Hacking Digital Democracy... and the History of Computerized Elections. (Part I)
1. Introduction
What makes electronic voting so unique?
The core truism of any competitive environment, from sports to business, is that any iron laws or codes of conduct and ethics can and will be breached at some time, at some place, by a competitor who deems it beneficial or, in a bout of despondency, necessary, to resort to such isolation and elimination of competition; this behavior can be expected to continue until the administrators of that competitive environment ascertain the nature of the cheat and mete forth proportionate and nullifying punishment, or establish structural blockades attenuating any net benefits extracted by anti-competitive behavior, whilst accelerating the cost of engagement.
The natural evolution of this truism brings attention to how it might unfold, and be quantified, with respect to electoral politics, wherein the benefits those who would so betray the public trust stand to reap is immense. The tactical repertoire that they might draw from is well-documented, from disinformation campaigns, subversive robocalls, flyers telling people to vote after the election, implementation of restrictive laws suppressing the vote, caging, gerrymandering, voter coercion, intimidation and bribery1 — some implementations become egregiously obvious if not for the general lack of legal infrastructure to combat such fraud.2 But that is besides the point of this article; the focal point of discussion regards how these actors might exploit the process of vote-counting itself, the, at present, heavily-computerized substrate of the democracy that confers into them their fortunes, and their tragedies. At the center of that discussion is what are the tools they have at their disposal to accomplish these ends?
For the greater part of the 20th century the most common way to cast and count votes was through the use of bulky, half-ton mechanical behemoths known as lever voting machines.

As the technological pinnacle of American democracy, for whose perennial status quo they dominated and represented, the common perception was that the era of lever voting would last forever. By 1964, two-thirds of the country lived in jurisdictions where votes were cast and counted by lever voting machines — the remaining third lived in areas where paper ballots were tabulated transparently and observably by hand. But, as it turned out, this era was temporary and would come to pass. By 1982 the stagnant duopoly of manufacturers responsible for developing and servicing these machines, the Automatic Voting Machine Corporation and Shoup Voting Machine Corporation, would cease their production and make forays into other technologies or get absorbed in the late-20th century concentration of the election market, but the voting machines themselves would remain staples of the democratic process until the early 2000s.3

The basic lever voting setup consists of a voting booth that secures voter privacy, equipped with a terminal with a display “ballot” laid out on its front. Candidates and parties would be listed in a tabular format, with candidate names on the row axis and party affiliations on the columnar axis, and a lever placed at the intersection of these axes. Voters would pull these levers and the counters installed on the backside of the front panel, which are not dissimilar to the odometer of a car, would record the cumulative tally of all votes cast for that candidate. Levers would have locking mechanisms that would prevent double voting or overvoting. Since the machines do not create records of each individual voter choice, recounts are impossible in the case of error or fraud,4 and the machines were difficult and expensive to test so jurisdictions generally enlisted the help of outsider technicians to perform those duties for them, meaning that, if somebody wished to buy an election all they would have to do is buy up support in those responsible for maintaining the equipment.5
The tactic du jour would be to send a technician to fix the vote counters, whose totals could not be independently adjudicated for a lack of voter-verifiable paper records or ballots, to display a given vote total. This could be done before Election Day in order to establish a vote 'floor' which is known to the attacker before a single vote has been cast and can plan accordingly. The attack might instead involve reducing the vote count for one candidate or issue by -x votes and increasing the votes for another option for the same contest by +x votes, keeping the vote totals the same and, in places where proper accounting measures are used to deter ballot box fraud, it would pass that measure and the election would be certified. Of course, that assumes that cooking the pollbooks isn't within the purview of the attackers.
This has the critical limitation that it, even in ideal conditions of absent oversight from county administration, requires the dispatch of a team of corrupt technicians to tamper with every individual machine, in every precinct in a county, and, if desired, across multiple counties or the whole state. The logistics of such an operation makes fixing statewide elections or even a presidential election next to impossible, and doing it secretly is unthinkable. Perhaps, if county elections are administered by insiders affiliated with that political machine or political party, then it would make sense, but, beyond county-level politics rigging lever voting machines makes little sense, except for cases where the outcome of a extraordinarily close statewide election can be manipulated by vote count rigging in a single, high-population county.
And then again, nothing about the setup of lever machines is electronic or digitized in any way; as the counters could not be infected with any type of brick-and-mortar ‘virus’, as anachronistic as that would be, set to tip the scales in favor of specific candidates or political issues, this cycling of technicians would have to be repeated before or after every election. That lever voting machines were manufactured by two duopolistic companies doesn’t really matter in this regard because elections are prepared at the county level, and as such, the absence of computerized components means that an insider at the assembly line cannot do anything to fix elections with said ‘virus’.
The other voting system was punch card voting.
Voters mark their choices on a paper “ballot” by punching out a rectangle of perforated chad next to one candidate for every contested office on the ballot through use of a tool as simple as a stylus or, most often, through the use of a ballot marking device, or punched card voting machine. The resultant hole is then counted as a vote by a electromechanical punched card tabulation machine, a standard card reader or, in some cases, a programmable digital computer, which became more common near the century’s close.

Stemming from an origin in textile manufacturing that was eventually spun off for uses in data processing and U.S. Census data collection and tabulation, the first practical example of a voting system that utilizes punched cards to record votes emerged with the Votomatic, developed from the IBM Port-A-Punch card punching device for voting by Joseph P. Harris and William Rouverol. The Votomatic was later acquired by IBM in 1965, before selling it off. Later Votomatic machines (including the one pictured) were made by Computer Election Services Inc. and several other IBM licencees. CESI was later absorbed into Election Systems & Software.
The Votomatic was a mechanical ballot marking device that translated voter intent into a vote on a physical, pre-scored punched card, containing a dense layout of voting positions accommodating complex ballots. The punch cards are not verifiable by voters for a lack of candidate nominal signage next to each hole, so it is impossible for a voter to know, unless if they have access to ballot design files for that jurisdictions, if their votes were punched properly. The other popular configuration is the Datavote card punching machine, which is combined with punch cards that do have such signage, though at greater cost to the jurisdiction.6
As they are cheaper, easier-to-maintain and less cumbersome than their counterparts, these technologies quickly overtook the archetypical lever voting machine in popularity and widespread usage by the 1980s, and dominated the scene of American voting until their failure in the 2000 presidential election lead to their retirement. They had the perks of leaving behind a voter-created audit trail, not unlike a paper ballot, that could be examined in the event of a recount of an audit, though the error rates of card punching machines was generally high enough that a detected discrepancy in a single precinct due to fraud or improperly punched chads would be nearly indistinguishable.7
As non-programmable mechanical devices any perpetrated frauds would, again, have to be done by technicians with physical access to the machines, except for the locations that tabulated them digitally. “Hacking” a punch card machine is technically more difficult than modifying the numbers on a lever voting machine.
A strategy would be to have certain choices pre-punched in order to create anomalous overvotes that would be spoiled during tabulation, or to misalign the cards so that a voter who punches votes for one candidate would accidentally punch a vote for the other. Misaligned punch cards can create improperly punched chads that are still attached to the cards at the seams, generating false undervotes. At its broadest scale, the only effective fraud that could be mustered was by delivering punch card machines that couldn't count votes to strongholds of the other party.
The votes that get reported can be manipulated at the punched card tabulator, as well.
The original Hollerith tabulating machine was a device used to process masses of punched cards for the U.S. Census in 1890 with spring-loaded metal pins embedded into the card reader that were pushed down upon the inserted cards, and if a hole was punched for a given option then the wire for that position could be suspended into liquid mercury, completing an electrical circuit which powers a electromagnet mechanism that increments counters that record the number of instances that particular position had been invoked as best describing the citizens theretofore included in the Census count.8
Under the assumption that the electromechanical punched card tabulator used after the fifties aren’t conceptually dissimilar from the Hollerith tabulating machine then it's conceivable that an engineer would map the counter recording punched votes for one candidate to another candidate and vice versa, effectively reversing the result for that machine. The same process must then be repeated for every such machine being shipped to the pertinent jurisdiction, implying that the engineer has the graces of the manufacturer.
This comes at great cost to the manufacturer and is not exactly flexible. A “fire and forget” dynamic, the rig would not be particularly useful in a volatile election environment. If a sudden pre-Election Day surge in support for the fixer’s favored candidate who was projected as the underdog by their pollsters results in them winning in the court of public opinion, then not only is the rig superfluous but also self-destructive, and there is nothing the fixer can do about that. The company will have no control over the vote flipping in future elections, and who benefits from the rigging.
The transition from the precinct-count configuration to the central processing of voted “ballots” still made vote rigging far easier to do manually, since the vote data recorded by the tabulator's counters can be manually manipulated after the election like a lever voting machine, but counties would only have one punched card tabulator as opposed to dozens of hundreds of lever voting machines for each polling place.
Nonetheless, both of these voting types are still quite decentralized and hard to penetrate on a scale that extends beyond the utility of local political bosses. The fraud of old could only clearly serve the purpose of swaying the tide of close elections9 or ones far enough down the ballot that the predicted electorate would exceed no more than a few thousand votes, padding the vote in partisan fiefdoms, or perhaps as indemnification or a display of loyalty to political patronage. Electoral fraud was a egalitarian free-for-all and produced a net wash because vote rigging would not strictly favor any party over the other and could not effectively be executed at a national scale, with the exception of good-old fashioned voter suppression.
It is from the development and speciation of these technologies that electronic voting emerges. Direct record electronic voting machines are quite straightforward, consisting of a touchscreen interface which voters use to electronically submit votes, which they will cast after reviewing their selections on the screen.
Optical mark-sense scanning, or optical scanning, was developed as an alternative to IBM's electrical system. IBM had explored optical mark sensing in years earlier, but Professor E. F. Lindquist of the University of Iowa developed the ACT exam and directed the development of the first practical optical mark-sense test scoring machines in the mid 1950s. The rights to this technology were sold to the Westinghouse Learning Corporation in 1968, and Robert J. Urosevich of the Klopp Printing Company presided over the trialling of this tech for the scanning of voter-marked ballots in 1974. Urosevich’s company, Data Mark Systems, would ultimately license the tech after it was abandoned by Westinghouse.
The very first mark-sense scanners used for grading papers detected graphite pencil marks or insulating ink made on conductive stationery by sensing the slight difference in electric conductivity of the two media. Mark-sense ballot scanners, such as the Votronic Corporation ballot scanner that dominated during the late sixties and early seventies, to modern optical scanners, use light-emitting diodes and photosensors to scan votes filled in by voters using non-reflective ink.10
The ballot would be illuminated by the diode, whose light would be absorbed by the ink, and the ‘gap’ would be interpreted as a vote by the scanner. The vote data would be logged into an electronic storage medium such as a memory card. Optical scanners can be used in a central-count, batch-fed configuration, similar to the punch card tabulators, which is often used to process large quantities of absentee ballots though some areas use it to aggregate in-person ballots, too, or precinct-count configuration, used chiefly to count in-person ballots cast on Election Day or during early voting.
The processing of ballots and punched cards for these two devices is coordinated centrally by a programmable memory card or control card. The code on these removable electronic storage media, the former of which are small enough to fit on the tip of your finger, store vote-counting logic, records of votes cast and counted by the machines, audit logs, and so forth. With mechanical voting systems and punched cards counted by electromechanical tabulators, changing thousands of votes takes much material effort to execute. Changing numbers on a memory card takes seconds. Additionally, they can be programmed with malicious counting logic that reacts semi-intelligently to variables supplied over the course of an election. If the desired candidate is winning the real count, then nothing is done, and if they are trailing, the code can add votes to their running total, whilst subtracting votes from their adversar(ies)y’s totals, until the desired candidate eclipses them and achieves a commanding plurality.
Provided that the yet-still gestating Internet would not escape its infancy until the late eighties, these computers would not be networked and thus vulnerable to very much outsider interference. Rather, the worry was that a corporate insider, with unfettered access to the manufacture and programming of these devices, can install undetectable malware into the memory of the computers that manipulates vote data stored invisibly as abstracted numbers on a memory card, unseen by a human being, and unilaterally perpetrate fraud at an unprecedented scale without much risk of being detected. All they would need is a political or financial interest to motivate them to commit these crimes, and the will to stomach it.
The principal practical vulnerability of the digital age is invisibility. The internal processes and events of computer programs are not liable to be subject to any kind of oversight or observation by all but a few highly-educated and technical-savvy users. Checking the windows and locking the doors is not possible — yet still, it remains implausible to design a perfectly secure computer, and they are still exceptionally vulnerable to fraud and theft.
Thus, it is with these digital, programmable, computerized voting systems that the fears that they could be used to propagate election fraud at a unprecedented scale and irrecoverable error began to take shape. First, it was the digital punched card tabulators that jurisdictions began to adopt during the seventies and eighties that received much of the attention.1112
The company at the center of everyone’s attention was also the largest; Computer Election Systems, Incorporated of Berkeley, California. Contracting out to over 1,000 county- and municipal-level jurisdictional governments by the mid-eighties, it was accused by many politicians running for elected office of facilitating vote fraud across the states of Indiana and West Virginia, which, naturally, its president, John H. Kemp denied, though while conceding that designing a fraud-proof system is infeasible or even impossible.13
In West Virginia, three-term Charleston mayor John Hutchinson charged that several Kanawha County election officials and Computer Election representatives successfully conspired to deprive him of his re-election in November 1980, citing pre-election polls that showed him winning overwhelming there despite the recorded loss.14
In Dallas, Terry Elkins, the campaign manager for Max Goldblatt, who in 1985 ran for mayor, came to believe, on the basis of a months-long study of the surviving records and materials of the election, that Goldblatt had been kept out of a runoff by manipulation of the computerized voting system. Impressed by the charges, the attorney general of Texas, Jim Mattox, conducted an official investigation of them.15
Whether these allegations of fraud could be proven, and if they were based in reality and not cynical politics, is besides the core point; the specific allegation that was corroborated by the testimony of multiple experts and computer scientists was that these systems were insecure and ripe for fraud. Howard Jay Strauss, the associate director of the Princeton University Computer Center, who formerly worked at Bell Laboratories, the National Aeronautics and Space Administration and the RCA Corporation, had confirmed that the program used to count Indiana votes was vulnerable to manipulation. An attacker could punch bogus votes into the punched cards, or control how they are counted by the tabulators, whilst purging audit log evidence of their intrusion.16
The New York Times also sought the counsel of Eric K. Clemons, an associate professor of decision sciences at the Wharton School of the University of Pennsylvania, who backed up those claims.17
For a technology so new, few states had adopted coherent standards and guidelines that the computerized election systems would be accordingly tested and certified against in order to ensure their security, reliability and accountability. The state of California’s chief voting system certification consultant, Robert J. Naegele, who had been hired by the Federal Election Commission in 1987 to draft the basis of the voluntary federal recommendations and standards for the certification and adoption of electronic voting machines and tabulators, portions of which stand to this day,18 stated in ‘88 that “when we first started looking at this issue, back in the middle seventies, we found there were a lot of these systems that were vulnerable to fraud and out-and-out error.”19
And as such, the course of electoral democracy becomes their’s to lose. A single programmer, or a small group of motivated, technically-skilled conspirators, now has the ability to perpetrate fraud at a massive, unprecedented scale, with any impedance originating from the sole limiting factor of the market dominance of the company that the programmer works for or whose vulnerabilities they are exploiting. When monopolies in the election market begin to coalesce, the business of election rigging itself becomes a monopoly, the sole domain of whomever the company has set its sights upon.
The election market of the eighties was, however, not yet centralized and monopolized. Without that, such insider fraud would be restricted to a smaller scale — not as localized as the fraud of old, but not quite enough to tip the scales at a national level, except for in the narrowest elections, determined by a handful of state and fractions of the total vote.
The earliest systems were built by an ecosystem of numerous small and relatively localized mom-and-pop election vendors operating in a healthy, competitive market, that generally persisted in their own parochial niches and supplied counties with supplies and vote counting equipment. The very first direct recording electronic system to be sold for real world election use was the touchscreen Video Voter, developed McKay, Ziebold, Kirby and Hetzel in 1974 (U.S. Patent 3,793,505)20 and marketed by the Frank Thornber Company, which was deployed for use in 1975 in Woodstock and Streamwood, Illinois, before other counties in the state bought and used them over the course of the following years. Then there was Western Data Services Inc., a firm that provided on-line computer services to several hundred county and municipal governments, school districts and other governmental agencies in Texas.
This framework would be dissolved in a frenzy of acquisitions and mergers by the nineties, wherein the great majority of them had been subsumed into the corporation that would eventually be incorporated into what would become known as ES&S. During the mid-eighties and nineties, the Business Records Corporation of Dallas, Texas, the sole and wholly-owned subsidiary of Cronus Industries, embarked on an expedition to corner the market.21
In July, 1984, BRC began its expansion with the acquisition of Data Management Associates of Colorado Springs and the C. Edwin Hultman Company, before moving to absorb Western Data Services Incorporated of Texas, Roberts & Son Inc. of Birmingham, Alabama, and Frank Thornber Co. of Illinois. By the end of 1985, Cronus Industries had finalized its purchase of Computer Election Systems, Inc., and in the months following BRC had further acquired Integrated Micro Systems Inc. of Rockford, Illinois, and merged with Computer Concepts & Services, Inc. of St. Cloud, Minnesota in 1986, and subsumed Sun Belt Press Inc. of Alabama and Minneapolis-based Miller/Davis Company.
The result of the acquisition blitz was to eliminate most competition, with the exception of a few large companies, and to operate virtual vote-counting monopolies in numerous states. They sold election services to the nation’s largest cities, in Los Angeles, Chicago, Detroit, Houston, Phoenix, Miami, Seattle, Minneapolis, Cincinnati, and Cleveland by 1988.22
Eventually, Cronus Industries would pivot its focus to healthcare consulting, and in 1997, American Information Systems, based in Nebraska, would come to seek the acquisition of BRC’s assets, after which it was reincorporated as ES&S.23 The Securities and Exchange Commission objected on antitrust grounds, and a deal was made in which the assets of BRC were shared between ES&S and another voting company, the burgeoning, California-based Sequoia Voting Systems.24 It is these two, together with two other corporations, Diebold Election Systems and Hart InterCivic, that embodied the election market at the dawn of the new century.
The transition to optical scanning systems and DREs began in the early nineties as the technology came to maturity and the promise for faster accounting and reporting of large amounts of votes was actualized, although they did not truly become common until the end of the century. After the voting debacle of the November 2000 presidential election in Florida, caused by thousands of lost votes due to card punching machines and unaligned ballot cards engendering hosts of ballots where voter intent could not be discerned by man or machine, election administrators and officials were neither ready nor willing to bear the brunt of the chaos — asymmetric recounts, vicious litigation, protests and riots — should such a scenario reach their jurisdiction, so they turned to the various electronic voting vendors for replace their aging equipment with newer, modern vote-counting computers, who proceeded to ruthlessly exploit the panic to force through their sales.
The old mechanical and punch card voting systems quickly collapsed in utilization as purely digitized voting became the mainstay of the 21st century. Direct recording electronic devices, once an obscure technology with limited market penetration which gradually grew through the nineties, swelled from less than 15% by 2000 to nearly 40% by 2006. Optical scanners, which had been displacing card punching machines and lever voting machines for a decade at that point, grew from 30% market share to over 40% in the same timeframe.25
The transition to all-electronic voting was supercharged, however, by the passage of the Help America Vote Act,26 which was signed into law on October 26th, 2002. Drafted in response to those voting failures and the resultant crisis of confidence in the administration of democracy, most important of its provisions was the order to phase out mechanical voting systems, and the disbursement of federal funds to jurisdictions across the country to replace these systems with advanced electronic voting machines or optical scanning systems, which were promised to make voting easier, faster, more reliable, and preclude the administrative debacles of the past. Beforehand, electronic voting systems were used by no more than 40% of registered voters in the country — including punch card counties, 55%. Afterwards, that quickly expanded to >99% by the top of the decade.
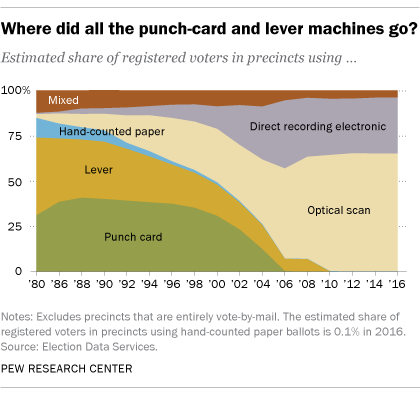
Lost, though, in the stampede to modernize, were the repeated demonstrations of insecurity and unsecurability. Over the course of the 21st century, from the beginning onto 2023, studies commissioned or contracted to computer scientists at the University of Princeton,272829 the University of California,30313233 the University of Pennsylvania,34 the Florida State University,35 Johns Hopkins and Rice Universities,36 the University of Connecticut,37 the U.S. Department of Energy's Argonne National Laboratory,38 cybersecurity contractors such as Virginia's Science Applications International Corporation39 and Michigan’s Compuware Corporation,40 and others4142434445 have served to expound upon the flaws and inherent absence of insurance pertaining to the security and privacy of vote casting and tabulation through these digital means, both in a laboratory and practical setting. They expose, both for systems in the United States and abroad, a distinct vulnerability to illegal and/or unauthorized interference, which, in any case, can be propagated by a single individual with physical access to a single machine in a given jurisdiction.
There was a difference between the election computer fraud of the eighties and that of the 2000s — these computers are heavily networked, paving the way for outsider threats as much as insider threats.
Network-based attacks can be mounted by outsiders by exploiting a crucial process in the preparation of elections: unlike lever voting machines precinct-count electronic voting systems and optical scanners have to be programmed centrally by copying election definitions into the memory of the machines, which are read by memory cards to facilitate the display of electronic ballots onto the glass screens of direct recording electronic machines, and to direct the process of discern deliberative intent from voter markings on ballot sheets. These election definitions are prepared by poll workers or election subcontractors at election management systems (EMS) in the central county election office, which most-often manifest as general-purpose workstations running commercial operating systems such as Windows or Linux. The definitions are generated and then copied onto removable electronic media, and dispatched to every voting machine in the county before they are sent to their designated precincts before voting begins. Alternatively, they are copied to voting machines via a LAN.
Ballot definition files can be modified to deliver a malware payload to the precinct voting equipment, or malware can be directly copied onto the electronic storage device and onto the voting machine, effectively jumping over the air-gap. Conversely, because of the programming process, infecting a single voting machine with malware provides the opportunity for it to infect the EMS via memory card, and subsequently all other precinct-level devices in the county — a single individual with temporary access to a single voting machine can compromise the entire election system of counties ranging from Loving County, Texas to all 22,000 such machines in Los Angeles County, California. The election management systems themselves are sometimes connected directly to the Internet; provided the equivocations of county election officials the extent to which is unclear, though such connectivity arrangements have been observed for months or years on end, without, allegedly, the knowledge of those officials. This provides a pathway for outsiders to remotely infiltrate county-level election networks and compromise voting software and election results, as well as future machine-aided recounts and audits, by modifying the election definition files to harbor malicious executables, which are transferred to voting machines.464748
The “secret”, that officials within all echelons of government, and vendors, often hate to admit,49 is that precinct voting machines are capable of connecting to the Internet, through modems or WIFI-capable memory cards, and have been for decades, sometimes without their knowledge. Cellular modems that can communicate with central election offices,50 have been used in voting machines and precinct optical scan tabulators to transmit (usually) unofficial results to the central EMS for aggregation and reporting for decades. It was, and probably still is (though it most likely wouldn’t make an inkling of a difference if it was not) the case that ES&S DS200 optical scanners equipped with networking cellular modems were in use across eleven states, numbering in the tens of thousands by some, admittedly napkin estimates. Hart InterCivic, similarly, admitted to selling 1,300 such Internet-capable tabulators in eleven counties in Michigan.5152
Because computers cannot be secured, it is up to election officials to implement comprehensive defenses against potential election tampering in all its forms. This includes devising certification standards and efficacious testing protocols to prevent insider-fraud, and effective post-election auditing or recount procedures in order to deter fraud which the chance that a hacker could be caught, thereby escalating the cost of hacking an election whilst decreasing the maximum gain one can extract by doing so.
The point of this article, then, is to examine the procedures in place and appraise their real value for achieving these ends, or to deconstruct them.
2. A “Brief” Description of the Election Market
“There is no reason to trust insiders in the election industry any more than in other industries, such as gambling, where sophisticated insider fraud has occurred despite extraordinary measures to prevent it.” — Report of the Carter-Baker Commission on Federal Election Reform (2005)53
A degree of certainty is enforced, in part, by the notion that, because our elections are administered over equipment supplied by a “broad” array of vendors, they evoke a sense of “decentralization” such that compromising every election system would be technically complex and orchestrating a manufacturer-side subversion scheme impossible.54 Perhaps in the eighties, this would’ve been true.
Of course, this is not the eighties. Technically the mores of election administration are decentralized in the sense that there are a lot of counties subdivided into a lot of townships, each with their own election officials, administrators, judges et al. This, critically, only serves to make election adjudication even more difficult in the case of a successful attack or other procedural error and only represents a roadblock for hackers, particularly of the state-backed kind. It is, rather, a boon for corporate insiders,55 however, since ballot design and voting machine programming is highly specific to a given jurisdiction due to local races like for mayorship, school board, water retention services and so forth. This means that the programmer will necessarily know the location that every memory card and every ballot definition file will be sent to will extreme precision, allowing for demographic-based attacks if they are desirable or necessary.
By contrast, the elections market, crucially, is not decentralized. At present, the market of vendors is highly centralized and concentrated into a tight oligopoly of three companies, each with various political agendas and tribulations unto themselves: the Omaha, Nebraska-based, Election Systems & Software, the Toronto, Ontario-based Dominion Voting Systems, and Austin, Texas-based Hart Intercivic. Combined, their voting equipment services north of 88% of registered voters across the country, with the remainder being handled by a smaller carnival of vendors with a none-too-much better track record, as we will see shortly, at least in the respect that anyone has done any research on them.56
The politics of bidding for jurisdictional contracts is a complex process but more often then not transpires in a way not dissimilar to a racket; a common observation in the world of election administration is that election officials, well-intentioned as the median individual might very well be, are, lacking in the requisite technical expertise, largely in the dark about the inner workings of the various black box voting systems and usually resign to the explanatory caprices and hail of fact-averse marketing pitch proudly spread by amoral election vendors unconcerned with actual (i.e. not because nothing better exists) customer satisfaction. Such naivety ends up getting exploited in the world of election market hegemonies and corporate gangsterism, where honesty is a deadweight, the lengths of which these contractors will consider necessary to maintain their gaping share of the market can be quite egregious: lobbying, extortion, deception and even outright bribery.
Voting machine vendors will utilize the tools disposed to them to command the unfailing allegiance of the officials charged with the drafting of legislation and election management functions on the county or state level, first with undermining the very structure of U.S. elections and establishing an inescapable codependency between themselves and the administrators that have made the grave error of contracting out to them.
The prime example of this dynamic was provided in Angelina County, Texas, just before the 200857 presidential general election cycle; the county depended on ES&S to provide and deploy election equipment and supplies, design paper ballots, pre-marking ballots for pre-election testing, the programming of iVotronic voting machines, service the voting machines designated as accessible for disabled voters with audio functions, burning memory cards, electronic vote cartridges and flash drives for the M100 ballot scanners and iVotronics, set-up the Election Night vote reporting manager program, and administer Election Day support, retrieve results and report outcomes. This all gave the contractor considerable sway to extort the county administrators into signing agreements to clean up ES&S’s own election reporting mess, by recounting ballots using the very reporting manager program serviced, at an expensive price, by ES&S. If the county did not then the company could simply withhold support and let future elections collapse. Testimony and documents from many other counties across the country demonstrated that this dynamic was fairly common.58
Among HAVA’s mandates is the requirement for at least one ADA-accessible voting device per precinct or polling place, but New York, which was still using its antiquated (and quite effective and hard to hack) mechanical, lever voting machines, missed the federally-mandated deadline. As a result, by January 2008 U.S. District Judge Gary L. Sharpe granted a motion to enforce and ordered counties to deploy at least one ballot marking devices for disabled voters by the September primaries. With only eight months to comply with the court order, Nassau County, along dozens of other counties, contracted out to Sequoia Voting Systems59 for hundreds of its ImageCast optical scanner/BMD hybrid voting machines, effectively indenturing itself to its whims. By June 26th, the county had received 156 of its ordered machines, yet 85% of them were rendered unusable by printer failures, USB problems, battery drain, no responsive keypads, physical damage, and so forth. Similar failures were reported by other counties across the state, yet Sequoia took its sweet time fixing them, and, months afterwards their diagnostic functions were still out of order.60
Hawaii was another example of a state whose elections were virtually entirely privatized by corporate vendors. In the early 2000s ES&S and Hart InterCivic handled everything, from election programming, ballot design and all technical work. Volunteers administered elections on the precinct-level, but after the polls were shuttered on Election Night and the memory cards were removed from precinct voting machines they were handed off to corporate technicians and the vendors handled tabulation and vote reporting. This led to problems such as machines reading votes for Green Party candidates despite the fact that they ran no candidates for the affected races, or election officials having to revise turnout estimates because the vendors calculated them differently from one another.61
By 2008, Hawaii had awarded a contract to Hart InterCivic that gave them a complete monopoly over the state’s elections, which ES&S challenged on the basis that Hart's bid was unreasonably pricy, automatically triggering a stay on the contract.62 Eventually, the contract went through when Craig Uyehara, an administrative hearings officer for the state Department of Commerce and Consumer Affairs, ruled that, while the contract was awarded in bad faith, it was too late to renege it, lest the 2008 primary elections and onward be thrown into jeopardy.63 The state was so dependent upon corporate support that it believed that upholding an invalid contract was necessary to run elections. Hart InterCivic still runs Hawaii's elections to this day.
Election programming is a process repeated, necessarily, for every election and is not subject to any sort of testing or oversight by federally-accredited or state-level agencies. However, since most counties, mainly rural, though some larger urban counties exempt this rule of thumb, lack the fiscal resources, and therefore qualified staff and technical experience to maintain the electronic voting equipment that run their elections, this process is often contracted out right back to the vendors themselves, or subcontractors.64 The concentration of this programming into the hands of the vendors has lead to dozens of reported cases of the results of elections being reversed and victory misattributed to the wrong candidate65 — and these are only cases detected by officials. If ballot programming errors mapped, for example, Democratic votes to Republican votes and Republican votes to Democratic votes for a single race then, perhaps, the mismatch of the results of that race compared to other partisan-contested races would make the programming errors obvious, but if the misattribution of votes applies to all candidates in all races, then it would not be so obvious. Nevertheless, hundreds of jurisdictions still continue to pay these vendors to program their ballots despite the many observed flaws, and outright incompetence.
A major component driving these dependencies is the fact that the laws of some states statutorily impel, either explicitly or implicitly, election officials to acquire equipment or fulfill requirements that can only be fulfilled and supplied by vendors, no matter how flawed their operations are. These provisions corner officials into purchasing from inveterate and often security/consumer satisfaction-agnostic corporations, rather than establishing independent voting systems with the guidance of seasoned cybersecurity experts. Many states require that counties purchase from companies that have their equipment certified by the two federally-accredited test authorities, which sounds good on paper, but, due to the extravagant contract pricings they charge for their compliance testing only well-established vendors can afford, which has the dual-effect of accelerating reliance on large vendor corporations, and introduces market barriers for smaller competition.66
Because of the legal setups forcing counties to bargain for often-failed and insecure voting systems from untrustworthy vendors, the general, unspoken rule of the election industry is that, once you bought it, you keep it. Sometimes this rule is summarized honestly by vendors. Internal emails authored by Ken Clark, Principle Engineer of Diebold Election Systems,67 and later leaked and made publicly available on the Internet, read that “there is an important point that seems to be missed by all these articles: they already bought the system. At this point they are just closing the barn door. Let’s just hope that as a company we are smart enough to charge out the yin if they try to change the rules now and legislate voter receipts.”.68
When asked to clarify the meaning of “out the yin”, Clark wrote further: “Short for ‘out the yin-yang’. ...Any after-sale changes should be prohibitively expensive. Much more expensive than, for example, a university research grant.”69
In accordance to this iron law, ES&S began gouging the costs of maintaining the (often-failed and unreliable) election systems it doled out to contracting counties. In Webster County, Iowa, the budget set aside for election operations expanded from $49,000 to $110,700 for only 25,300 registered voters across twenty-five precincts over the course of two years from 2005 to 2007. The vast majority of this cost came from extortionate ES&S maintenance fees for the county's new Model 100 ballot scanners and AutoMARK electronic voting machines.70
The standard-issue corporate greed was varnished with a dash of ambition, too, since the contractors working for Sequoia Voting Systems were allegedly ordered, despite any ethical qualms they may wish to bring to bear, to deliberately supply counties in Florida with substandard punch card ballot paper that didn’t punch properly, manufactured at a paper mill with zero experience printing punch card papers, ahead of the 2000 general election with the knowledge and sanction of the company’s management. The company even modified the specs of paper punch cards sold to Palm Beach County, leading to piles of undervotes and improperly punched chads, an action which very effectively spurred a crisis after the election that discredited punch card voting, and drove the country’s transition to all-electronic voting, a dynamic which is, evidently, quite good for business.7172
The programming of voting equipment is considered to be proprietary, subject to fiercely guarded property rights, a dynamic where the code is known only to the corporate programmer and no-one else, except for perhaps an “independent (in name only) testing authority” that inspects the code, and a lucky few independent researchers.
The excuse is that open-source programming would ultimately be harmful to the security of the system by revealing the inner-workings of the system to potentially malicious outsiders, a principle known as security in obscurity, despite the cybersecurity community’s virtual unanimity regarding the inefficacy of obscurity as a useful security solution73 because hackers can still acquire the source code through extralegal means, or insiders can perform drill-downs into the code, and now knowledge of vulnerability is privatized and unlikely to be patched on a timely, meaningful basis.
Of course, the idea that these vendors actually care about security has been found in the breach on many occasions.
An example is given in 2003 when a small team of researchers from Johns Hopkins and Rice University analyzed only the unencrypted portions of the source code repository for the Diebold AccuVote TS voting machine that was discovered on an unsecured company FTP Internet server by voting activist Beverly Harris earlier that year,74 and found that it was easy to generate fraudulent smart cards that could be used to allow voters to submit multiple votes, obtain administrator privileges and review partial results and shut down the election early, vote totals aren't encrypted when transmitted to the count election office, meaning that they can be intercepted in a man-in-the-middle attack if transmitted by phone line or over the Internet and manipulated, and whenever cryptography is used it's used incompetently. Diebold disregarded the findings of the study, claiming they are not reflective of the protocols of a real election. Afterwards, Maryland, whose board of elections had been considering finalizing the purchase of Diebold touchscreens, contracted out to the Science Applications International Corporation, whose report largely confirmed most of the findings of the Johns Hopkins/Rice study.75 Diebold spun both studies as confirming the integrity of its systems76 and that any and all problems stem from management issues (“human error”), which the state Board of Elections accepted.
Another study, also commissioned by Maryland, out to the company RABA Technologies,77 again confirmed the findings of the previous two studies, this time in a simulated election environment inspired by the state’s election administration, netting the AccuVote-TS a failing grade.78 Still, Diebold managed to spin this too.79
Security analysis conducted three years later revealed that most all of the vulnerabilities discovered before and during the Maryland certification process had not been addressed by Diebold at all; if anything they were more numerous than before.80
The deceit culminated in October, 2006, when a disk containing a certified copy of the Diebold BallotStation program and Global Election Management Software (GEMS) database source code used to tally votes was possibly stolen, which Diebold denied, and then apologetically claimed that, even if it were real (it was) it would take a “knowledgeable scientist years to break the encryption”. BallotStation source code was found not to be encrypted in the least.81
Diebold, at this point infamous for its negligence — among the cybersecurity and election integrity community, not election admins, who continued to contract out to the company until its insolvency, mostly because they were never alerted by the “information clearinghouse” Election Assistance Commission — enlisted its lying spokesman to besmirch the findings of the UC Berkeley Top-to-Bottom review commissioned by California Secretary of State Debra Bowen as having unrealistic access to company-provided source code, and that existent “checks and balances” prevented the hacks from occurring in real life.82 Not only did the Red Team Top-to-Bottom review83 explicitly not have access to the system's source code,84 but the “complete and unlimited access” assumed (fallaciously) to be required to hack a voting system is already available to Diebold insiders and poll workers. The ultimate example of this was that, in 2007, sitting out in the open, in the cold, unsupervised darkness of the company's warehouse in Allen, Texas, were stacks upon stacks of optical scanning systems which were easily hackable and accessible to all sorts of insiders and burglars, who could infect the devices with malware, undetected, and they'll still be shipped out to the counties as though nothing was amiss.85
In Ohio, a former high-level technician of Hart InterCivic by the name of William Singer filed a Qui Tam false marketing lawsuit on behalf of the federal government in 2007 alleging that the company deceived both the government and county customers about its eSlate voting machine in order to pony up a slice of the $3.9 billion HAVA appropriations pie and win contracts. Activities that the company variously engaged in in order to illicitly acquire those funds include routinely failing to properly test its voting equipment (botched alpha tests and zero beta tests to catch “major” and “minor” flaws respectively), deliberately avoiding the process of properly certifying its eSlate voting machines by the submission of unmarketed dummy voting machines that voting system test labs would “certify” for use in Ohio, then substitute it for the real, uncertified product upon delivery, hand fabricating election abstract reports that the eSlate system could not produce and submitting to the Ohio Secretary of State in order to acquire state certification, submission of false reports to InfoSentry during its state of Ohio commissioned examination of voting systems86 to give the false impression that Hart provisions for disaster plans and security audits, lying about the lack of voting system capacity to store vote data truly randomly (only pseudo-randomly) allowing insiders to breach ballot secrecy with reasonable certainty as to how voters voted, issuing software patches to some of its eSlate voting systems but not others whilst not alerting anyone about it after Singer discovered that the audit logging function for the Ballot Organization Software System used to create and design ballots produced invalid entries and was rendered useless, falsely marketing the M2B3 memory card reader as being faster and less prone to data corruption than previous card readers it sold, and so forth.878889
In the aftermath of a purported failure of their AVC touchscreen voting machines in the 2008 New Jersey primaries,90 Sequoia spent its sweet time drafting press releases ballyhooing its dedication to third-party reviews of its equipment whilst simultaneously threatening Princeton scientists with legal retribution if they took a crack at their “tamper-proof” easily hackable voting systems.91
Instead, its Vice-President of Compliance, Quality and Certification, Edwin B. Smith III, kicked the buck over to the completely unknown Kwaidan Consulting Services supposedly based in Houston, which had no website and was a one-man operation headed by a figure of questionable character who used to work at the company that became Suntron, which manufactured Hart’s troubled eSlates.9293 Perhaps there is no correlation between Suntron and Sequoia, but provided Ed Smith’s former employ at Hart InterCivic that hope is unlikely.
When maverick election officials take the responsibility of ensuring the integrity of the technology of democracy into their own hands they often find themselves at the receiving end of an assault by election vendors and their vanguards implying that there would be hell to pay for their transgressions. Such was the case of Ion Sancho, Supervisor of Elections in Leon County, Florida, who in 2005 invited BlackBoxVoting activists and researchers examine the certified Diebold voting equipment and demonstrate their insecurity for the Hacking Democracy documentary,94 afterwards vowing not to use their equipment again,95 and, after a predictable litany of lies and threats from Diebold,96 thus was quickly rendered a persona non grata by, in the collective, both the tripartite slate of corporate vendors authorized to sell in Florida, and public officials snaking all the way up the governmental pyramid up to the Secretary of State and the Governor of Florida themselves for the fallout of those company’s actions.97
After initially agreeing to enter a contract with the county after the county council voted to disavow Diebold’s equipment, ES&S ultimately spurned their attempted acquisition on the basis that they could not fulfill equipment deadlines and had to restrict themselves to serving long-time customers.98 The fictitiousness of this excuse is demonstrated by ES&S agreeing to deploy AutoMARK touchscreen electronic ballot marking devices that create a paper trail elsewhere, after the Leon County request, once the council of Volusia County voted 4-3 to abandon its Diebold equipment.99 Similarly, an attempt to reach out to the remaining state-qualified vendor, Sequoia, ended in failure when an arrangement established between the county and a local representative was overruled by the corporation’s CEO, who asserted that the company would not be accepting any more contracts for 2006 due to being at maximum capacity.100101
For their flaws, voting systems and modifications are tested and certified by federally-accredited testing labs and state commissioned testing authorities in order to ensure their compliance with certain standards designed to preclude the worst of the above — theoretically, anyways, but sometimes election vendors simply flaunt the law outright.
On November 10th, 2003 an audit conducted by the California Voting Systems and Procedures Panel of Diebold voting systems used in seventeen counties discovered that, in all seventeen counties, Diebold had engaged in unauthorized installations of software patches that were not certified by the state, and in three of its client counties the patches weren’t federally-certified, either. These patches were in use for at least three years. They failed to notify the Secretary of State of California of its proposed system modifications and admitted that it’s deployment of software without obtaining certification ran contrary to state and federal law.102103 SoS Kevin Shelley decertified and banned the use of the Diebold AccuVote TSx touchscreen voting systems104 (though his successor recertified them), and called upon the State Attorney General, Bill Lockyer, to pursue criminal charges for fraud against the vendor; however, he declined, and instead sought to pursue a monetary false claims judgement, which he, alongside BlackBoxVoting activists, won.105 But the fine was insignificant next to the profits Diebold made from selling the uncertified systems to counties, meaning no true consequences for breaking the law were resultant of the suit.
Indeed, in January of 2002 Diebold's Principal Engineer Ken Clark penned in a memo that “Strictly adhering to our release policies, the California change should also require a major version number bump to GEMS (because of the protocol change). We can't reasonably expect all of California to upgrade to 1.18 this late in the game though, so we'll slip the change into GEMS 1.17.21 and declare this a bug rather than a new feature. What good are rules unless you can bend them now and again.”.106
The story repeated itself again in late 2007 when the state of California attempted to subpoena ES&S voting system source code as a part of the state sanctioned UC Berkeley Top-to-Bottom review of electronic voting system security. ES&S initially ignored SoS Bowen’s demands for them to cede the source code for their InkaVote Plus voting system used in Los Angeles County,107 at the time, only — curiously — surrendering when she motioned for Iron Mountain, the company holding the originally certified source code in escrow, to release it to the state; indeed, ES&S lobbied for the state to only inspect the code that they gave them, not the certified code held in escrow, and for Bowen to withdraw her request to review it.108 It was, given the company’s dilatorialness, far too late for the source code to be subject to the Top-to-Bottom review, however, as it happened, it was immediately obvious that, just as with the Diebold AccuVote TSx source code, the version number for the deployed InkaVote Plus machines did not match that of the source code held in escrow, either suggesting a typographical error or an unauthorized modification to the voting system firmware.109 Given its unwillingness to let the state examine the escrowed source code, it’s most likely the latter, and use of the InkaVote Plus in Los Angeles County was suspended shortly thereafter.110
Additionally, about a month later the state discovered that ES&S had violated California Elections Code § 19213 by illegally deploying for use in polling places across multiple counties 1,000 units, costing taxpayers $5 million, of an uncertified and unauthorized version of the AutoMARK ballot marking device model that have been modified from a version previously approved for use by the SoS, without alerting the SoS and confirming that the modifications do not materially impair the performance or accuracy of the system. The systems weren’t even certified federally.111112
Even minor voting companies are in on the art of steal. MicroVote General Corporation113 was ordered to pay nearly $400,000 to the state of Indiana in civil penalties after they came under investigation negotiating hundreds of thousands of dollars in sales contracts with ten Indiana counties to deliver and service completely uncertified voting systems.114
As a semi-related addendum, as I'm not quite sure that this is expressedly illegal (though it certainly is extremely unethical), but there was a design flaw involving incompatible tolerances for the motherboards115 of 4,700 Diebold touchscreen voting systems across four counties in Maryland (Allegany, Dorchester, Montgomery, and Prince George) that led to unresponsive screen failures during voting in 2004, resulting in the manufacturer quietly recalling the boards and replacing them over the months. Oh, and they did not properly inform the Maryland State Board of Elections about this; indeed, they deceived them in a July 12th, 2005 interview, claiming that the upgrades would bring the devices up to date with the specifications of newer units, whilst omitting mention of the motherboard changes. They only thought to exhibit candor with Diebold apologist Linda Lamone, the director of the board.116
The saga of uncertified equipment or software patches does not, however, stop there. The federal Election Assistance Commission is theoretically charged with the regulatory authority and prerogative to revoke certifications from and otherwise punish voting machines manufacturers for running afoul the law, but history has shown the agency to be both feckless, impotent and captured by those very vendor corporations to effectively regulate them.
There is a certain amount of trust, or, more sneeringly, faith, involved in the business of electronic voting that is due between officials and voters, and the companies responsible, in part or in whole, for administering statewide elections. We have seen that trust broken and betrayed on many occasions, but perhaps, that is simply inherent to the companies themselves and the private equity that controls them, and the nature of those they employ to deliver on their promises.
The roster of employees at Global Election Systems117 included ex-felon Jeffrey W. Dean, a former tech consultant for the large Seattle law firm Culp, Guterson and & Grader, who was convicted in the 90s for the highly sophisticated computer-aided embezzlement of $465,341 from said firm and the digitized alteration of financial records, who served as the senior vice president of Global after 2000 and then made head of research and development with full, unfettered access to all components of their voting system, which was used in Washington, Florida and elsewhere.118119 Diebold denied enlisting him after its acquisition of Global, but depositional records demonstrate that he returned as a consultant in mid 2002.120
Meanwhile, convicted cocaine trafficker John L. Elder worked for Global's and Diebold's ballot printing and absentee ballots handling divisions.121
Then there are the companies that program the voting machines when the vendors themselves aren't charged with such activities. These election subcontractors handle programming, servicing voting equipment, results reporting, and even acceptance testing for the jurisdictions, and constitute a clique of shadier, less known, even more centralized and sometimes equally unreliable and/or partisan outfits such as Triad Governmental Systems Incorporated,122 responsible for election support before, during and after voting in seventy-three Ohio counties, Command Central,123 based in an indistinct storefront in St. Cloud, Minnesota and which performs programming for 2,000 jurisdictions across thirty-four states,124 LHS Associates125 of New England, and, formerly, the non-corporate Center for Election Systems at Kennesaw State University (KSU-CES) of Georgia.126 Harp Enterprises Incorporated of Kentucky,127 Scytl, SMARTech, among many others that I do not know and cannot name handle election reporting.128 Even if these outfits are not explicitly beholden to private interests, it would be easy to implant malware on the voting systems they service by burglarizing and/or hacking their company computers first, which they use to prepare programming packets.
To be specific, LHS Associates, which is entirely responsible, to my knowledge, of the programming of voting machines on the county- and township-level, from legacy Diebold optical scanners to modern Dominion optical scanners, in the states of New Hampshire, Massachusetts, Connecticut, Vermont, Maine, and Rhode Island, amongst whose key executives some are ex-convicted felons implicated in the drug trade.129 Fittingly, the company would, back around 06, troubleshoot the number of memory card failures on the serviced states’ optical scanners (which were and are quite common130) by doing something very illegal, at least in Connecticut: swap out memory cards, containing instructions that direct the machines’ reading of vote data and can be used to introduce viral malware, during voting, during elections, in order to deal with procedural difficulties. Said memory cards would be stored soundly in the trunk of a car, idling outside without supervision until they received a call for assistance. Chain of custody is, after all, a famous substitute for toilet paper.131
"I mean, I don't pay attention to every little law. It's just, it's up to the Registrars. All we are is a support organization on Election Day" — the Director of Sales and Marketing for LHS Associates, 2006.132
Vendors are proven to be untrustworthy, uncompromising, negligent and even criminal.133134 But to complete their regulatory capture they take advantage of election authorities’ willingness to be swayed through their bank accounts, and facilitate the corporate infiltration of rule making bodies to bend their decisions in their favor.135
A long-time administrator of the Maryland State Board of Elections, Linda Lamone, was a wholehearted Diebold apologist who sang praise to the perfectability of the company's products and did everything in her power to reinforce the company's tireless pitch that all the calamitous excesses of electronic voting were instead brought about by human errors relating to the operation of the equipment.136137 She even explicitly endorsed the Diebold, and allowed them to utilize her likeliness to market their ExpressPoll e-poll book138 which caused disastrous voting meltdowns during the 2006 primary elections, under her watch.139140 In 2003, despite multiple studies confirming grave vulnerabilities in the Diebold AccuVote TS, one of which was commissioned by the state, the Board of Elections nevertheless moved forward with its $55.6 million contract with Diebold to supply those touchscreen voting machines to all jurisdictions across the state.141
In August of 2007, in response to the corporate voting system certification avoidance scandal referenced above Debra Bowen issued a wave of election system decertifications (including Diebold stock and the ES&S InkaVote Plus) and then conditionally recertified them (excluding the InkaVote Plus) under the stipulation that counties can only purchase those touchscreen devices for disabled voters. The entire stock of paper audit trails produced by the touchscreen voting machines would be manually recounted to ensure, with reasonable certainty, the correctness of the count. This recount would not be paid for by the counties or the candidates, but rather by the companies selling the ADA-compliant voting machines.142 Expectedly, this rule was unpopular with the vendor corporations and the various peons on their bankroll, including Los Angeles County Registrar of Voters Conny McCormack, an avid e-voting defender who, like Lamone, had been recruited for a marketing position with Diebold,143 and lead the charge against the SoS's new rule. She was deeply concerned... about how Diebold's bottom line would be negatively impacted by the rule.144
McCormack said Bowen’s order requires the county's vendors to pay the costs of that recount, which she estimated at $400,000 per election.
“I think we have to see what the vendors are going to say about that”, McCormack said. “The vendors aren't going to make much money in Los Angeles County if they have to pay $400,000 for the recount.”
But Supervisor Gloria Molina upbraided McCormack for her concerns about the vendors’ profit margins.
“I think you are walking close to the edge”, Molina said. “I don't understand why you are so protective of the vendors. You keep saying you are concerned about what this is going to cost them.
“It’s really none of our business. It shouldn't be in our interest to protect the vendors’ profits.”
Top Utah election officials were enamored with Diebold back in the 2000s. Lieutenant Governor Gary Herbert, unabashed Diebold defender and, of course, is one of those people that accuses anyone who is skeptical of counting votes on an easily hackable computer of being a luddite and a conspiracy theorist. The conflicts of interest came to a head after March 2006, when twenty-three-year Emery County Elections Director Bruce Funk invited computer scientists from BlackBoxVoting, including Harri Hursti, to examine the security of the Diebold AccuVote OS optical scan voting system in order to demonstrate his voting concerns practically. Superior Utah election officials, and other county commissioners, did not thank him for exposing systemic defects that could collapse elections in Emery County, and open up elections across the state and the country to compromise. They did not demand Diebold fix their products or to instead refund their contract money, nor did they sue them. Instead, they lambasted him for turning in the electronic voting devices for inspection, locked him out of his office and quickly relieved him of his duty.145146
Phillip Foster, a Sequoia salesman indicted in 2001 by a grand jury for crimes relating to a Louisiana kickback bribery scandal involving an election administrator responsible for servicing election equipment and oversaw the purchase of unnecessary Sequoia equipment, was granted prosecutorial immunity for his testimony in the scandal and was not tried. Foster thereafter rose in the company and eventually came to serve as the Vice President Administration & Strategies.147 He served on the Palm Beach County Election Technology Advisory Committee, from September 2005 through May 2006 and continues to advise the county’s elections supervisor.148
Former California Secretary of State Bill Jones, who helped develop an election “modernization” plan that involved decertifying and phasing out the state's antiquated mechanical voting equipment with high-tech optical scanners and touchscreen voting machines in all fifty-four counties without electronic voting equipment, and sponsored Proposition 41 which allocated $200 million to counties to acquire privatized voting systems and was financed and lobbied for by ES&S and Sequoia, ultimately leaving the office in 2003 to become a top consultant for Sequoia. The officials working under his administration's employ had similar conflicts of interest: his former top aide departed to work as a vice president for business development at the same company, while Alfie Charles, Jones’s press secretary during his tenure, simultaneously sat on the panel that recommended to Jones which machines could be sold in California, and worked on communications for Proposition 41. He went on to work for Sequoia as a spokesman in 2002 soon after the passage of P41.149
After serving as the chief of elections under long-time California Secretary of State March Fong Eu, potent e-voting counter-critic Deborah Seiler departed for a job with Sequoia in 1991 after working in the state legislature for a year, before transferring to Diebold as a sales representative,150 who she helped deliver nearly 1,200 non-federally or state certified touchscreen voting machines to Solano County, among other activities, legal or otherwise. She was also the chairwoman of the California Association of Clerks and Election Officials at the same time. But her saga through and about the revolving door didn’t stop there; eventually she returned back to elections, and was hired as assistant registrar at Solano County in 2004151 before becoming Registrar of Voters at San Diego County in 2007.152
Former Riverside County Registrar of Voters Mischelle Townsend was alleged to have failed to file conflict-of-interest forms from 1998 to 2002 and failed to disclose the source of her husband’s income, and illegally accepted travel and lodging fares from Sequoia Voting Systems in order to facilitate her appearance in an infomercial marketing their products.153154 She was also, as the supposed poster-child of electronic voting, responsible for making Riverside County one of the first counties in the state to use touchscreen voting machines for all registered voters in 1999-2000, which were manufactured exclusively by Sequoia.
Edwin B. Smith III, then serving as the vice president for compliance and certification at Dominion Voting, and who formerly served as vice president of manufacturing, compliance, quality and certification at Sequoia Voting Systems, and, before that, the operations manager at Hart InterCivic, was appointed to the Board of Advisors of the Election Assistance Commission in 2009, which is charged with oversight functions of the very companies Smith served in.155 The same Edwin Smith who, as stated above, spent years soliciting the advice of questionable crackpot contractors over Princeton computer scientists who he threatened with legal action over infringing upon "proprietary corporate trade secrets" if they conducted the independent inspection of the source code of their touchscreen voting system as commissioned by New Jersey.
In 2004, Common Cause reported that Diebold Election Systems had wooed Jack Abramoff's firm Greenberg Traurig with a donation of $275 million. Abramoff and Greenberg Traurig represented OH-18 House Representative Robert W. Ney, who introduced and sponsored the Help America Vote Act in the House in 2001 until its passage, which disbursed $3.9 billion in taxpayer-funded kickbacks to electronic voting vendors like Diebold.156 A payment stub and pre-check-register revealing a $12,500 payment for the month, made from Diebold to Greenberg Traurig, was discovered in a dumpster at Diebold’s McKinney, TX facility in July of 2004 by electronic voting watchdog group BlackBoxVoting.157158
An issue incumbent to the genesis of the computerized voting era was that of equipping DREs with paper audit trails that could be recounted in the event of an error or fraud, but this requirement, though seemingly common sense, was opposed fiercely by disability rights groups implying that only unverifiable machines serve the needs of disabled voters, leading to some to suggest that they were on the bankroll of cynical vendor corporations who benefitted from cheap to manufacturer, expensive for counties to purchase paperless voting machines.159
The National Federation of the Blind, for instance, had, in 2004, championed these controversial, paperless voting machines. It attested not only to the machines' accessibility, but also to their security and accuracy; neither of which is within the federation’s areas of expertise, and was contradicted by a wellspring of scientific research already available to the public at the time. Troublingly, these assertions were not made from a stance of neutrality, as Diebold had allocated a gift of $1 million, which they accepted, to cover the expenses of a new training institute.160
The American Association of People with Disabilities, according to member Jim Dickson, who paper trail-opponent and HAVA signatory Senator Christopher Dodd appointed to the EAC’s Board of Advisors, had received $26,000 from voting machine companies in 2004.161
The long saga of influence-peddling by election vendors in Georgia began in 2002 despite the legislature-backed introduction of a statutory requirement necessitating that voting systems leave behind an independent audit trail of each vote cast.162 Subsequently, Secretary of State Cathy Cox, another such Diebold apologist who repeatedly allowed the company to utilize her likeliness to advertise their products,163 negotiated a deal with the company to purchase unauditable, and therefore illegal, paperless DREs.
This bargain, evidently, necessitated the $54 million164 (plus another $15-or-so million for warranty extensions beyond 2002) makeover of Georgia’s voting systems with unverifiable touchscreen DREs, and that, in order to facilitate the transition in the five months Diebold had to prepare the state for the November 2002 election, the state should engage the complete abdication of its election administrative duties and effectively surrender its sovereignty to corporate contractors working for Diebold, who should service and support the state’s centralized and standardized voting system and county election offices, train poll workers, open and close polling stations, design ballots — a completely privatized and corporatized system.165166 This arrangement still holds to this day, just with ES&S in 2018, and finally Dominion, instead, just even more centralized with KSU-CES out of the picture. At the very same time, the lobbyist for Diebold, the preceding Georgia Secretary of State Lewis Massey, and Cox’s former boss, then joined the lobbying firm of Bruce Bowers.167
The Director of Election Administration under Cox, Kathy Rogers, who was cited as casting a considerable influence over Cox’s final decision,168 is an ardent defender of the faith when it comes to unverifiable, faith-based electronic voting, rejecting the near-consensus on the hackability of voting machines, especially Diebold ones. In 2006, a bill requiring a verifiable paper record of each ballot, introduced in the Georgia legislature at the urging of election-integrity advocates, failed after Rogers opposed it.169 It thus came as no surprise that she should accept a job at Diebold at the company’s enjoyment in December of that year.170 In the present she serves as the senior vice president of ES&S, and promoted its sanctity (and its unverifiable touchscreen electronic ballot marking devices) through hell or high water.171
Karen Handel, whose successful 2006 Secretary of State campaign integrated ideas of election integrity and vote-count verifiability,172 seemingly turn-tailed her position upon inauguration, defending173 and defeating174 a grassroots election integrity suit175 to decertify Georgia’s unconstitutional voting system in the three years it wended through the courts, all the way up to the state Supreme Court. Shortly after winning election in 2006 Handel appointed Rob Simms as Deputy Secretary of State, who worked as a partner to Lewis Massey’s Atlanta-based Massey & Bowers lobbying firm.176 She received $25,000 in campaign contributions from employees and family members associated with the lobbying firm.177
Later litigation by the plaintiffs of the Donna Curling et al. v. Brad Raffensperger et al. in mid-2019 was more successful, and achieved the suits goals of decertifying the unverifiable AccuVote-TSx DREs and forcing a court-ordered transition to paper balloting.178 Rather than move to cheaper and more reliable hand-marked paper ballots processed by optical scanners, against all expert counsel,179 state administrators sided with proposals to replace the aging DREs with almost as unverifiable, for reasons discussed later, electronic ballot marking devices and machine-marked paper ballots180 — a 2018 measure to implement universal machine ballot marking was defeated by election integrity advocates despite vigorous corporate lobbying181 but was rammed through in 2019 by the state legislature anyways.182 The first of these proposals, endorsed by Governor-elect Brian Kemp earlier in the year and before the landmark ruling, was to back a >$100 million ES&S bid to purchase ExpressVote machines.
In 2019 Kemp established the Secure, Accessible and Fair Elections Commission to initiate an appraisal process of multiple contracts from six different prospective vendors, acquired through a request for proposals submission.183 Worries that the bid selection process was pre-determined to favor ES&S proliferated after Kemp’s cabinet appointments came to light.184 David Dove, Kemp’s appointed executive counsel, worked on an advisory board for ES&S, and attended a Las Vegas conference hosted by them in 2017.185 His deputy chief-of-staff, former state representative Charles Harper,186 was a lobbyist for the office of Secretary of State during Kemp's former incumbency from 2012 through 2017, before pre-registering as a lobbyist for ES&S. Additionally, John Bozeman, formerly the head of legislative affairs for Georgia’s former governor, Sonny Perdue, registered to lobby for ES&S.187
It then came as a surprise when the state instead signed a $90 (later $130) million contract with Dominion instead.188189
Of course, as the Kemp-Raffensperger administration is a triple-chocolate mousse of duplicity, the spinning of the revolving door of corruption didn't end with ES&S; Dominion’s lobbyist, Jared Thomas, was then-state secretary Brian Kemp’s chief of staff and press secretary from 2012 to 2015. Dominion’s partner in the state is KNOWiNK, a supplier of electronic pollbooks, which are used to sign in voters and confirm voter registrations. KNOWiNK’s founder and CEO is Scott Leiendecker, whose wife donated $2,500 to the campaign of Brad Raffensperger in November 2018. It was this admin that authorized the use of KNOWiNK e-poll books coordinately with the new BMDs.190 Perhaps it is the case that, whatever financial incentive Dominion offered to Kemp, it exceeded ES&S’s.
ES&S’s highly-secretive National Customer Advisory Board, the very same that hosted the likes of David Dove, hosted more than a dozen top election officials from states all across the company over its long, publicly undisclosed existence, and beguiled them with lavish gifts, prepaid travel fares, and exquisite dining, including but not limited to Mike Ryan, since-resigned191 executive director of New York City’s Board of Elections, Nikki Charlson, deputy administrator of Maryland's election commission; Marisa Crispell, elections director in Luzerne County, Pennsylvania; Steve Harsman, deputy elections director in Montgomery County, Ohio; Ralph Mohr, elections commissioner in Erie County, New York; Brad Nelson, elections director in Pima County, Arizona, historically embattled for his lack of transparency192 and (some say deliberately) disastrous administration of a 2006 bond election; and Greg Riddlemoser, elections director in Stafford County, Virginia.193
One of these “customers” is Toni Pippins-Poole,194 an election administrator in Dallas County, Texas, who also illegally solicited thousands of dollars in contributions and funds from ES&S contractors in 2017.195 The county subsequently penned a $30 million contract with ES&S to replace its older yet still theoretically verifiable hand-marked paper ballots processed by M100 optical scanners with newer, unverifiable and expensive ES&S ExpressVote ballot marking devices for all in-person voters.196
Louisiana is one of the last states to use exclusively paperless DREs, specifically old circa-1998 Sequoia AVC Advantage serviced by Dominion, and indeed, they use them in every parish statewide.197 This means recounting or auditing them is impossible. In 2018, the state was in the process of finalizing a $95 million contract with Dominion to replace its slate of equipment with upgraded voting devices that are equipped with paper trails, but the deal was nixed by an official appointed by then-incumbent Governor Edwards, who sided with the complaints fielded with ES&S purporting that the contract conditions were biased in favor of Dominion. Louisiana campaign finance records show that ES&S’s lobbyist in Baton Rouge, William “Bud” Courson, has donated $13,250 to Edwards’ campaigns since 2014.198
The congressional lobbying platoons of the two largest vendor corporations expanded significantly after 2016. ES&S hired lobbying firm Peck Madigan Jones in Oct. 2018 and paid it a combined $150,000 to lobby the U.S. Senate and House of Representatives in the fourth quarter of 2018 and the first quarter of 2019. ES&S did not employ any federal lobbyists in 2017, and when they reported lobbying in previous years it was at a much lower level, spending just $10,000 in many quarters. Dominion Voting Systems, which was recently acquired by New York-based hedge fund Staple Street Capital, signed its first-ever federal lobbying contract in January 2019 with Brownstein Hyatt Farber and Schreck and has paid the company at least $30,000 so far to lobby Congress.199
Some of the appropriations were directed at the office of Mitch McConnell.200 It was simultaneously that he embarked on a quest to disavow and filibuster any and all post-2016 election legislation, both the bitterly divisive and the bipartisan, that would’ve forestalled sales and diminished vendor profits by enforcing greater standards for the cybersecurity that they seem to loathe.201202
Except for a minor section of the 2018 omnibus spending bill that authorized $380 million,203 and then another $250 million by 2019,204 of no-strings-attached discretionary funding to jurisdictions across the country to purchase new election equipment, not even 1/5th of the federal spending allocated by HAVA and insufficient to upgrade aging election systems nationwide205206 — indeed, entirely entrusted to the states and counties to spend it wisely on increased security measures, establishing meaningful audit protocols and switching to hand-marked ballots rather than machine-marked ballots, and it seems as though the bill served only to fill the corporate trough than actually accomplish anything substantial.207 As we have seen, the money has been used questionably. McConnell’s subsequent pandering and crusade against election integrity, broadly consistent with his instrumentality in the drafting and passage of the Help America Vote Act and the total digitization (and corporatization) of the country’s elections,208 altogether becomes easy to explain.
And the corruption goes on. I will not list it all.
There are, of course, in the great war against election integrity, those who have abdicated their duty to act in the general interest of the public on their own, uninfluenced terms, and to adequately exercise the provisions and authorities granted to them by law, or indeed, embrace lack of desire to abide by the regulations of the law. To this end some election officials are negligent; others criminal.
Case in point is the production of former San Diego County Registrar of Voters Mikel Haas, and the horrendous management policies of his administration; chief among them was the “sleepover” policy, defined as the delivery of active, pre-programmed voting equipment into the unsupervised tutelage of temporary, volunteer poll workers who are subject to the slightest of standards and security screening to ensure that they can effectively participate in the election management process, which obviously constitutes a breach in the chain of custody of the equipment, a grave security blind spot that could compromise the integrity of the elections in San Diego County, and runs in contravention to federal and state law,209210 resulting in him being on the receiving end of bipartisan condemnation.211 He was removed from his office in March of 2007… and promoted to deputy chief administrative officer of the county as a token of appreciation for the numerous rolling disasters under his belt.212 He was summarily replaced by Diebold/Sequoia sales representative Deborah Seiler.
And then there is Arizona Secretary of State Jan Brewer who, in her unbridled opposition to election transparency and integrity advocacy in all its forms,213 went out of her way to characterize the concerned citizens worried with her late-2005 approval of unverifiable, now-known-to-be-vulnerable Diebold DREs for use in almost every precinct in the state as “anarchists”, “conspiracy theorists”214 and “brown shirts”.215
More recently, there was the county clerk of Los Angeles County, Dean Logan, who, in 2020, shepherded county election administration into signing a $282 million contract with Smartmatic to develop an “open-source”, unverifiable, unaccountable, obstructive, overly-expensive proprietary electronic voting system consisting of touchscreen ballot marking devices found in violation of over forty clauses of the California Voting System Standards216 before its “conditional certification” in by March by the Secretary of State,217 whose operation disastrously collapsed the primary elections on Super Tuesday not long after their roll-out218 — but at least it's accessible, and “publicly-owned”, the latter of which necessitates transparency above all else. To that end, Logan’s administration presided over the imposition of a policy of secrecy, whereby pollworkers and technical operators are not allowed to communicate the specifics of the system to the press,219 an order which he also lied about issuing.220
Two years onward, many of the security violations persisted into VSAP version 3.0.221 When this fact was pointed out by election integrity advocates, he instead decided that, since this is 2022 and never-my-fault narcissism is okay, admirable, even, he didn’t need to take responsibility for his own actions; he just smeared those expert witnesses as liars and conspiracy theorists, and baselessly accused them of spreading misinformation and disinformation when, ironically and hypocritically, they had done no such thing. He refused to even point to the exact instance in which they allegedly disserviced the populace.222
Granted, the crusade against transparency is not necessarily the manifestation of malice or ignorance, as officials and career servants charged with, in some manner, the responsibility of informing the public, represent the first line of defense against the supposed menace of lack of trust (or, more inanely, “faith”) in the democratic process — a menace whose very existence is better interpreted as an indictment of the non-transparent, secretive and unaccountable election process itself, one that, if administered in any other country on Earth would witness a unilateral condemnation by the U.S. Department of State for its lack of transparency and accountability, rather than something to be blamed on the insanity of the voters.
For now, the drill-down will be limited to the administration of democracy itself, and the players in its presence. We will observe first the triumphs and failures of the guidelines of voting system testing, and of the pre-election equipment testing apparatus; how an attacker might proceed with rigging our elections from top to bottom; how states audit their elections and their susceptibility to subversion, both on paper and in practice; and the tireless efforts of those who seek to shine light on our untransparent, computerized democracy, and the equally tireless efforts to obstruct them.
3. The Election Assistance Commission and Voting System Certification
“...for instance, the Help America Vote Act mandates that an electronic voting machine be in every precinct in the country and that mandate preceded the funding of research necessary to ensure that there is some prototype or standard for such machines ... There is no prototype. There are no standards. There is no scientific research that would guarantee any election district that there’s a machine that can be used to answer these very serious questions ... But there’s an erosion of voting rights implicit in our inability to trust the technology that we use and if we were another country being analyzed by America, we would conclude that this country is ripe for stealing elections and for fraud.”
— former chairman of the Election Assistance Commission, Reverend DeForest Soaries (2006)223
The Election Assistance Commission, established under Title II, Subtitle A, Part 1 of the Help America Vote Act of 2002, is an independent agency charged with enforcing regulatory standards, administering state-level procurement of voting systems that meet federal voting system guidelines defined in the 1.0 version of the Voluntary224 Voting System Guidelines of 2005, effective until November 5th, 2023, the 1.1 version enacted in 2015, or the 2.0 version adopted formally in 2021, both by a unanimous vote of Commissioners, and acting as a national clearinghouse for information regarding election administration. Intended to replace the older voluntary standards set forth under the Federal Election Commission during the nineties and very early 2000s, Voluntary Voting System Guidelines (VVSG) are a set of specifications and requirements against which voting systems can be tested to determine if they meet minimum functionality, accessibility, and security capabilities.225
Under Title II, Subtitle B, Part 3 of the Help America Vote Act of 2002, the EAC is further tasked with providing for the testing, certification, decertification, and recertification of voting system hardware and software, and the documentation remediation of runtime anomalies discovered over the course of certification. This is achieved through testing done by voting system test laboratories (VSTLs), or independent testing authorities, which are testing suites, independent of the federal government, accredited by the EAC under a vote by its four Commissioners to authorize these private laboratories, evaluated and statutorily recommended by the Director of the National Institute of Standards and Technology,226 unless the Commission should object to the recommendations of the NIST and provide a written explanation for its divergent decision, to carry out the process of voting system standards enforcement.
Lastly, under Title II, Subtitle B, Part 3, the Director of the National Institute of Standards and Technology will monitor the performance and adherence to guidelines of voting system test laboratories, to make appropriate recommendations regarding the continued acknowledgement of the VSTL and whether or not the EAC should revoke its accreditation.227
The purpose of this section will be to go over some of the requirements of VVSG 1.0 and 2.0 that are directly pertinent to matters of election security. Only federal certification processes will be inspected.
Testing Sequence
The Voluntary Voting System Guidelines 1.0 Volume 2 manual describes various tests used by voting system test labs to conduct pre-certification tests. Specifically, the testing sequence is summarized in § Section 1.4, which will be used as a template here.
The first step mandates vendor compliance with the voting system test laboratory according to requirements prescribed in VVSG 1.0 Volume II § Section 1.5. They must submit all technical documentation, known as the Technical Data Package, or TDP, necessary for the identification of the full system configuration entered for evaluation and for the development of an adequate and effective testing plan by the testing lab. This data package includes documentation for the system's hardware, software, security, test and verification specifications, operations procedures, maintenance procedures, and personnel deployment and training requirements.
The second step involves a review of the quality assurance program created by the vendor, which, in accordance to provisions of VVSG 1.0 § Section 8.x, defines procedures that are initiated at the activation of the voting system and extends throughout the maintenance life cycle of the voting system to ensure that it conforms to workmanship and production standards and conventions laid out in the Voluntary Voting System Guidelines, for which the responsibility for carrying out quality assurance, testing and documentation functions pursuant to that plan is solely given to the vendors.
It also requires the review of the vendor submitted configuration management plan that invokes a broad array of activities relating to record keeping, auditing and reporting, including the documentation of discrete system components, creating records of a formal baseline and later versions of components, controlling changes made to the system and its components, and so on, as outlined in VVSG 1.0 Volume I § Section 9.x.
For the third step the VSTL shall devise a comprehensive system test plan to determine system correspondence with the requirements of the Voluntary Voting System Guidelines according to processes specified in VVSG 1.0 Volume II § Section 1.8 and associated subsections. After conducting an inspection of the TDP as specified in step one, along with all complementary information, the vendor will agree to pay for the costs of the testing, and deliver all requested hardware and software.
The test lab shall create an adequate test environment impounding optimal environmental conditions, wherein they will initiate and complete the tests required to evaluate the performances of selected system characteristics, after which they will establish a target metric against which the system characteristics are measured to demonstrate expected and desirable performance levels, before performing a post-factum verification of the normality of the equipment’s condition after the test. They will confirm that vendor documentation corresponds to the configurations and operation of the actual system, and that documented vendor practices for quality assurance and configuration management comply with the Guidelines.
The fourth step impounds a formal inspection of the voting system codebase by the voting system test lab. Selected software components are subject to source code audits that appraise the quality of the codebase authorship, and verifies that it is written in general accordance with design protocols specified in Voluntary Voting System Guidelines 1.0 Volume I § Section 5 and Voluntary Voting System Guidelines 1.1 Volume I § Section 5, that is, conformance to standards of programming completeness, elimination of unused or nonexecutable code, consistency, commentary, conciseness, modifiability, modularity, structure, and traceability.
Similarly, application logic is audited to determine its adherence to the same standards. The source code inspection, as described in VVSG 1.0 Volume II § Section 5.4 and the subsequent subsections, will also impound the enforcement of certain standards compelling the voting system vendor to use control constructs in their code and replacement rules for streamlining and/or formalizing system logic. The aforesaid subsections also prescribe guidelines for coding conventions. Source code must be provided by the manufacturer in the Technical Data Package.
VVSG 1.0 Volume II § Section 1.3.1.3 indicates that unmodified commercial-off-the-shelf generated software source code is exempt from the aforementioned guidelines and may not be examined in full by independent testing suites, however, the election vendor must provide uncompiled/uninterpreted, human-readable source code generated by COTS packages and embedded in software modules to the accredited test lab in order to permit cursory inspection of the source code using various sampling and automated scanning tools to determine, with a certain degree of (questionable) certainty, that the COTS software has not been subject to unauthorized modifications, but will not be subject to a full review.
Evidently, the voting system certification pre-test process does not merit provisions for requisite standards of finesse that demand system stability or security, else one might assume that the large cohort of standardized, very common and almost systemic vulnerabilities afflicting every election software version, variant and model, irrespective of the manufacturer of the consulted certification authority, to ever exist would be minimized, or at least known to the cybersecurity community and to the federal and state governments without the need for private examinations of the source code. That, or the implication is that the voting system test laboratories are not thorough.
Step five involves the test lab witnessing of a system build conducted by the vendor to conclusively establish the system version and components being tested; the test lab must witness the build of the software source code at the vendor site immediately prior or as a part of the physical configuration audit in order identify the system version and determine that it matches the version listed by vendor documentation, per protocols defined in VVSG 1.0 Volume II § Section 6.2.2.
Step six requires the test lab to conduct stress tests of the system hardware in order to determine its reliability under strenuous environmental factors, including humidity, heat, cold, acoustic stresses, sustained and variable voltages and electric currents, and induced operational stresses, as specified in VVSG 1.0 Volume II § Section 4.2 and associated subsections. These conditions are intended to replicate those found during storage of polling place devices inside a warehouse, during transit from and to a warehouse and a polling place in order to preclude equipment damage or decalibration during transport, and during an operating context in which they come into contact with voters. § Section 4.6.1 specifies that the procedures and conditions of these tests correspond generally to those of MIL-STD-810D, “Environmental Test Methods and Engineering Guidelines”, 19 July 1983.228
Steps seven and eight mandate functional and performance testing of hardware components; and system installation testing and testing of related documentation for system installation and diagnostic testing.
The ninth and tenth steps involve the functional and performance testing of software components, functional and performance testing of the integrated system, including testing of the full scope of system functionality, performance tests for telecommunications and security, and examination and testing of the System Operations Manual. System integration testing, defined in VVSG 1.0 Volume II § Section 6.x, is the testing to be performed by the accredited test lab to confirm the proper functioning of the fully integrated components of a voting system submitted for national certification testing.
Basic physical security measures are also tested under this section and, for systems that use public telecommunications networks, such as the Internet, to remotely transmit election management data or official election results, the accredited test lab shall conduct tests to ensure that the system provides the necessary identity-proofing, confidentiality, and integrity of transmitted data. These tests shall be designed to confirm that the system is capable of detecting, logging, preventing, and recovering from types of attacks known at the time the system is submitted for certification, among other safeguards of questionable utility.
The Functional Configuration Audit encompasses an examination of vendor tests, and the conduct of additional tests, to verify that the system hardware and software perform all the functions described in the vendor's documentation submitted for the TDP. It is an exhaustive verification of every system function and combination of functions cited in the manufacturer’s documentation. Through use, the FCA verifies the accuracy and completeness of the system Technical Data Package. The various options of software vote counting logic that are claimed in the manufacturer’s documentation shall be tested during the system-level FCA. Generic test ballots or test entry data for DRE systems, representing particular sequences of ballot-counting events, will test the counting logic during this audit.
Physical configuration audits, or PCAs, compare the configuration of voting system components submitted for certification to those specified in the supplemental technical documentation of the manufacturer. The test agency shall examine the vendor's source code against the submitted documentation during the Physical Configuration Audit to verify that the software conforms to the vendor's specifications.
The eleventh step requires the VSTL to examine the system maintenance manual, developed by the vendor and procured by county election workers, information systems personnel, or maintenance personnel, to determine if it is detailed and accurate enough to support them in adjustment or removal and replacement of defective or failing components or modules in the field, per VVSG 1.0 Volume II § Section 2.9.
The twelfth and thirteenth steps describe how, after testing is complete, the VSTL will prepare an exhaustive documentation of test results in the form of a National Certification Test Report, and its conveyance to the EAC.
Tests mainly include the verification of the accuracy of the vendor’s documentation.
The regulatory assurance of the test plan is predicated on the honesty of the vendor to accurately describe the full breadth of functionality for each system component in the voting system. There is no language disallowing the installation of irregular components so long as it and its functionalities are included in the voting system documentation. VSTLs cannot probe for functions beyond the scope of documentation.
This is perhaps best exemplified by the fact that this guideline was already present in the 2002 Voting System Standards manual that was instituted and enforced by the Federal Election Commission, and Sequoia touchscreen voting machines were, given the time, almost certainly reviewed by VSTLs and certified by the National Association of State Election Directors (which handled voting system certification before the EAC) and, nonetheless, this didn't stop every Sequoia touchscreen in dozens of states, each with their own election system regulations, from having a bright yellow button on the back that allowed voters, poll workers and precinct inspectors to cast an unlimited number of votes back in 2006.229230
The accredited testing authority has little in the way of determining whether or not the system build or source code submitted for certification even matches what they will sell to counties, other than with hash code validation or other forms of automated comparative measures, which can easily be circumvented, or whistleblowing, such as with the tales of Stephen Heller, who brought to light smoking gun evidence that Diebold had been conspiring to sell California counties thousands of units of uncertified voting equipment, for years at that point.231
The consequences of this issue have, perhaps, been observed in practice, as revealed upon closer examination, by Bev Harris, of the Diebold GEMS database foolishly and incompetently left out in the open in an unsecured Internet-facing internal server, in 2002, and summarized by these statements:232
After the program is certified, it must not be changed without reexamination, so you can imagine my surprise when I ran into these comments, written into the source-code files for Diebold Election Systems by its programmers:
“Remove SCWinApi module till pass WYLE233 certification.”
And because the version sent to Wyle for certification is supposed to be the official version, and the voting machines are supposed to use only the officially-certified version, you might wonder at this comment:
“Merge WYLE branch into the stable branch.”
Why are we removing things before we send them to Wyle, and why are we merging the officially certified version back into something else? Just wondering.
Error Rate
VVSG 1.0 Volume II § 4.7.1.1 defines the desirable “target” error rate at one error per 10,000,000 ballot positions (available voter selections, aggregated from all election contests), or an error rate of 0.00001%. Because this is infeasible, the maximum “acceptable” error rate is defined at a more modest one error per 500,000 ballot positions, or an error rate of 0.0002%. We will hereinafter list examples of voting system failure as they can be known post-factum. We shall assume for this subsection that “error rate” impounds the rate of mistabulation (“miscounting votes”) or failure to register scanned or cast votes, rather than issues relating to faulty memory cards, debris build up on optical scanners, incorrect ballot definitions, and so on.
The “one error in 10,000,000 ballot positions” target error rate for direct record electronic machines, as well as now-ancient technology such as punchcard machines, was first established in its current form in the 1990 Voting System Standards under the Federal Election Commission.
Presumably the error rate of the voting system subject to test should reach a minimum by the time of certification. Of course, mistabulation errors occur quite often. In pre-election logic & accuracy testing (next section) certain issues with device maintenance, obvious tabulation errors stemming from misprogramming and so forth are dealt with in the setup of the election.
To calculate the error rate we will define the quantity of ballot positions as the number of ballot bullet points on a given ballot; for a hypothetical ballot on which three contests are present, with unto themselves three, two and seven possible candidates to vote for, there are twelve ballot selections present. We will define the total ballot positions to be equal to the ballot positions multiplied by cast ballots. We will define the maximum voter selections to impound the highest number of votes a voter can mark on a ballot; for ballots consisting solely of “vote-for-one” contests, the maximum voter selections equals the number of contests. We will define the misread votes to equal the number of voters selections interpreted erroneously or not read at all; if entire ballots are voided then the misread votes equals the number of votable ballot positions. And finally, the error rate is defined as the ratio between misread votes and maximum ballot positions. The HAVA violation rate, or just the violation rate, is equal to the error rate divided by the decimalized acceptable error rate, 1/500,000 = 0.000002.
A software programming error caused Dallas County, Texas's new, $3.8 million “high-tech” ballot system serviced by ES&S to miss 41,015 votes during the November 1998 election. The system refused to count votes from 98 precincts, telling itself they had already been counted. Operators and election officials didn’t realize they had a problem until after they’d released “final” totals that omitted nearly one in eight votes. 12.5% of ballots were completely uncounted in the initial tally, and the precincts not tabulated by the ES&S election management system witnessed an error rate of 100%.234
Optical scanners in San Diego County miscounted 2,821 absentee votes cast in the 2004 Democratic presidential primary and Republican Senate primary. Out of 208,446 ballots cast, this is at most an error rate of 1.35%.235
ES&S Optech IIIP Eagle optical ballot scanners in Milwaukee County, Wisconsin, failed to count eighteen ballots in Milwaukee Ward 43, seven in Ward 44, and ten in Ward 98, and, for 1,199, 1,954, and 660 total ballots cast in the 2004 general election with thirty-eight (thirty-nine in Ward 98) total ballot lines, including eleven voter-markable ballot lines each, adds up to a total error rate of 0.43%, 0.10% and 0.43% respectively, running in violation of the 1 in 500,000 error rate mandated by law by a factor of 2,173, 519, and 2,137. Similarly, Diebold AccuVote OS optical scanners produced an error rate of 0.11% per ballot line, failing to count eleven ballots with 45 total ballot lines, including eleven voter-markable ballot lines, in Germantown District 1 in neighboring Washington County.236
Sequoia Advantage and Danaher Shouptronic push button direct recording electronic voting machines recorded massive undervotes for all races (President, Representative, state Supreme Court, etc.) which were as high as 15% in some precincts in New Mexico in the 2004 general election, a possible violation rate factoring at 75,000 times the federal maximum error rate. The massive undervote rate was highly correlated with voting type (only election day voting showed this anomaly; early voting did not despite using the same equipment, and absentees, counted by optical scanners, did not either), and demographics (Hispanic and Native American undervote rates were far higher than non-Hispanic White undervote rates, but only for push button precincts — opscan and touchscreen precincts didn’t show discrepancies as extreme). Expected undervote rate based on precinct-level data for mail-in voting and voting in counties that use other in-person voting systems is a mere 1.5% or less.237
ES&S machines recorded zero votes for former/returning Texas Supreme Court Justice Steven W. Smith in the irregularity-ridden March 7th Republican Party primary for the Supreme Court’s second seat in Winkler County, where he won 74% and 65% of the vote in his 2002 and 2004 general election runs respectively.238
Of the 104,325 ballots cast in the March 8th, 2005 Miami-Dade County special election on Election Day using ES&S iVotronic direct recording electronic voting machines, 1,106 were recorded as having undervotes, 477 of which were directly attributed to the DREs; 1.06% of voters supposedly went to the polls and effectively cast a blank ballot since there was only one race to vote on, a violation rate of 5,300. Absentee undervote rate was exactly zero.239 Undervote rates for some other local elections are also quite absurd, with the earlier Golden Beach, Florida special election dated February 15th, 2005, with its one race, having a DRE undervote rate of 24.7% and a (six ballots) absentee undervote rate, as reported by optical scanners, of 50%.240
In the May 23rd, 2006 Democratic primary for the Arkansas State Senate District 16, it was discovered several days after the Election Commission certified that race and Crumbly and Willis began campaigning for the June 13 runoff that commission staff discovered that 432 of 2,011 votes cast at the Allen Temple precinct in Phillips County had mistakenly been counted as ballots for the Republican primaries by the ES&S iVotronic DREs used there, effectively nullifying them, tallying up to an error rate of at maximum 21.4%, 107,000 times higher than the federally mandated maximum error rate.241
ES&S M100 optical scanners and iVotronic DREs in the town of Waldenburg in Poinsett County, Arkansas recorded zero votes for mayoral candidate Randy Wooten, despite him having voted for himself and knowing at least eight or nine people who had sworn that they had voted for him. With only eighty votes cast in the mayoral election, this maximally amounts to an error rate of 11.25-12.5%, 56,000 to 62,500 times higher than the federally mandated maximum error rate.242
ES&S iVotronic touchscreen machines failed to tabulate perhaps as much as 13,000 votes in Sarasota County for the hotly contested election to replace former Secretary of State and erstwhile representative Katherine Harris in Florida's 13th Congressional District, which was decided by 369 votes overall, enumerating a drop-off rate of ~9.1% for 142,532 ballots cast.243 By contrast, absentee drop-off rates were a far more reasonable 2.5%, discounting lack-of-voter-enthusiasm based explanations. Speculation for this egregious undervote involved poor ballot design, leading to voters failing to notice the race on the electronic ballot, but these explanations fail to take into account hundreds of voter complaints detailing voting machine problems and the inability to select representative candidate Christine Jennings on the touchscreen even when pressed repeatedly.244245246
On March 4, 2008, the Diebold GEMS central tabulator failed to upload and store 105 ballots recorded on their AccuVote touch-screen voting machines, even though the system reported that all the ballots on the 1,599 memory cards had been uploaded successfully. The elections website of Butler County, Ohio (which has since corrected the GEMS error) reports that 94,053 ballots were cast in the election. The 105 ballots missed by the GEMS upload software represent from 0.08% to 0.18% of the ballot positions counted by the system, depending on the proportion of Democratic to Republican ballots stored on the memory card, since there were nearly twice as many contests on the Republican ballot). This means the error rate on the Butler County GEMS server was between 400 and 900 times as high as the rate allowed by federal law.247
The freshly deployed Sequoia Optech 400C Insight optical scanners in Palm Beach County, Florida misinterpreted 156 of 11,748 invalid ballots, that is, overvotes and undervotes, for a judicial race in September 2008, as valid ballots, and greater than 600 valid ballots as invalid, adding up to a minimum of 756 errors. For 102,746 ballots cast and two ballot positions across two contests, adds up to an error rate of 1.84%, which is 920 times larger than the 1 in 500,000 error rate mandated by law.248
197 absentee votes in Precinct 1E-45 were not included in the final results by the Diebold GEMS central tabulation system in the November 2008 general election in Eureka, Humboldt County, California. For 64,161 cast ballots, this amounts to an error rate of 0.307%, 1,535 times larger than the 1 in 500,000 error rate mandated by law.249250
Freshly contracted and serviced ES&S DS200 optical scanners in the South Bronxian Public School 59 precinct in New York falsely recorded overvotes, and subsequently voided, for 70% of the 103 ballots scanned in the September primary, and 59% of ballots in the 2010 November general election. Inspecting digital ballot images retrieved by public records request, ballots marked as having “overvotes” by the scanners were found to frequently have had perfectly discernable voter selections.251
Only sixteen votes (7 Yes - 9 No) were recorded as having been cast by ES&S DS200 for the local 2014 ballot referendum in the City of Stoughton, Dane County, Wisconsin that asked if voters wished to overturn the infamous Citizens United SCOTUS ruling, despite >5,350 voters known to have voted in the city's six precincts for other races.252253 Updated returns showed that it easily passed 4,440 vs 992, although bizarrely Ward 9 and Ward 10-11 reported zero votes.254 This accounts for a maximal error rate of nearly 100%.
Tens of thousands of votes for president were recorded as undervotes by aging ES&S Model 100s and, surprisingly, freshly deployed ES&S DS200 optical scanners in the cities of Detroit and Flint, Michigan and Milwaukee, Wisconsin in the 2016 United States presidential election and, due to the inefficacy of the vote recounts there, these likely scanner failures were never resolved.255 These undervotes are known to not reflect voter intention in the city of Racine, Wisconsin, which used Sequoia opscans, where error rates ran as high as 2-6% — the tally of presidential contest was tracked quasi-manually using a “clicker”, and matched to the post-2016 machine retabulation “count” to calculate the error rate.256257 Errors in suburban Racine County precincts were, by contrast, much lower. Election results certified anyway despite absurd undervote rates.
Physical Security
VVSG 2.0 § Section 12 specifies methods to physically safeguard voting equipment from tampering through use of access controlling methods, and other methods such as installation and interaction event logging during voting. It extends VVSG 1.0 Volume I § 7.3.1, which advises poll workers on how to protect and perform orderly shutdown of equipment in the event of tampering, vandalism, or civil disobedience.
The most basic physical security solution is the tamper seal, which is ideally used to secure USB and removable media ports, control panels, and boxes or bags used to contain ballots during elections or before recounts and audits. They are sometimes informally marketed as being “tamper-proof”, suggesting that they cannot be bypassed. Numerous studies have confirmed that security seal designs can easily and summarily be thwarted by determined, premeditated attackers.261262 Thus, the aim is not to design an infallible seal, but to design one that cannot be defeated without leaving evidence of an attack behind.
If tamper-“evident” seals are found in the breach, what will, or can be done about it? Hypothetically, common sense procedures would dictate, at minimum, to decommission the breached tabulator, and retabulate (or, preferably, count by hand) all ballots counted by the original machine, or to decommission breached voting machines, though usually protocol isn’t so airtight.263
The implementation of such security seals, then, is predicated on the presence of some statutory clause defining remediatory actions in the event of tampering, and if these protocols are even effective. Of course, whether or not tampering is determined to exist is solely the discretion of the election administrators in charge of executing such protocol, and there is much impetus, even disbarring malice, to cover-up or dismiss evidence of machine tampering in order to avoid too much negative attention being turned to their production.
The election remediation polynomial is thus amended to impute a term encapsulating the ability of election officials to recognize prima facie evidence of tampering as such, rather than rationalize and dismiss them as “human error”, or ignore them entirely.
Safeguarding Integrity of Election Data
VVSG 2.0 § Section 13 includes provisions for the safeguarding of the integrity of system data. Many of these provisions presuppose that any unwarranted modifications of election and results data stem from man-in-the-middle attacks and so can be prevented by internal validation and computer-generated cryptographic measures, which obviously wouldn't prevent data corruption if the voting machines are themselves compromised.
Provided the election industry’s historical and continuing hostility towards any sort of common sense cryptography measures, and the long-standing refusal of both VSTLs and the EAC to confront these obvious shortcomings and the many infractions made against already existing VVSG264 regulations by vendors, there is no guarantee that even this will protect from wanton interceptions and en-route modifications of transmitted election data.
The most notable of these provisions is VVSG 2.0 § Section 13.1.1 and its subclauses, which issue the requirement that voting systems authenticate system administrators and restrict to them the authority to modify the system configuration file, which the Guidelines document describes as a file that manages the operating system, application logic, security, and so on, so maintaining its integrity is critical to the proper functioning of the voting system and the health of elections administered using the system. The election management system must also authenticate system administrators before permitting the modification of system configuration files.
Election management systems are commercial workstations used by county election officials to prepare and manage elections. They have applications that are used to create and dispatch election definitions, manage elections databases, activate voting machines, encode voter smart cards that qualify them to vote, they contain a central tabulation program that aggregates unofficial or official results, depending on the policy of the election officials, alongside “cast vote records” and “ballot images” if any are exported, stored on removable memory cards or flash drives and transferred manually, or transmitted by a telephone line or Internet/LAN-facing cellular modem, to the EMS memory. They also usually have a vote reporting module that transmits votes to, for example, a media vote count collecting consortium like the Associated Press, or a state central tabulator, sometimes by Internet.
As a standard laptop or PC workstation the EMS is, used to program voting machines, is capable of Internet connectivity, sometimes is connected to the Internet, and is thus at risk of compromise.
For example, despite official denials from the voting system manufacturer, ES&S ultimately admitted to including installed remote access software and Internet-facing modems on the election management systems it sold to over 300 counties across the United States, including Venango County, Pennsylvania,265266 between 2000 and 2006 to aid in remote client computer file access and troubleshooting by ES&S technicians, creating another port of entry for hackers who can intercept these modem calls to install malware onto the EMS.267 That specific brand of remote access software is pcAnywhere, which, at the same time, was inflicted by a severe vulnerability that allowed remote attackers to execute arbitrary code without authentication.268 Evidence says that jurisdictions are not always aware of the use of this software, and it's unlikely that election administrators had updated their software to patch this vulnerability, or if it even matters.
The election reporting module is physically “separated” from the EMS, however, since vote counts are transferred from the EMS/tabulator to the reporting module by electronic storage medium in this configuration it’s also not really “air-gapped.269
Because the EMS is inherently centralized, unlike polling place voting machines, used to facilitate the central programming of precinct voting systems, used to centrally tabulate and report election results from all precincts, and are generally connected, at some point in their existence, to the Internet, they are extremely insecure and are likely to be tantalizing targets for hacking by corrupt election officials seeking to gain the patronage of the highest monied bidder, to state-backed hackers.
In 2002 it was alleged that the general illegalities that election vendors often engage in, of course, continued in a early 2002 election for the Riverside County, California Board of Supervisors. Two Sequoia technicians had been dispatched to the central tabulation room, where the WinEDS EMS system was consolidating and reporting votes, at 8:50 p.m., while tabulation of votes from two-thirds of precincts had stalled. The race between Lisa Soubirous and incumbent Bob Buster left no candidate with an absolute majority of the vote, so it was heading to an automatic runoff. However, once the vote counting resumed, the newly counted votes percolated asymmetrically into the already reported totals of the various candidates, and Buster's percentage of the vote gradually rose... and rose... and rose until it reached just a hair over 50% of the vote, enough to avoid runoffs, sending him back to office.270271
It’s conceivable that early-counted absentee ballots favorable to Soubirous or harmful to Buster precipitated the early night performance, or precincts less favorable to Buster reported first, however, provisional ballots from all precincts, which were cast on Election Day by voters with registration issues or were assigned to the wrong precinct, showed Buster getting 47% of the vote, exactly the same percentage as his vote before tabulation resumed.
Sequoia marketing maiden Mischelle Townsend, credulous as ever, disputed that election rigging ever would take place due to a supposed ‘lack of motive’ despite the storied history of election rigging at the county-level by political machines going back decades and centuries. There is a considerable financial incentive to rigging that specific election — Riverside County was, after all, a quickly expanding county with many opportunities for prospectors and construction companies to capitalize off of, so long as county supervisors let them. And yes, what those Sequoia technicians did is expressed forbidden by state law, for Section 18575 of the California Elections Code makes it illegal for anyone other than an election officer to handle, count, or canvass ballots under penalty of imprisonment. Sequoia technicians are not election officers.
Obviously, administrator privileges do not safeguard systems against tampering if the election administrator themselves, or even company technicians responsible for servicing voting systems and EMS databases, happen to be the attacker.
The protections against privilege escalation go unclarified.
System Integrity Protection
VVSG 2.0 § Section 14.3 specifies runtime protocols to regulate and minimize the chance that unauthorized and illegal software is installed onto a voting system, and that it is run and allowed to interfere with the normal operation of the system. These provisions deal with outsider attacks, and cannot protect against corporate or election insiders.
VVSG 2.0 § Section 14.3.2 imposes the requirement that the voting system authenticate purported software updates before installing them using their digital signature. A message digest is computed from the software package and subsequently encrypted using a private key to generate the digital signature, which is attached to the package and decrypted by the recipient to regenerate the unencrypted digest, which is compared to a new digest, computed using the same algorithm as the initial computation, and the two are compared to verify that the message wasn't intercepted and tampered with during transit.272
This is important because all existing voting systems273 that have been subject to penetration testing exhibit weaknesses to having their software replaced by technically-skilled voters, poll workers or election administrators with any measure of physical access to the machine in question, and a memory card, flashdrive or other compatible electronic medium containing malware.
The extinct Diebold AccuVote-TS paperless direct recording electronic voting device was discovered to have vulnerabilities that meant it could be hacked within the span of a minute with brief physical access and malicious software stored on a commercial-off-the-shelf memory card. Upon startup, its bootloader copies itself to RAM and initializes hardware, then checks for memory cards installed into the first PC slot and, if a file called fboot.nb0 is present in the card's storage, the native bootloader assumes that this is a replacement bootloader and overwrites itself with it without first validating its authenticity. In the Princeton hack, the bootloader is superceded by a viral bootloader which creates a copy of the vote-stealing application on the memory card, which then renames and sequesters the original BallotStation executable and swaps it out with itself on flash memory. From there the application can be set to manipulate vote-counts during voting and do so secretively and, due to the machine's lack of a paper audit trail capability, completely without risk of detection, and nothing about its design — protective counters, audit logs, vote-count encryption, etc. — would impede the malware's function.274
Similarly, physical and digital security measures for the also extinct ES&S iVotronic direct recording electronic device were designed poorly and could easily be bypassed. The compact flash port is protected by a locked sliding panel, but that protection can be bypassed by temporarily disassembling the DRE's terminal housing. The disassembly can be carried out using an off-the-shelf screwdriver, and, once the housing has been removed, the internal flash chip can be removed from its socket, reprogrammed with a standard flash writer, and replaced,275 or alternatively the drive can be swapped out with an infected copy.
The ES&S M100 performs a self test of its operating system on power-up, and checks for a properly formatted flash card in the PCMCIA slot. The PCMCIA card is mapped directly into memory, and portions of it are copied into RAM for faster access. This is to aid in delivering firmware updates since the memory card was, among other functions, used to deliver updates.276 Because of this, anyone with correctly formatted software loaded on a PCMCIA card could easily modify the existing software present in the M100 optical scanner as it neither asked for a password nor did it authenticate the software being downloaded cryptographically.277
On startup, the ES&S M650 batch-fed optical scanner boot manager, not dissimilar to the Diebold AccuVote-TSx, ascertains the presence of a designated firmware update disk entered into the onboard Zip disk drive and, upon identification, searches for three files. If these files exist and the reported version number is disparate from the installed firmware version, the firmware installer script is executed and the new software, not subject to integrity checks or authentication by the device, is copied onto memory and overwrites the current version.278
More recently, open ended vulnerability testing conducted on the Dominion ImageCast X ballot marking device presently certified for use in the state of Georgia and counties in thirteen other states is vulnerable to similar attacks. The BMDs have multiple USB ports used for tethering printers and receiving election definition data injections from a thumb drive, with all of the assorted vulnerabilities, which are externally located though statutorily required to be protected by tamper-“evident” seals during use at a polling place under the laws of Georgia and elsewhere, but, again, these seals can be easily subverted and bypassed with off-the-shelf tools and, when they are discovered in the breach, it is typically attributed to human error rather than as evidence of tampering. More importantly, as they were deployed in 2020 and likely 2022, the ICX is tethered to a ballot printer by a USB cable that lacks such sealage. The cable could easily be unplugged from the printer, undetectably if done quickly enough, and connected to an adapter and then a USB thumb drive infected with malware. The voting machine does not, or did not, adequately restrict the devices that can connect to it to certain models of printer, or proprietary flash drive models.279
In this voting system attack scenario, a single unscrupulous poll worker — in many jurisdictions they may or may not be subject to security screening, and there are a lot of poll workers recruited for political means, especially as of late — that is in possession of an infected memory card or results cartridge, out of the many dozens or hundreds staffing county polling places, can infect every voting machine and tabulator in every precinct across the span of an entire county with physical access to only a single voting machine for only a short period of time, because, as alluded hitherto, at some point over the course of pre-election preparation and post-election vote-count aggregation, infectible memory cards are administered to each voting machine in a county and delivered either to each other or a election management computer. Notably, this is an attack, relying purely on the transfer of physical hardware, does not depend on whether or not voting machines are ever connected to the Internet or any local area networks.
These attacks can be carried out without deploying a single “trojan” election worker, too, if the jurisdiction fails to preserve memory card chain of custody or execute basic cybersecurity functions. This is not an idle concern, either; for example, in 2006 Cuyahoga County, Ohio election workers uploaded election results from Diebold voting machine memory cards to regular, off-the-shelf home or office laptops in order to archive election information. These laptops were not screened for malware, possibly not adequately protected from malware, and most likely connected to the Internet.280
The result are events like the midsummer 2008 St. Pete Beach, Florida incident, where, just before the municipal referenda, poll workers discovered the computer worms Flush.G and W32.SillyDC, which replicate themselves onto target computer software via removable electronic hardware, to have infected Pinellas County's central tabulation system.281
The worms themselves were benign and not programmed to specifically corrupt election results, and, as a result, quite easy to detect (and this was the only reason why they were detected), but malware designed for the expressed purpose of compromising vote totals can very easily be hidden from the lackluster security practices of current election administration. Under the (generally known to be unreliable) assumption that voting systems are completely disconnected from the Internet, the only way a situation like this could happen is if it were introduced over the course of manufacturing or testing, or was the culmination of an election insider attack or violation of chain of custody. Both possibilities are unsettling.
Even if this provision is twenty years too late, but the effectiveness of its execution is predicated solely on the competence of the voting system vendors who are implicitly entrusted, incorrectly, to mediate the summary execution this provision. For most voting systems (such as the ImageCast X) the private key used to encrypt voting data and other internal records generated during an election is standardized across all such systems in a county, or even in the country. It would not entirely be surprising if encryption is once again deployed incompetently and the private key used to digitally sign documents is the same for all software packages created by a given company, and an attacker might be able to compute and encrypt a new digital signature after tampering with the original update package.
If ballot definition programming is cryptographically signed, and it usually isn't, and programming is prepared by county administrators, then the private key used to generate ballot definition digital signatures might be imagined to be stored in the EMS itself, and all outputs are thus, by definition, authorized and authenticable irrespective of their legitimacy, legality or honesty. For most jurisdictions across the country election programming and software updates are developed and administered centrally by vendor corporations, and in other configurations election programming and services are dispatched by associated subcontractors. A malicious payload could be ‘grafted’ onto software update packages by breaching the update preparation and publishing infrastructure of these companies.282283 Such software packages are by definition digitally authenticable and authenticated, even after manipulation.
Similarly, § Section 14.3.1 outlines a requirement that the operating system must be cryptographically validated by the bootloader upon startup. Amazingly, the subclause explicitly does not mandate the elimination of the possibility of the unauthorized substitution or modification of the bootloader itself.
Interdiction of Insider Malware Packages by Testing Authority
For most purposes avoiding the detection of testing authorities is superfluous since malware can be deployed after election equipment reaches the customer, perhaps during voting, or logic and accuracy testing (next section), when voting machines and election management systems are often configured to connect to the wider Internet. Ballot definition files are not subject to certification testing. There are, however, contests where embedding malicious logic into the programming of polling place voting machines or tabulators are desirable, and designing these scripts to dodge inspectors during certification in mandatory. So, how may holes in the certification process manifest, and be exploited to further this end?
Disregarding the commercial operating systems that they are built on, the source codebases for voting system software suites usually consist of hundreds of thousands of lines of heavily abstracted and parameterized code, the purpose of certain executable blocks sometimes not being immediately clear to reviewers or even the engineers that designed them. Ensuring that complex code packages are free of bugs, vulnerabilities or even tampering is next to impossible, though it seems that VSTLs aren't particularly effective at catching systemic vulnerabilities prior to approving these systems for certification.284
Inadequate provisions inculcating testing doctrine for the examination of source code translator programs exist and are specified by VVSG 1.0.
Source code is abstracted, human-readable plain text used to design and build executables, and is not directly executed by computer programs to control operational logic. It must be processed by a translator program — compiler, assembler, or interpreter — into low-level machine binary or an assembly language which is then executed by the computer program, though interpreters directly execute translated source code.285 A commercial-off-the-shelf compiler, which is exempt from software checks as clarified in the lede to VVSG 1.0 Volume II § Section 5.2, that is designed to insert malicious machine logic into the source codebases it is translating can easily evade inspection by VSTLs and unthorough investigators.
Indeed, only COTS compilers can be used to compile code. Nothing prohibits the vendor from establishing a shell corporation and charging it with the task of designing, and subsequently getting certified elsewhere (inapropos to election security), “commercial-off-the-shelf” compiler code for their voting system. No changes need to be made by the vendor themselves to the COTS software that they cannot command their puppets to deliver for them, and as such VSTLs won’t inspect.
The 2005 Brennan Center for Justice report The Machinery of Democracy: Protecting Democracy in an Electronic World describes such an insider-propagated attack using a bootstrapping compiler286 as follows:287
But what if, instead of inserting the attack into the vendor’s source code, our attacker inserted an attack into the compiler (which is generally a standard software program created by a non-voting system software vendor)? Under these circumstances, the compiler could take harmless human-readable source code and turn it into malicious binary code without any inspector being the wiser. As a compiler is generally COTS software, it would not be inspected by the ITAs.
In any event, the attacker could hide the attack program in the compiler by adding one level of complexity to her attack: make the compiler misread not only the seemingly innocuous vendor source code (which would be converted into malicious binary code), but also the seemingly innocuous compiler source code (which would also be converted into malicious binary code, for the purpose of misreading the vendor source code). In other words, the attacker can hide the attack program in the same way that she might hide an attack program in other software: change the human-readable compiler source code so that it does not reveal the attack. When the compiler “compiles itself ” (i.e., turning the human- readable source code for the compiler into computer readable binary code) it creates a binary code that is malicious, but cannot be detected by human inspectors.
Federalism, and the delegation of powers not reserved for the federal government but to those of each of the fifty states, results in a system that is geographically complex and technically labyrinthine, and an idealist with vote-rigging capacity, who wants to reshape America into their vision, will have to rig a large portion of these — from the pool of 7,386 legislative seats across 98 bicameral legislative chambers and one unicameral,288 fifty governorships, alongside 435 House seats, 100 Senate seats and one presidency — to tilt the balance of power into their own court and establish a working “mandate”. This, of course, does not concern the multitude of state Supreme Court and circuit court seats subject to popular contest, the Attorney General races, county or township governments with their own minor stakes, and so forth.
Individually pulling a successful caper on these races is quite easy since few elections for seats in the House of Representatives or a state legislature are polled, analyzed, or subject to any other form of public scrutiny. Stealing all of them, on the other hand, is logistically complicated. Designing and distributing a new software “fix” to each county before each election of import to knock off every seat desirable to the insider is certainly possible but introduces too many points of potential error, leading to one's hack failing and being exposed. Hence, they might opt to design malicious vote-counting logic into the software itself, that can be activated under any set of parameters generic to an election they would want to steal (such as the Party ID of the candidates), or perhaps activated by those aforementioned “fixes” that, now, simply turn a switch ‘on’ or ‘off’ rather than rewriting the code wholesale.
Take, for example, the curious functionality built into central tabulation systems called “fractionalized voting” that might be activated by either administrators or internally, where recorded votes are assigned non-integer decimal values rather than whole numbers as one might consider normal, weighting votes and allowing insiders to easily shuffle votes between candidates in seconds, with little effort or chance of detection. It was first described289 by activists Bev Harris and Bennie Smith in 2016 with respect to the Diebold Global Election Management System, used by all jurisdictions that contracted out to Diebold or used their legacy equipment,290291 but similar functionalities are used in systems designed by ES&S, Dominion and Hart Intercivic.292 With exceedingly few legitimate uses, such as in rare land-use elections, its quite a convenient tool for election fixers.
Such a program would have to pass certification and, as we can see, source code review practices are unlikely to detect that program.
Modems and Internet Connectivity
Precinct voting systems are often equipped with Internet-facing cellular modems or WIFI-enabled memory cards for the purposes of receiving system updates or programming from the central county election office or an election vendor, or for disseminating official or unofficial election results to the county’s central tabulator, thereby turning the voting machines into a node on the Internet.293 Nonetheless, it has been rehashed ad nauseam by officials charged with the weight of the public trust that voting machines are not connected to the Internet and are thus unhackable.
Votes stored on memory cards are ideally transferred to election management systems, canvassing computers or reporting units by being uploaded to a removable storage medium such as a flash drive, which is driven to the county central election office, but many jurisdictions across the country opt to fit their optical scanners or touchscreen voting machines with modems to transmit unofficial or official election results to an SFTP server situated beyond a network firewall non-locally instead, depending on the configuration of the network. The EMS/reporting unit reaches out to the server, collects and tabulates the votes.
More specifically, both the ES&S DS200 and M100 hand-fed optical scanning tabulators, the former utilized at present over hundreds of counties across more than a dozen states, can be configured with a advanced Verizon Multitech MTSMC-C2-N3-R.1 commercial-off-the-shelf digital cellular modem to upload unofficial Election Night results to a centrally located county canvassing computer or election management system for quick reporting of election results. The number of modem-equipped DS200 tabulators that ES&S estimated were in service in 2018 were 33,000 across eleven states,294 including Wisconsin,295 Rhode Island,296 Florida297 and Illinois,298 with at least 14,000 configured to transmit vote totals wirelessly, sometimes on for days or months on end, and the market share of the model has only grown since then.299
Similarly, a Michigan contract document for the Dominion ImageCast Precinct optical scanner discusses how counties could outfit the Democracy Suite election management system with a TCP/IP data transmission protocol server called the ImageCast Listener to collect election results.300 The older Sequoia Edge DRE and Optech Insight optical scanner could be fitted with a Hybrid Activator, Accumulator, and Transmitter Model 100 device that transmits unofficial results over a Verizon CDMA 1X cellular network to an EMS server.301 Other machines, manufactured by smaller, more obscure companies, such as the deprecated Advanced Voting Solutions WinVote direct recording electronic system, also had modems that can dial out to the Internet. In fact, one analyzed machine had logged modem activity as having dialed out to unknown addresses during the 2005 Virginia gubernatorial election, and broadcasted pop songs over the Internet.302 Hell, you could even hack into its wireless connection with a smartphone.303
Other legacy systems may also be equipped with digital cellular or analog modems. All such Diebold AccuVote-OS precinct optical scanning tabulators were equipped with an analog modem that, if county administrators so elect, can communicate unencrypted/unauthenticated preliminary or official vote totals scanned by that device over a public telephone network to be received by a GEMS EMS computer at the county central election office or, in those counties that administer elections in this manner, at a regional return center election management computer. In regional processing counties the client GEMS computers can dial up the master GEMS database over an SSL-encrypted phone line connection if connected to a modem bank, which are set up to accept phone calls from any given source provided that that source knows the right phone number to dial, and can supply the right username and password. There are no technical specifications preventing the Diebold modems from being configured to permit communication over the public Internet.304
Since the connection between the AccuVote-OS and the GEMS was unauthenticated then it was possible for an attacker to reverse engineer the GEMS communication protocol and impersonate a GEMS client to redirect telephone traffic to them, giving them free reign to edit and modify the data fields of the optical scan memory card as they need, possibly infecting it with malware or modifying vote totals.305
The Hart InterCivic voting system examined was set up in a similar, slightly more secure fashion.306 These vulnerabilities as they manifest are not exclusive to these systems.
Most landline modems are gone and are now superceded by advanced cellular modems that interface, directly or indirectly, with the Internet. Any remaining systems that still are equipped with landline modems are unlikely to be truly “air-gapped” because analog traffic likely passes through the digital, cellular routers that have replaced older analog switching equipment in the modern era.307
VVSG 1.0 acknowledges the use of public telecommunications networks for the transmission of vote totals, and the consequent exposure of system and data integrity to compromise, but does not prohibit the installation of modems for this exact purpose. Instead, specifications admit provisions for the maintenance of election data integrity using error correction methods such as checksums and message digest hashes, cyber threat monitoring and detection, general response protocols, and various other computer security measures that voting system vendors never adhere to and the EAC never enforces.308
The initial draft for the Voluntary Voting System Guidelines 2.0 manual included a provision disallowing the physical presence of external or internal wireless networking hardware such as cellular modems in voting equipment,309 but after extensive backdoor canvassing of voting system vendors' opinions this requirement was attenuated to allow the presence of such networking technology so long as the vendor could demonstrate to the voting system test laboratory that the technology was disabled, apparently loosening election security in order to appease the cost-cutting desires of vendor corporations.310311
This means that insiders and hackers who gain access to these machines through hacking the county election management system or by compromising removable electronic media can still configure them to dial out to whatever IP address or phone number is associated with the attacker to allow them the ability to fine-tune and optimize vote theft in real-time, along with easily configuring the machines to cheat in future elections. And granted, these vendors often lie and the EAC has demonstrated a complete unwillingness to punish them for going against its own regulations, meaning that it's not unlikely that they'll reactivate Internet connectivity again during voting to report votes faster and satisfy the impatient whims of election officials.
Other provisions were weakened or eliminated, namely, the removal of the requirement for all voting systems to provide data reports that account for all cast ballots and all valid votes at the termination of a given election; removal of a transparency requirement granting public access, without an explicit request, to any cryptographic end-to-end protocol submitted for certification, for open review for two years before it enters the voting system certification process; limitation to voter-facing devices of the logging requirements for backend voting systems to record external connections or disconnections during the activated voting state; removal of a standard for physical locks installed in voting machines; removal of the requirement that all physical security countermeasures which are reliant on electrical power log incidents of power disruption; removal of the requirement that systems be expected to have a life span of 10 years; and removal of the ban on printing voting machine vendors’ advertisements on the ballot.312
Acceptance Testing
The final step in the process of the deployment of voting systems is acceptance testing, conducted after the examination by an independent testing authority and formal certification by the Election Assistance Commission. Authority and responsibility for executing this important task is charged with the chief election official of the jurisdiction that purchased of the voting system for field service. It is designed to determine if the system is physically, electronically, mechanically, and functionally correct; that is, that the voting system is the same as the one certified and purchased, and is in working order.313 As such, it is necessary for acceptance testing to be conducted independently of vendor corporations, though sometimes the vendor compels jurisdictions to delegate this duty, defeating the very purpose of this species of testing.314
One of the tools used for this ascertainment is hash validation. Conceptually, the inspector generates a hash code for the software installed on the machine and the corresponding certified software version using a hash function, and then they compare them. If there is a discrepancy, due to clerical errors, unauthorized modifications by the manufacturer or even malware, then the hash validation process will detect and flag it.315
For example, vendors have been observed deploying uncertified and unauthorized system patches, often without supervision316317318319 but sometimes at the behest of state officials.320 Just prior to the 2002 primary election in the state of Georgia, Diebold, which the state had contracted out to months earlier to administer their elections and replace their older voting equipment with unverifiable touchscreen DREs, had dispatched company technicians in the early morning to avoid detection by state or county officials, and deployed an unauthorized memory card software patch to over 5,000 AccuVote-TSx units that were slated to be delivered to Fulton and DeKalb County for the primary elections. Supposedly, the patch was a fix for the systems’ internal clock, but the timekeeping function was still not working even after the patch was applied.321322
Again, just before the 2002 general election, Diebold had instructed its subcontractor Automated Business Systems and Services to administer a software patch to the 19,000 machines it sold to the state without certifying the patch or recertifying the machines, or alerting public officials, which are illegal. The patch was allegedly supposed to fix a bug that resulted in machine failure rates of 25-30% when subject to pre-election testing by Kennesaw State University, but the patch did not eliminate the source of the problem, nor did it even ameliorate it.323324
On the onset of the 2012 presidential general election, a contract325 was signed between ES&S and Ohio Secretary of State Jon Husted to distribute an uncertified, untested update of the company’s Election Reporting Manager’s Results Export Program, an election management application that coordinates precinct-level results reporting, for the central tabulators of thirty-nine counties that are home to more than four million registered voters. This patch was designated as ‘experimental’,326 permitting bypass of standard state and federal testing and certification procedure.327328329
Requirements necessitating the certification, by testing authorities and the Secretary of State, of direct record electronic voting machines, electronic ballot marking device, automatic tabulating equipment, software used for the purpose of casting or tabulating votes or for communications among such systems and documentation governing the governance and administration thereof, can be waived conditionally by the Board of Voting Machine Examiners if they grant temporary approval by designating them as “experimental” under Ohio Revised Code § 3506.05(B).330 O.R.C § 3506.04(B) further clarifies that county boards of commissioner can lease that voting equipment for a “limited number of precincts” (most generously interpreted to be less than the total number of precincts in the county) for demonstrative purposes.331
As such, the terms of the contract likely render it illegal. The deployment patch influences the conduct of the election in hundreds, or even thousands, of precincts across the state, as central tabulators aggregate vote totals reported by precinct electronic voting systems in every precinct across the serviced county.
In situations like these it is imperative that counties possess the faculties to detect such behavior and lay down charges.
But hash validation testing has its issues which lend it little probative value in the determination of deliberate fraud, and isn't entirely taken seriously by election security experts. There is nothing stopping a program, embedded in the machine subject to examination, to simply misreport the hash code of the original program as being the code corresponding to itself, so that the malicious software always reports back as matching the certified comparative.
Such vulnerabilities are manifest in the Dominion ImageCast X BMD certified for use in the state of Georgia and elsewhere; the generation of SHA-256 hashes are coordinated by the ICX app itself, which can be compromised to always produce the hash code of the unmodified software APK.332 Another hash validation technique, where the APK is exported to an external USB stick where hash validation can be done independently of the device. Of course, this export is performed by the ICX app itself, so again it can just be configured to export the original, unmodified APK.333
But this inadequacy simply was not enough for ES&S and they managed to create an entirely new hash code validation tool for the EVS 6.1.0.0 and 6.1.1.0 system that is decked crown-to-toe in security violations and effectively automated the above stated misreporting process, such that hash code testing cannot even be used to divine non-malicious procedural errors, because when the reference hash code is missing the hash checking tool will report that the installed system matches the certified version anyways.334335
And so, the end result is such that election vendors have virtually unfettered ability to deliver completely unauthorized and uncertified “upgrades” to their voting systems and test labs/election officials will be entirely unaware of such a transaction having even transpired.
4. Pre-election Testing
Logic & Accuracy Testing is the routine procedure counties go through prior to an election to locate and redress errors relating to the fidelity of election definitions logged onto machines, ballot designs, ballot language, any missing races, absent or erroneous party identifiers, incorrect or faulty tabulation, touchscreen device printing and other menial issues. It also identifies technical issues relating to faulty election supplies and memory cards, and ensures that zero counters and memory have been wiped of data pertaining to previous elections. After this process is finalized the county will certify the L&A testing and summarize their findings in a report for public inspection.336
L&A testing, of course, has a critical function in ensuring the smooth administration of elections, and when counties don't do it, things tend to proceed poorly. When done right, the routine process allows jurisdictions to interdict and preempt procedural errors before they have a chance to become a problem, but the benefits end there. As for safeguarding elections from very deliberate fraud, it should provide no solace, because machines can be programmed to only misbehave when machines’ voting mode is active (“Dieselgate”337-style hack), so L&A testing has no hope of catching vote flipping in the act.
5. Auditing Election Results
“When a measure becomes a target, it ceases to be a good measure” — Goodhart’s Law, summarized.
Broadly categorized, there are three types of voting machines used by voters in the United States: optical scanning devices (opscans), direct recording electronic devices (DREs), and ballot marking devices (BMDs). Modern BMDs are sometimes referred to as electronic ballot markers (EBMs) to distinguish them from card punching machines which also serve the purpose of marking “ballots” and were historically known as ballot marking devices.
Optical scanners accept paper ballots, either marked manually by pen and the voter’s hand, or by machine. These ballots are inserted into a slot, which are rolled past a scanner head and deposited into an attached ballot box for further canvassing or adjudication. The scanner head generates a digital ballot image,338339 which is an internally stored, electronic interpretation of a physical ballot, and image analysis software associated with the tabulation program determines ballot image scale and orientation using fiducial marks or index marks printed on the ballot sheet before searching for ballot positions and assigning voter intent to the voter mark taxon found on the ballot. The tabulated votes screened from a ballot image are organized into a tabular format on a cast vote record, and votes are added to a running total in memory.
The digital ballot image, along with the associated cast vote record, may be destroyed by the tabulation program shortly after creation, thereby breaking the chain of custody of the physical ballots, or retained (or rescanned) and permanently exported, where they will be transferred to the EMS and uploaded for use by researchers and auditors, protected by public records laws. Most jurisdictions opt to destroy them.340
Direct recording electronic voting machines are classified as touchscreen machines,341 which in a purely technical sense are the only kinds of “electronic voting machine” since voters do not utilize optical scanners to vote, only to count them. The voter defines their voting selections on an electronic ballot displayed on a glass screen, and, after confirming their choices and casting their electronic ballot, their selections are directly recorded into an electronic storage medium like a memory card, diskette, smart card or cartridge. Legacy direct recording electronic voting systems do not have the capability to print out voter-verifiable paper audit trails (VVPAT), which are physical records generated by the system that is intended to capture voter selections for auditing or recounts. Modern systems do.
The other type of touchscreen voting system, the ballot marking device, which is directed by a voter to, like a card punching machine, print voter selections automatically onto a “paper ballot” or a summary card. Depending on the model, votes may printed in parallel as barcodes/QR-codes, which are what is processed by tabulators and are not verifiable by voters (and are unanimously known by cybersecurity experts to be irresponsible342), and the fault human-readable plain text, which, much like DRE VVPATs, is theoretically verifiable and subject to verification by a voter. However, the BMD does not tabulate votes, and the paper trail is meant to be handled by the voter and scanned by an optical scanner.
One type of BMD, the hybrid ballot marking device, instead combines the functions of an optical scanner and BMD by, in the marking setup, accepting a blank ballot, while asking the voter if they wish to inspect the ballot. If they do not, then their selections are (hopefully) printed onto the ballot successfully, internally, before being scanned by an internal optical scanner and deposited into an attached ballot box.343 In the scanning setup, a voter can mark their ballot and run through the slot, down the conveyor belt and past the print head, to the scanner and into the ballot box. Obviously, this configuration is exceptionally insecure for two reasons: one, casting machine-marked ballots without first getting the opportunity to inspect them violates the very principle of voter verifiability, and essentially gives the machine “permission to cheat” since it now knows that it won’t be scrutinized, and cannot be verified afterwards.344 Secondly, running the ballot past the print head gives the machine the opportunity to add new votes to the ballot.345 Hybrid BMDs include the ExpressVote (optionally) and ExpressVote XL,346347 to which criticism was levied that ES&S did not take very well,348 and the ImageCast Evolution,349 which was also criticized and to which Dominion countered with a very impotent and ephemeral response.350
Optical scanners have the perk of increased voter throughput because multiple voters can mark their ballots in parallel, and feed them into the same ballot scanner. Meanwhile, since voters must determine their choice at the voting booth, to emulate this with a touchscreen voting configuration, the polling place must be equipped with multiple machines, which is cost-prohibitively expensive. Else, bottlenecks and long lines are created.351 In general, optical scanners are cheaper than touchscreen voting machines.352353 However, optical scanners are not necessarily accessible by certain classes of voters, and thus to achieve ADA-compliance (as well as fulfill HAVA requirements) polling places have at least one touchscreen voting machine for accessibility.
As of 2024, 69.6% of registered voters who vote electronically reside in jurisdictions that provide for the option to mark ballots by hand and optically scan them, or use either BMDs, DREs with VVPAT or paperless DREs for accessibility purposes. 25.5% of registered voters are exclusively allocated polling place ballot marking devices for in-person voting, and another 4.9% of registered voters vote exclusively on direct record electronic devices for in-person voting. Louisiana and two counties in Texas use unrecountable DREs for all voters. A plurality of counties in Nevada, Indiana and Tennessee, along with some counties in Ohio, New Jersey and Utah use DREs configured to produce VVPATs for all voters. Some counties in Pennsylvania, New Jersey and Ohio use Hybrid BMDs for all voters. All counties in Georgia and South Carolina, most counties in Texas, Arkansas and West Virginia, and some counties in Nevada, Indiana, Nebraska, Ohio and eight other states use BMDs for all voters.354
80.4% of absentee ballots are counted by batch-fed optical scanning tabulators, 19.4% are counted using hand-fed polling place scanners, and the remaining 0.2% are counted observably by hand.355
Since BMDs and DREs digitize the process of voter creation, then the paper audit trails they produce are not considered to be strongly software independent,356 and do not provide convincing evidence attesting to any particular outcome when subject to recount or manual audit. This is because hacked software can direct the on-board or connected printer to doctor physical evidence corroborating bogus outcomes which, if these deliberate errors go undetected then the true election results are unknown and unknowable. If the error is detected by the voter then they cannot conceivably prove that it was machine error and not human error at fault.357
As computer security hazard and tampering prevention cannot be reliably automated, meticulous verification of printed machine outputs by voters to stave off the potentiality of an unrecoverable attack. However, studies have demonstrated that voters rarely review machine print-outs, and when they do they rarely detect errors. The voter-verifiable paper audit trails printed out by direct recording electronic devices are considered untrustworthy and unauditable.358 Voters rarely detect vote flipping on easy-to-interpret touchscreen review screens before casting their vote;359360 more fail to adequately verify the paper audit trail print-out.361 Even if the voters are privy to the existence of a printing irregularity, less than one in ten were willing to accept a new ballot and try again.362
The paper trail can get jammed in the printer, or they can degrade due to averse environmental conditions, or they can tear, and so forth, rendering any print-outs illegible and necessitating that poll workers reprint the trail from computer memory — defeating the very point of “voter-verifiability” and ensuring that no-one has the ability to verify whether or not the paper trail mirrors voter intent.363364365
Similarly, less than half of voters adequately inspect their ballots absent poll worker ‘encouragement’,366367 and few successfully detect surreptitious modifications to the ballot or card.368369 These issues violate the assumption fundamental to the administration of valid audits and even recounts, that the record itself is trustworthy. As 31% of registered voters live in jurisdictions that distribute unverifiable touchscreen machines for all in-person voters, then the determination is that these votes are not printed on a reliable, trustworthy audit record, if at all.
But these metrics assume homogeneity of voter verification/error detection rates across all demographics, but this is likely not the case. Thus, the chance of the voter detecting unauthorized modifications to their ballot can be pared down even further by targeting certain vulnerable demographics, by looking for certain parameters characteristic of a demographic that is the least likely to review their ballots — these parameters are sometimes known as “secret knocks”: subtle (yet perhaps common) inputs unlikely to be included in a testing procedure by authorities, that activates the malware.370371
Modern ballot marking devices cannot currently provide for the verification of ballots by voters with visual impairments. Approximately 0.8% of the U.S. population is legally blind, while approximately 2% of adults ages sixteen through sixty-four have a visual impairment.372 If the attacker only alters votes when the voter uses the audio interface or large fonts, detection may be very unlikely.
Most modern ballot marking devices do not print in languages other than English, meaning that voters who are not comfortable with that language might be hypothesized to be dissuaded from analyzing their ballot. If voters who use a foreign language when interfacing with the BMD touchscreen happen to be unlikely to check the English-language printout, an attacker could change votes with little chance of detection. Areas with significant populations of first-generation immigrants, such as urban areas, might be appealing targets for unrecoverable fraud.
The ballot marking device can measure how long it takes for a voter to go from initiating the voting session and terminating it, casting their ballot. Voters who take anomalously long to cast their ballot might be theorized to be unfamiliar with the voting system, and thus unlikely to inspect their ballots. Contrariwise, voters who are extremely quick with casting their vote might be imagined to be less likely to thoroughly inspect their ballots.
The specifics of the parameters, how they come to be in a jurisdiction of a certain demographic make-up and work to the benefit of the attacker and detriment of the auditor, will probably be determined on the county-level, and based on past elections. Because voter privacy and ballot secrecy, which is easily breached due to the digitization of elections, is likely not a problem for an already criminal and amoral election rigger, and they could've built a database of voter characteristics and behaviors attributable to that county or precinct that are the least likely to review their ballots, and, for future elections, deliver a malware payload, or adjustment, that flips votes based on that particular characteristic.373
The number of serviced touchscreen machines in the state of Georgia north of 22,000; ES&S advised that 27,000 ballot marking devices would be optimal for its slightly-over 7,000,000 registered voters.374 Assuming 100% voter turnout, and 100% usage of voting machines, that’s approximately one machine allocated to 260 voters, and if one vote is flipped for every fifty cast votes then that is roughly five votes per machine, or a net shift of 108,000 votes (nine times the reported statewide presidential margin of 2020), and, even under optimal conditions of a 20% error detection rate, 100% voter verification rate, and 100% reporting rate, only one vote flip will be detected per machine and reported, which is indistinguishable from error.
Parallel testing,375376 or live auditing, has been variously proposed as a solution to this problem, in that it seeks to authoritatively divest the responsibility of paper trail verification from the voters and to election administrators. The essence of the parallel test is conceptually much like a logic & accuracy test, except, unlike an L&A which can very easily be bypassed due to its very structure, the parallel test is conducted during an election, during voting, where presumably an active hack is doing its work. Per the hypothesis, the hack lacks the disposition to know when it’s being observed, and, when test ballots are marked by the machine, if it is assumed that votes are flipped independently and stochastically with a uniform probability p, then it can be determined that the chance of detecting a flipped vote after n tests is 1 - (1 - p)^n. Assuming shift of 5% of all cast votes for a race (p = 0.05) and 100 test ballots, there will be a 99.4% chance of detecting one vote flip.
But, as implied above, an attacker’s hack need not steal votes purely uniformly or randomly. The Volkswagen emissions scandal demonstrates the practicality of designing computer programs that fine-tune outputs that conform to the expectation or regulations of the tester in accordance to indirect parameters that impute the inference of active examination, even in the absence of explicit validation of the fact that the system is being tested. Accordingly, an attacker could design malware that searches out for signs of testing, or to only flip votes adhering to an obscure set of parameters not necessarily known to, or replicable by, the auditors — creating a dimensionality problem that is difficult to overcome.
There's another problem: the malware could be programmed to only steal votes the busiest times of day, impeding any live tests. Even without fixed epochs where parallel testing is known by outsiders to be run, testing can still be deterministic, only occurring when voter activity is low enough so as to not interfere with the democratic process in any way. When the number of votes being printed off/processed falls below an estimated mean value, the vote flipping algorithm might self-deactivate, to avoid being exposed. If they do conduct parallel testing during busy hours, then the auditors run the risk of disenfranchising voters, or even degrading trust in the system by igniting suspicions that the test ballots are stuffed ballots.
Compounding this inefficiency issue is the fact that marking ballots using touchscreen machines takes a long time to do for every single such ballot. To reduce this workload, poll workers must either vote for only one race, or a few races (and the malware then is programmed to only flip votes on ballots with few undervotes), or they can vote straight-ticket, but of course the attacker only flips ballots with at least one undervote, or with races filled in manually. They can fill in votes randomly, but again more clever viruses can be set to only flip votes on ballots with certain semi-common voting patterns, or obscure voting patterns, or a specific number of votes, and the targeted ballots only are represented as a small set of randomly filled-in ballots, with flipped ballots being an even smaller subset, reintroducing the dimensionality problem.
Thus, parallel testing, which is not done by a single known jurisdiction, is unlikely to fix the issues inherent to touchscreen voting, and they are likely to remain unverifiable.
Optical scanners, by contrast, are often mischaracterized as being more secure than electronic voting machines or, worse, entirely, capital-‘S’ Secure, but they are neither and that is impossible. What hand-marked ballots, paired with optical scanners, are, and what EVMs are not, is verifiable.377 There is an beseechment of blessing that votes are recorded correctly, or recorded at all, that is implicit with the use of touchscreen voting systems that simply does not have to exist for optical scanning systems since there is a paper record, created by the voter, that is independent of the debatably benign or even functional software of the voting systems, that can be examined by hand if need be. The scrutiny pivots to the appraisal of the basis upon which the determination to examine paper ballots is made, the procedures the jurisdiction has determined to be applicable in the conduct of an examination and, whether the promise that paper ballots can be audited or recounted is justifiable.378
It is crucial to ensure the trustworthiness and authenticity of the paper ballot trail inasmuch as it is imperative to ensure that the creation of an accurate paper trail is possible over the conduct of the election. It would be conclusory to assert that a manual tally alone, without a comprehensive, statutory pre-audit examination of procedures (“compliance audit”), is able to conclusively establish the true outcome of a race without a shadow of reasonable doubt, especially in the scenario for which election fraud is assumed, where the deduction is that there is a considerable incentive to compromise audits and recounts to avoid detection.379380
In that sense, the audit of hand-marked paper ballots embodies certain issues that are primarily administrative in nature, where of principal importance is the promulgation of reasonable ballot chain of custody maintenance procedures: formal, tamper-evident and numbered security seals, standardized security paper for protection against ballot swapping, reliable ballot storage units such as bags or boxes, insurance that ballots are kept in secure custody and overseen by multiple people, subject to surveillance, rather than stacked up in weakly observed boxes in warehouses that any old partisan official can saunter into as they please (as they usually are); ancillary to these activities is the development of a comprehensive ballot manifest to keep track of ballots and the containers that they are secured in to avoid including ballots in the audit twice, or excluding them improperly, reconciliation of the number of voters to the number of ballots and counted votes, and proper accounting of voted ballots, blank ballots, the number of ballots ordered for the audited polling place(s) of each ballot style, validate absentee ballots signatures, and so forth.
Breaches of chain of ballot custody are unsightly, common381 and open up the possibility that ballots substitutions might occur. In the trodden course of the grand election heist any given race, subject to manipulation, that is marked for official inspection through processes known to be competently administered immediately imparts a variable degree of urgency for the rigger that their fix would be exposed, opening up the possibility for charges and even the development of a more secure, more observable system to exclude further heists.
Without chain of custody protocols, and associated measures to troubleshoot breaches, the assessment of the authenticity of the ballots being counted, that they are in fact sheets of paper filled in by actual voters and not by a loyal-to-the-cause activist official or burglar with unfettered access to elections materials and no shortage of replacement ballots, cannot be made.382 Likewise, even if the audit establishes the true winner it will be impossible to prove that that is the case. The utility and trustworthiness of the audit greatly diminishes, if not collapsing to zero, and has the opposite effect of inspiring yet more suspicion and a greater dearth of confidence. Unfortunately, it is often this critical step that jurisdictions fail to enforce.383
Other issues exist, namely the concentration of auditing authority within the purview of partisan officials, such as a state secretary, as is usually the case, or advised under the counsel of a partisan third-party or subcontractor, which is illegal but hasn’t stopped county auditors in the past. They might then make non-random predeterminations that culminate in the selection of precincts or audit batches known to be clear of electronic fraud reconcilable to the will of the voters by a recount. It’s also possible, in those jurisdictions where precinct selections are made using a computerized pseudorandom number generators to create audit samples (most of them) to either predict the precincts that will be audited in advance, or even hijack the PRNG inputs to make its outputs more deterministic.
Of course it might simply be that the audits are structured to be non-random. A statutory post-election audit wherefor examination of absentee ballots is forbidden only serves to promote the exclusive manipulation of absentee ballots by hackers. For this reason, audits must assume an approach that encompasses all voting types, not just some. Or the audit procedure is simply security theater junk. This, of course, should be avoided.
Notably, state auditing protocols have failed in a number of these respects. That will not be explored too closely in this article384 though some aspects of this administrative failure will be demonstrated, however subtly, in certain studies for didactical purposes.
Around the presumption that these procedures are in place, a corpus of audits have been devised and debated over the years. The most elementary of these is the machine retabulation audit, which involves rescanning cast ballots and paper trails through the same or a different tabulator, usually a high-speed batch-fed optical scanner, and tallying the results for one or more races.
They’re fast, efficient, but also completely useless since they'll just be hacked again to produce the same results as on Election Day. At best, if the ballots are scanned by another tabulator brand, that one will correctly interpret voter marks that were unambiguous or invisible to the other scanner. Administrators might even uncover unscanned ballots.
There is also the standard hand count audit. Both of these are what I will refer to as ‘conventional audit’ protocols, and may be defined as a fixed-percentage audit, where a constant percentage of all auditing units (3% of precincts, 5% of voting machines, etc.) are audited irrespective of election margins or error rates uncovered in previous such audits, fixed-size audit, where similarly a constant number of auditing units (fifty precincts, e.g.) are audited irrespective of the total quantity of such audit units for the race being audited, and tiered audit, where statute modifies the baseline of the audit in response to error, for cases where states may repeatedly audit the same race, or the closeness of the race.
The most common manifestation of this particular audit battery is the fixed-percentage audit. Disregarding, for now, officials’ general propensity to sample precincts non-randomly and predictably to minimize the workload hoisted onto auditors (assuming their genuine attempts at random selection aren’t tainted by unconscious biases), the probability that precincts with hacked or erroneous reported vote totals will fail to be included in the sample can be conceptualized as following a hypergeometric distribution, so a 3% precinct sample audit (the most common sample size set for statewide or county-level audits) of an election where, for 100 precincts, 5% of precinct reports have been falsified, can be calculated to have an 86% chance of not auditing a single hacked precinct; for a 5% precinct audit that chance is 77%. The audit would need to select 45% of precincts to diminish the chance to under 5% that not a single affected precinct is included in the sample. For the rare states that audit more than 3% of precincts, they only go up to 10%. For a precinct population size of one-thousand, a 3% audit sample in a scenario where 3% of precincts are affected by a hack has a 39.55% chance of capturing zero affected precincts and 37.83% chance of selecting one.
As for whether or not this can detect actual fraud is, of course, a matter of administration. Again, as we will explore later on, ballot chain of custody is rarely adequately preserved (with some states like Minnesota being the exception that proves the rule), inviting opportunities for ballot swapping. And if selections are generated in some way that is predictable or even manipulable, then it is reasonable to assume that hackers are already anticipating auditors’ next moves and dodging them, or redirecting them elsewhere.
Additionally, following from the Georgia example from above, if instead of ballot-marking devices four votes across every ballot scanner were flipped, that would again amount to a shift of 108,000 votes, or a net margin shift of 216,000 votes, but if a given sample of machines were to be audited there would be a consistent shift of only 1.5% towards the aggrieved candidate. Will that be recognized as significant, or brushed aside as human or machine error?
There are also ballot image audits, which involve tallying, either manually or through use of a optical character recognition-based audit program, the votes recorded on the digital interpretations of scanned ballots.
This audit protocol is controversial in its utility to verify election returns because digital ballot images can be doctored by a computer vision-based program, not dissimilar to the optical scan tabulation program already in use, generally automatically.385 The only information that is needed is knowledge of the structure of the ballot, which is already provided through ballot definition files.
That's not to say that ballot image audits have no forensic utility, but simply counting them should not be expected to expose a rig that transfers, say, 5% of votes from Candidate A to Candidate B. The benefits are primarily analytical in nature; the doctoring process isn’t guaranteed to be seamless and so artifacts of manipulation might become obvious upon human inspection. A careful hacker might develop the program to, for example, avoid swapping votes on ballots marked with check marks, because check marks often spill out far past the boundary of the ovals and the program might be set to ignore all markings made some number of pixels past the boundary, so manipulation would leave incompletely transposed marks and artifacts.
This might result in check mark voters being less likely to split-ticket in some fashion then voters who fill in ovals properly, or having completely different (and even conventional) voting patterns or partisanship rates, when theoretically they shouldn't, generating a pretty obvious irregularity that is hard to explain away.
They can be used to diagnose poor, obfuscating and/or malicious ballot design, as well. For example, in the 2017 Alabama November election it was possible for voters to mark paper ballots with either a straight-ticket vote — even though, in the vast majority of counties, the only race on the ballot was the Senate special election between Roy Moore and Doug Jones — or to fill in the ovals manually, however, voters could possibly do both. If they did do both, then optical scanners are likely to parse these ballots as false overvotes; these errors can be remediated easily with access to ballot images.386
The last group of audits that are semi-regularly instituted by election jurisdictions are risk-limiting audits. The purpose of a risk-limiting audit is not to diagnose the general accuracy of the deciding margins of the election results, or the vote-counts at the precinct- or county-level, but rather to limit the risk that, should the outcome of the election be reversed by fraud or error, that the wrong outcome would be certified — or equivalently, provide sufficiently strong evidence that the reported outcome is correct. If the outcome is incorrect then the auditors escalate the audit into a full hand recount of the respective jurisdictions for which the audited race is on the ballot.387
The standards for the criterion of evidence of “sufficient strength” are quantified by the risk limit parameter, a percentage value which essentially encapsulates the maximum chance, or risk, that, in the event of outcome-determinative error, the audit will not escalate; in other words, the risk that false outcomes go undetected the auditor is willing to tolerate. A risk limit parameter of 5% means that, in the event of fraud, there is a theoretical 95% chance that the audit will detect it, and a 5% chance that it won’t. Higher risk limits require smaller sample sizes, and thus less work, than lower risk limits, which are more desirable and authoritative.
There are generally three types of risk-limiting audits: the batch-comparison audit, the ballot-level comparison audit, and the ballot-polling audit.
A batch-level comparison audit appears to be the most elementary of audits, and involves selecting audit batches collectively consisting of thousands of ballots and counting them by hand, and comparing the counts for each batch to the machine tabulation of those batches. This is the most common RLA, used in Georgia, Pennsylvania and elsewhere, but also the most labor-intensive, inefficient, and isn’t exactly telling; the only utility they have is, not detecting errors but rather by identifying disparities between the population-representative sample margin, and compare it to the reported margin. If, when interpreted to take precedence over the reported margin, the audit margin changed the outcome of generates significant errors in favor of the reported losers, then the audit may be expanded. Of course, if auditors use a poor sampling method, or go out of their way to oversample ballots for the reported winner or one of the losers, then it has no real value.
The related ballot-level comparison audit also involves comparing the voting system’s interpretation of individual physical paper ballots, such as a cast vote record or digital ballot image, to its corresponding ballot, identified using a serial number printed on both during the voting period and selected at random using a pseudorandom number generator. These are not possible in most jurisdictions, for reasons relating to, as usual, ballot secrecy issues, as well as those jurisdictions propensity to refuse to export CVRs and DBIs, but places in Colorado and elsewhere may optionally implement these strategies under law.
One of the definitions for the parameters of a ballot-level comparison audit is given in “Super-Simple Simultaneous Single-Ballot Risk-Limiting Audits”388 for a method that seeks to simplify the risk-limiting examination of all races featured on the ballot, though I’m citing a variant of that proposal. Suppose a disparity is identified between the manual tally for a given race and the voting system interpretation of it. We can define a diluted margin parameter µ as the ratio between the difference of the votes cast for the apparent winner of the audited race and the apparent second-place loser, such that the parameter is minimized, and total the ballots cast.389
An overstatement is defined as a disparity that shrinks the diluted margin by reassigning a vote from the winner to any of the losers (a two-vote overstatement, since it shrinks the diluted margin by two), assigning a tabulated undervote to any of the losers, assigning a reported vote for the winner to an undervote or overvotes (both of which are one-vote overstatements). A two-vote overstatement should be uncommon unless if in the event of mis-programming or fraud. Likewise, an understatement is a disparity that instead expands the diluted margin between the winner and every loser through the means described above.
Let n be the size of the sample of ballots that is being subject to the audit. Let u₁ and o₁ be the number of one-vote understatements and overstatements, respectively, among those n ballots; similarly, let u₂ and o₂ be the number of two-vote understatements and overstatements. Setting the risk-limit α at 0.10 and an “error inflation factor” γ at 1.03905, the number of ballot-level comparisons that auditors are required to conduct is defined by the inequality n ≥ (4.8 + 1.4 * (o1 + o2 − (0.6 * u1) − (4.4 * u2)))/µ.390 The absolute minimum number of ballots sampled, for µ = 0.05 and zero misstatements, is ninety-six or higher.
Overstatements increase the required sample size and understatements decrease it, but not by equal amounts. If the number of overstatements is inordinately high, then the audit sample size approaches the size of the maximum number of ballots cast in the race, becoming a hand recount.
Ballot-level comparison audits are the most resource efficient of all three RLAs. However, due to the small sample size of this audit and its reliance on the voting system, it is possible for hackers to “misdirect” auditors implicitly relying on machine outputs in order to audit the voting system. If the supposed rig converts straight-ticket ballots for one party into straight-ticket ballots for the other, the optical scanner might doctor a serial number on the ballot image or CVR subject to audit, redirecting auditors to an arbitrary physical ballot with an array of selections identical to the voting system interpretation of the first ballot, possibly illegally submitted by the rigger and set aside for such diversionary purposes. However, this cheat becomes more onerous to deploy for larger vote shifts.
Nevertheless, to rule out such a possibility auditors would have to examine as many ballots as they would in less efficient batch-comparison auditing techniques.
The last form of risk-limiting audit, the ballot-polling audit, so named because it resembles a public opinion poll or an exit poll, which involves randomly sampling ballots until it can be forecasted with reasonable statistical certainty that the election outcome is correct, or that it is not, similar to how a poll gives reasonable certainty to commentators and political strategists that a candidate is leading over the other(s).
Define s as the reported vote share of the winner which is, for now, assumed to be correct, and t as an otherwise arbitrarily defined value that controls the chance of a full hand recount on the condition that the winner’s vote share is accurate within a certain specified tolerance, with the only requirement imposed being that t is small enough that, when subtracted from s, produces a value greater than 0.5.391392 t will be set to 0.01, alternatively 1%. Then, 1 - (s - t) is equal to the adjusted vote share of all other losing candidates combined.
Define α to be the risk-limit of the audit, which is set at 0.1, and the threshold value 1/α, which, under the preceding definition for α is ~9.9. Suppose, for instance, that s = 0.53. The Average Sample Number of ballots is defined to be (ln(1 / α) + (ln((s - 0.001) / 0.5)/2)) / ln((((s - 0.001) / 0.5)^s) * ((1 - (s - 0.001)) / 0.5))^(1 - s)393 which, for the specified parameters, produces an expected sample size of 1,296 ballots if the null hypothesis that the reported outcome is true is presupposed.
Define a test statistic T, which is initially set to a value of one. For each sampled ballot, multiply T by 2(s - t) if that ballot contains a vote for the reported winner and multiply T by 2(1 - (s - t)) if it contains a vote for anyone else. Thus, we can define T as the function 2^(n + m) * (s - t)^n * (1 - (s - t))^m, for n = # of sampled ballots with votes for the winner and m = # of sampled ballots with votes for other candidates. Assuming a risk-limit α of 0.1, if T is greater than the threshold value, 1/α, of ~9.9, then auditors have evidence that the reported outcome is correct. If it falls under 0.011 then there is a paucity of evidence supporting the null hypothesis of the correctness of the report outcome and the audit may be expanded into a full hand count.394
Ballot-polling audits have the perk of being highly efficient,395 and, unlike ballot-level comparison audits, they are entirely independent of voting system interpretation of scanned ballots, since not every jurisdiction opts to export digital ballot images, which can also be manipulated, as they only require access to the ballots, statistically-sound random sampling of those ballots, responsible organization of those ballots, and knowledge of the candidates reported to have won by that voting system as a comparative.
Unlike ballot-comparison audits, which can be gamed precisely because of their strict reliance on voting technology, ballot-polling audits are resistant to such manipulation unless ballot chain of custody is breached or sampling techniques are non-random — same as any other audit, although these audits are easily subverted if chain of custody is in any way breached. Ballot-polling audits, then, might provide a robust measure (if they’re conducted competently) to determine the chance the correctness of the reported results or, if they should have been defrauded, that the reported results are wrong, though they provide little to no information about mistabulation and error.
Of course, that is all assuming that election administrators actually choose to charitably interpret evidence that the election results are wrong as evidence that the election results are wrong. Provided the propensity for pundits and officials alike to reject and ignore evidence that contradicts their a priori assumption of a valid vote count, that might be a forlorn hope; in the world of the post-election audit, some jurisdictions even go so far as to eliminate vote-count errors detected by the audit entirely.396
Auditing statute will be assumed to allow public observation, inspect audit units or batches according to mathematically sound procedure that excludes the possibility of partisan interference by decision makers, count paper ballots marked by hand and enforce maintenance of ballot chain of custody, and include procedures for discerning voter intent unless otherwise noted.
5.1. Risk-limiting Audits by State
Georgia
O.C.G.A. § 21-2-498 outlines requirements for the execution of pre-certification, post-election, manual risk-limiting audits by county election superintendents, with a risk-limit of 8% for 2024, 6% in 2026, and 5% or less in 2028.397
Ga. Comp. R. & Regs. r. 183-1-15-.04(1)(3) charges the Secretary of State the authority to select one race to be audited after each biennial November general election, a decision that shall factor in the closeness of the margins of the reported outcome in a given contest, the jurisdictional breadth of the contest, the number of votes cast for the contest, the measure of suspicion in the contest's reported results, as well as administrative interests arising from the contests that are identified as potential recipients for audit and whether or not that could be finalized before certification.398399 Clauses second-through-fourth imply that statewide or federal races will almost certainly be selected as an ancillary by the SoS.
The audit shall be open to the view of the public and press, but no person except the person(s) designated by the election superintendent or the superintendent's authorized deputy shall touch any ballot or ballot container [Ga. Comp. R. & Regs. r. 183-1-15-.04(2)(1)]. Chain of custody for each ballot shall be maintained at all times during the audit, including but not limited to, a log of the seal numbers on the ballot containers before and after completing the manual audit [Ibid.(2)(3)]. The audit shall end once all selected ballots have been counted and the risk limit for the audit has been met [Ibid.(2)(5)].
100% of registered voters in Georgia live in jurisdictions that distribute unverifiable Dominion ImageCast X touchscreen ballot marking devices to all in-person voters.400
For the 2024 presidential election audit, 750,000 ballots, or roughly 14.2% of all cast votes for the presidential race, were subject to a manual audit. Despite statutory requirements, no other race appears to have been subject to the manual risk-limiting audit. RLA audit units included batches whose hand tallies were compared to the machine count of those batches, to which the SoS office, as always, sung unduly praise to:401
Georgia is recognized as a national leader in elections. It was the first state in the country to implement the trifecta of automatic voter registration, at least 17 days of early voting (which has been called the “gold standard”), and no-excuse absentee voting. Georgia continues to set records for voter turnout and election participation, seeing the largest increase in average turnout of any other state in the 2018 midterm election and record turnout in 2020, and 2022. 2022 achieved the largest single day of in-person early voting turnout in Georgia midterm history utilizing Georgia’s secure, paper ballot voting system. Most recently, Georgia ranked #2 for Election Integrity by the Heritage Foundation, a top ranking for Voter Accessibility by the Center for Election Innovation & Research and tied for number one in Election Administration by the Bipartisan Policy Center.
#1 state for election integrity indeed, Brad, #1 state for election integrity indeed…
There was the digital ballot image audit of computerized interpretations of scanned hand-marked provisional/absentee ballots and machine-marked printouts ran between November 8th and November 20th, 2024. Due to the complexity and logistical issues of manually tallying all races on the ballot, likely by a comparatively small audit team consisting of county staff, over millions of ballots and hundreds of ballot definitions, in time the certification of the general election, digital ballot images were examined by conducted using the Enhanced Voting optical character recognition-based automated audit software as opposed to a human-eye audit.402
Digital images were only inspected by an auditor in the event that image quality was degraded by the presence of scanner artifacts, dead pixels, faint machine-marked ballot text due to a printer toner or scanner cleanliness issue or, for voter-marked ballots, due to ambiguous voter intent, in a way that precluded the automated inspection of the ballot images. No comparisons to hand-marked ballots or even machine-marked ballot cards were conducted. No manual inspections of 99.741% of ballot images were conducted in order to rule out deliberate duplication of ballot images by software installed on optical scanner memory cards; the only safeguard is an automatic feature with the Enhanced Voting tool that allowed it to detect bitwise identical duplicates created by counties during the export process, not slightly transformed and altered duplicates.
Back in mid-November of last year an analyst looked the audit sample used to “determine” that Georgia’s elections were pristine and found that, while approximately ten percent of votes (no more than twelve) cast for Harris and two third party candidates were included in the statewide audit, seventeen percent of votes cast for Trump were included in the audit, a representation almost twice of what is expected, perhaps suggesting that they were oversampled egregiously. That observation partially forms the basis for this section. The purpose of a risk-limiting audit is to minimize the chance that the state will certify the incorrect outcome, irrespective of the correctness of the actual margins that decided the race. That being said, I believe it would be edifying to conduct a brief examination of the audit sampling itself as an addendum.
To quantify the rate of per-county irrepresentation in the audit sample, we define a % of reported statewide vote total per county parameter as being the ratio of the votes reportedly cast for president in that county and the total number of votes cast for president in the statewide aggregate, quantity multiplied by one hundred to create a percentage. We will also define a % of statewide audit sample per county parameter in much the same way, except with the reported votes for president in each county and the statewide aggregate being swapped out for the audited votes for president per each county and the statewide presidential audit aggregate, respectively. We will lastly define a parameter representing how the audit sample irrepresents the county based on the county’s share of the statewide reported vote, by simply taking the difference of the % of reported statewide vote total per county parameter and the % of statewide audit sample per county parameter. If this parameter is negative, then the county is presumed to be underrepresented in the audit compared to its proportion of the reported vote, and if this parameter is positive then it is likely being overrepresented.
In Figure 1, the irrepresentation % dependent variable is measured against Harris’s percent of the total votes reportedly cast for the presidency in each county, revealing an apparent sampling asymmetry with heavily Republican rural counties such as Cherokee, Pickens and Union being overrepresented in the audit sample by 1-2% and heavily Democratic urban/suburban counties either at best having a fair sample, with only Cobb County being oversampled by more than 0.5% (ironically having the most extreme oversample in the set) but, for most cases, such as Gwinett, DeKalb and Fulton counties, they depart from expected % audit sample share from about 1-2% to as much as 8% in the case of Fulton — extreme undersamples. We can also observe a different visualization in Figure 2, showing that the percentage of votes said to have been cast for president that were included in the audit sample versus the percentage of the vote Harris reportedly received hits a ‘wall’ at 45% Harris vote share, with only Terrell, Clay, Macon and Randolph Counties having more than 20% of their vote audited.
So whatever sampling method the auditors are using, it ain’t random.
Some investigation by plaintiffs for the then-ongoing Curling v. Raffensperger lawsuit was also done with respect to the statewide, post-election “audit” after the November 2020 presidential election, and the candidate-requested machine recount.403 Though the hand count audit involved the “recount” of all vote paper ballots and BMD printouts generated for the 2020 presidential general election, it was characterized, incorrectly, by Secretary of State Brad Raffensperger, as a “full count risk-limiting audit”,404 presumably to get around the fact that recounting ballots in Georgia without an evidenced allegation of outcome-changing election fraud (none had been supplied by either the Biden or the Trump campaigns) is expressedly prohibited by law.405
The red flags of a man so historically repulsed by election transparency and integrity suddenly pivoting to wanting to ensure the confidence of the voting constituency in their elections are flying high and are bright enough, even in the absence of the invocation of the fact that these activities are being conducted in a state where, as all in-person votes are cast unverifiably on touchscreen BMDs, a recount can safely be discarded as meaningless. Nonetheless, both the hand count, the Election Day machine count, and the subsequent candidate-impelled machine recount were, collectively, an administrative disaster, as documented by the plaintiffs of the suit for Fulton County, though it should be noted that there was no reason to believe these administrative irregularities did not persist in other counties, which I will largely transclude from for this subsection.406
The hand audit was conducted using “sort and stack”, where teams sort batches of ballots and BMD printouts by the presidential vote, then count the sorted stacks. These hand count batch tallies were printed manually onto paper “Audit Board Batch Sheets”, which were then transcribed into VotingWorks’s Arlo database generation software. Audit totals were calculated from that database, and a spreadsheet of results was produced from the program. Every ballot validly cast in the audited jurisdictions should be represented exactly once in one, and only one, ABBS, and every ABBS should only be entered once into the database from whence the audit spreadsheet was exported. While the process of transcription of ABBSs into the databases itself was done unobservably (and indeed unaccountably), images of the ABBS and the exported spreadsheets were available on the Internet and the public could theoretically compare the two.407
For Fulton County, many ABBSs were not completely filled in. The “Batch Type” field, signifying the mode of voting (absentee, election day, advance) was often blank. The four posted ABBS image files for Fulton County contain a total of 1,927 ABBSs, while the audit spreadsheet contains only 1,916 rows of data for Fulton County, meaning that at least eleven ABBSs are omitted from the spreadsheet, not counting possible duplicate entries in the sheet. On the assumption that the ABBSs, the original source of the manual tally data entered into the audit spreadsheet, are correct, the omission of that sample of 11 ABBSs deprived Trump of 1,582 votes, Biden of 2,288, and Jorgensen of 65, not to mention write-ins. This sample alone has a total of over 3,900 votes that the audit tabulated but were not included in Fulton County’s audit vote totals, compared with a statewide margin of 11,789 votes. The original tabulation in Fulton County showed 524,659 votes; the reported audit results showed 525,293, a difference of 634 votes, about 0.12 percent. Accounting for those 11 omitted ABBSs increases the apparent tabulation error from 634 votes to over 4,569 votes or 0.87 percent, far larger than the statewide margin of victory of 0.23 percent. It is also larger than 0.73 percent, which Raffensperger claimed was the maximum miscount in any Georgia county.
Indeed, there were plenty of similarly large errors between the machine counts and hand counts, but Brad Raffensperger, of course, attributed everything to “human error” since priority numero uno is maintaining the image of competent election administration, citing a 2012 study that found that hand count tabulation of ballots in a laboratory setting, using the very sort-and-stack counting method that was used in Georgia during its hand count audit, generated error rates running as high as two percent.408 It all makes sense, once you presuppose that the machine count is always correct and the corporations are right — and ignore the observed, empirical error rates of these vote tallies.
For the manual recount, the two-party Election Day vote totals for precinct RW01 (home of one of the plaintiffs) were reduced by 16.78%, with Trump’s vote tally falling by 16% and Biden’s vote totals falling by 17%. You might observe that the number ‘2’ is smaller than ‘17’, and if you do, congratulations, you’re Secretary of State material. By contrast, somehow the machine retabulation apparently found that 14.6% of Election Day votes for president were not included in the original count, in the very same precinct. Dozens of Trump votes that were not found in the hand count materialized in the second machine count, inflating his totals (and only his totals) by 20.5%.
These schizoid swings between counts illustrate the absence of proper ballot accounting and bookkeeping. Similar errors were observed in other vote types, and in other precincts, with error rates between the first and second machine counts running as seventy percent in some precincts, though hovering between ten-to-forty percent.
Fastidious and administratively sound hand recounts have the potential to be more “accurate” than automated tabulations for any number of reasons, including an obstruction or debris on the machine optical scanner lens, use of unreadable ink, memory card upload failures or other software irregularities that result in votes going unprocessed and unreported, and, most importantly, unclear voter intent or poorly filled-in ovals resulting in the machine rejecting the vote outright. The optical scanner might erroneously scan or record votes multiple times. Manual adjudication of voter intent can identify these lost, uncounted, spoiled and otherwise valid votes, and establish the non-existence of other votes, and include these votes into the final, amended count.409410
For instance, it was found that the Dominion ImageCast Central batch-fed, high speed optical scanner that is used to centrally tabulate absentee ballots across all counties in Georgia, and elsewhere, has an internal setting that can be fine-tuned by poll workers, election officials and hackers, that determines the scanner’s sensitivity to voter marks. During the June 2020 Georgia primary elections, the scanners were set to a sensitivity of 12%, meaning that if the ovals were filled in with a check mark or an ‘X’ mark, they wouldn’t be counted as votes. Indeed, it wouldn’t even flag it as an undervote at that sensitivity level and percentage fill, and these tabulation failures were only caught by manually (i.e., with all the potential for “human error” as a hand count) examining rejected ballot images for completely different reasons.411 The result was likely that hundreds or even thousands of absentee votes went uncounted during the primary season,412413 topping the June disaster heap that, not unlike Donald Trump, Raffensperger wholly forsook responsibility for; indeed, he barely acknowledged that it even existed.414
Fulton County did not produce an image file for every cast vote record. For the first machine count (the Election Day count), the procedure resulting the inclusion of digitized images of ballots or BMD printout cards for only 168,726 of the 528,776 cast vote records: 376,863 image files, or 71.2% of files for all cast ballots, were missing. For the second machine count (the electronic recount), Fulton County’s production included images of ballots or BMD printout cards for 510,073 of the 527,925 cast vote records: 17,852 image files were missing. Entire batches of digital ballot images were missing from the second machine count: for example, images from Scanner 801 batch 117 and Scanner 801 batch 118 are referred to in the cast vote records for the second machine count but the images were not among the electronic records. Without additional information it is impossible to determine whether the missing images have because of human error or malfeasance, programming errors (bugs), and/or malware in Fulton County’s election management system.
What ballot images remained extant demonstrate repeated instances of the same ballot being scanned multiple times, or the corresponding electronic record being duplicated repeatedly, in Fulton County’s database. These duplicate images possibly implicate tens of thousands of votes scanned over the course of the Election Day machine count and the machine recount.415
It is generally not necessarily possible to determine if any pair of two-hundred dots-per-inch resolution computer scans of ballots that include very common lists of voter selections (particularly flush straight-tickets) are the same ballot, unless if each ballot image has a identifying, randomized serial number, which Georgia paper ballots do not have (though, at higher resolutions, otherwise identical pieces of paper can be “fingerprinted” based on paper fiber patterns416). Even ballots that are scanned repeatedly by the same scanner are not guaranteed to be bit-wise identical and automatically detectable by a simple automated duplicate file detector, and ballot images that are duplicated electronically can be doctored to be as distinct from the base image as an authentically different image.
Nevertheless, some ballots have certain identifying peculiarities that allow them to be distinguished from other ballots with similar voter selections, such as stray marks or poorly filled ovals characteristic to a specific family of ballots that are unlikely to be spontaneously recreated by multiple voters, especially living far apart from one another and unlikely to influence each other. Likewise, a rare array of voter selections, like a specific split-ticket pattern unlikely to be replicated repeatedly, or the presence of a vote for an obscure, specific write-in or third-party candidate, helps distinguish a ballot and identify modified duplicates. Similar restrictions are applied to divining duplicates from cast vote records.
There are at least 12 hand-marked absentee ballots from Fulton County precinct RW01 that were scanned twice in the first machine count. At least three BMD cards from precinct RW01 appear to have been scanned twice in the machine recount in RW01, based on the votes and the order in which they were scanned in two batches. In particular, Scanner 801, batches 43 and 44 — both comprising scans of advance in-person BMD printout cards — start with images of 214 BMD cards that have the same sets of votes in the same order in both batches. The two batches were scanned within about five minutes of each other, according to the timestamps in the images. Many of the images show write-in votes or votes for third-party candidates, further evidence that the match was not coincidence. Visual inspection of all 214 pairs and confirmed that they match: those BMD cards were scanned twice in the machine recount. The other 211 duplicated scans are of BMD cards from other precincts in Fulton County.
There is also one hand-marked paper ballot that was scanned twice in RW01 in the machine recount, and at least seven hand-marked paper ballots that were scanned thrice in RW01 in the machine recount. Twenty-nine images seem to represent only 11 distinct pieces of paper, even though they contributed 29 votes to some contests, including the presidential contest.
For Fulton County as a whole, plaintiffs in Curling v. Raffensperger identified images of at least 2,871 ballots and BMD printout cards, of a sample of 6,118, that they claimed were counted two or three times in the machine recount. Some were identified by visual inspection of the images; others were inferred to be duplicates because a sequence of cast vote records was identical (or reversed) for long portions of two scan batches. 916 of the 2,871 sets of images were images of hand-marked paper ballots. It could be determined that at least 891 of the claimed 916 multiples were genuine duplicates, with a lower confidence bound of 95%.
These observations of ineffectual protocol is evidence of Fulton County’s inability or lack of care in keeping track of which ballots had been scanned and those that had not. It is impossible, without a properly conducted audit that the Georgia “statewide hand/machine count audit” was decisively determined not to be, to know with certainty which cast vote records and digital ballot images were altered or manipulated accidentally or deliberately.
It is not possible to determine whether some ballots were not scanned by county optical scanners from the database of ballot images, and the “audits”/“recounts” were not likely to pick up these potentially lost ballots. Ballot accounting and chain of custody maintenance procedures were lax and poorly administered in many Georgian counties, as evidenced by thousands of votes being lost on Election Day and only being found during the audit,417418419 and the saga of mysteriously vanishing (other times appearing) votes between machine tabulations, retabulations and hand counts.
It is possible that memory cards were never uploaded to election management systems after the election, or were uploaded twice, or that the EMS lost votes during an upload failure whilst falsely reporting that all votes have been received, as EMSs have been known to do. The most fundamental safeguard against election manipulation is to determine whether or not the number of voters and the number of votes matches, to defend against ballot stuffing or loss of votes. While e-poll books can be hacked to fix the two values to match each other regardless of what transpires on Election Day (as we will observe momentarily), assuming the alleged absence of criminal activity it appears that Georgia jurisdictions did not engage in this basic duty. How, without exaggeration, hundreds of thousands of ballot images could be lost in Fulton County alone, or even never exported after an election, despite the twenty-two month federally-mandated retention period of election materials, is confounding.
Note that the plaintiffs only analyzed Fulton County, which means that it’s still likely that both recounts were run just as poorly. It has been charged that, while the process of counting the ballots by hand was open to public observation, witnessing the markings on the ballots themselves, the transcription of the results, and the generation of audit reports were entirely conducted in secret and subject to the private, ethically-challenged discretion of the Secretary of State. If he so chose to ‘fudge’ the hand count numbers to match the election results then, provided the lackluster ballot reconciliation and accounting procedures of at least Fulton County, I do not think anyone would be in the position to challenge him.420
Recounts and audits mean very little without a trustworthy record of vote, and mean nothing without proper administration. Nevertheless, any such protests apparently fell on deaf ears as Brad Raffensperger wasted no time characterizing the many expert witnesses in the Curling v. Raffensperger court case as conspiratorial loons, and used (and abused) the various polemic prerogatives conferred by a “flawless” post-election auditing campaign to assert that Georgia’s easily hacked and unverifiable voting systems are actually, in complete contravention of the general wisdom in the field of election integrity, replete with the backing of countless cybersecurity experts, completely secure and unneeding of such checks as ‘verifiability’ and ‘susceptibility to reasonable spot-checks and recounts’ (school children are expected to do-over their homework before turning it in).
The consequences of this particular pathology, widespread as it is, was, and continues to be, spilled into the years hence. Thus we observe the administration’s pathetic response to the Coffee County debacle of 2022, wherein Sidney Powell’s troopers421 were ushered into the county central office’s tabulation room by local election commissioners and, with negative resistance from those officials, illegally exported copies of the hard drive contents of Dominion voting and tabulation systems.422423424 Raffensperger, having put the lessons of Trump’s erstwhile petitioning, on no uncertain terms, for him to overturn the results of Georgia’s presidential election on the backburner, did his best to stall, obstruct, and do absolutely nothing to help425 — amazingly and audaciously, whilst crowing, alongside his right-hand attack dog Gabriel Sterling, about how they had been presented with no evidence of a breach and that it all didn’t happen. “No evidence”, despite the Curling v. Raffensperger plaintiffs having provided them video evidence of a breach nine weeks earlier.426
Eventually, U.S District Judge Amy Totenberg unsealed a report427 describing the long list of horrific, and entirely predictable, vulnerabilities that was compiled by the plaintiffs’ expert witness, J. Alex Halderman of the University of Michigan, who was allowed to independently examine the firmware of the Dominion ImageCast X ballot marking device and Dominion ICP optical scanner in 2021.428 The report, which was reviewed by CISA in 2022, compelled them to post an advisory citing “vulnerabilities...that should be mitigated as soon as possible”, and instructed Dominion on the system upgrades required to ameliorate these risks429 — upgrades that, all told, most likely wouldn’t fix a thing.
Systemic issues and modifications that require system or component redesign can not be addressed by simple software upgrades. These issues reflect the most grave concerns about the security and robustness of these systems, and any claims for issues fixed in software upgrades should be viewed with deep skepticism; all such claims must be demonstrated authoritatively.430
Many of the issues highlighted in the report are not unique to the ImageCast X BMD and, if they could be fixed so easily, would have already been fixed. Provided the election industry’s (including Dominion’s431) historical resistance and inability to secure their own systems, the weight of this lesson only redoubles.
Of course, since no-one in Raffensperger’s administration actually cares about election integrity, they predictably wasted no time smearing these expert witnesses, again, as “paranoiacs and conspiracists” and making vague, arrogant432 allusions, as officials usually do, to non-existent “security measures” supposedly preventing attackers, both within and without, from undermining the state’s fragile electoral foundations,433 citing such as the rationale behind the cultish mendacity that, because such undemocratic happenings simply Can’t Happen Here, any security upgrades could be safely stonewalled for eighteen months until the aftermath of the 2024 presidential general election.434
Pennsylvania
25 Pa. Stat. § 3031.17 directs county boards of elections to audit 2%, or 2,000, ballots, whichever quantity is lesser, cast by voters during the preceding general, special or primary election during the course of the routine post-election canvassing protocol. This may be done manually, or by machine retabulation,435 though every county that uses optical scanners are directed to recount by hand, per a 2011 directive issued by the Secretary of the Commonwealth,436 and since every county in the state utilizes optical scanners in some form to tabulate hand- or machine-marked ballots, all counties are hereinafter assumed to audit ballots by hand. Counties are also directed to conduct risk-limiting batch-comparison audits after each general and primary election. Guidance for this procedure is supplied by the state’s Risk-Limiting Audit Directive.437
The practical purpose of the 2% audit is negligible so for didactical purposes I will disregard it and review the RLA for 2024, which is a batch-comparison audit of 38,920 votes for the State Treasurer election. Others have, of course, already looked at the audit sample in the past, and the dataset is available for download.438 Only thirty-one counties were audited — auditors somehow managed to let thirty-five other counties escape the audit wholesale.
The same trend of oversampling smaller, and more Republican counties continues with the Pennsylvania risk-limiting audit. The effect is such that Allegheny County, the second largest county in the state and one that has the highest absolute turnout overall, is encapsulated by 1,778 ballot sample that’s smaller than the 2,362 ballot batches from Adams County, with less than one-twelfth the population and the total votes.
Nearly 700,000 ballots cast out of Philadelphia County are represented by a single, discrete audit batch of 183 ballots that’s skewed to boot — knowing that all votes in Philadelphia County are cast by completely unverifiable hybrid BMDs, such that the strategic impetus to avoid overusing that recount-dodging privilege is completely discountable (unlike in Georgia, where the chance of detection of BMD misprinting of voter selections is still above zero), then there is no reason to believe that an attacker would steal votes in a recoverable fashion and all divergences from the reported results are attributable to poor sampling. So how they managed to sample an audit batch, subject to the presupposition that the election results are unchallengeable, so egregiously irrepresentative of the >80% Democratic county, is a debate for the ages.
In any case the audit samples no more than ten percent of cast votes per county, peaking with Montour County, and its 9,424 votes cast for the State Treasurer race. It only accounts for 0.179% of all votes cast across the thirty-one county slate, but in the audit accounts for 2.03%. Philadelphia County accounts for 12.536% of the audited county slate in the reported results, which shrinks to 0.4702% in the audit, a twelve-point undersample. The numbers in Allegheny County are similarly extreme. This gives way to a chain of counties of ever-increasing size that, in the series, diverge further and further away from expected audit sample representation in a correlation linear to their reported size, as shown in Figure 3.
Seven counties deploy 100% unverifiable ES&S ExpressVote and ExpressVote XL hybrid BMD/tabulator devices exclusively for all in-person voters. These counties are Cameron County, Cumberland County, Elk County, McKean County, Northampton County, Northumberland County, and Philadelphia County, accounting for 17.4% of voters in the state. Thirteen other counties exclusively deploy unverifiable ballot marking devices alternately manufactured by ES&S, Dominion and Unisyn439 for all in-person voters. These counties are Berks County, Bradford County, Columbia County, Crawford County, Forest County, Greene County, Luzerne County, Potter County, Susquehanna County, Union County, Warren County, Washington County, and Westmoreland County, accounting for another 12.6% of registered voters.440 Audits and recounts are of questionable or negative utility in these counties.
Hand-marked paper ballots in the remaining majority of counties are theoretically liable to be subject to verification though we will explore two sections afield how Pennsylvania law is (almost) uniquely hostile to hand recounts of any kind.
Nevada
The state of Nevada has a hybrid arsenal of two different auditing procedures used after voting ends and prior to certification after the results of the election.
The first one is an audit, discretionarily manual or by electronic retabulation, where county clerks are charged with auditing voting machines to diagnose their error rate. The clerk of a county with less than 100,000 votes will select three percent of voting machines with VVPAT capability, or a minimum of four terminals, and compare the tally of each vote for each candidate or voted measure on the audit trails to the tally records in the voting machine’s memory. If a discrepancy of four or more votes is found, then the county clerk must audit an extra 3% of voting machines in the county and repeat the above stated procedure if the discrepancy cannot be resolved. An explanation of any discrepancies found and their root cause must be reported to the Secretary of State as part of the county’s audit results. If the county has more than 100,000 votes then the clerk will select 2% of voting machines, or a minimum of twenty machines, whichever is greater, and commence the same process [Nev. Admin. Code § 293.255].441
The second is a risk-limiting audit of one statewide race, randomly selected by the Secretary of State, which the Secretary must make known to the county clerks at least fifteen days in advance of the election, and likewise, one countywide election, selected piecewise by the county clerks, is selected 15 days before the election [Nev. Admin. Code § 293.480(3)]. The risk-limiting audit will consist of either a ballot polling or ballot comparison audit, or a combination thereof, with the risk-limit set at five percent.442 Nev. Admin. Code § 293.480 is referred to as the primary source for this procedure, and established the procedure for the 2022 RLA pilot program, though Nev. Admin. Code § 293.485,443 which went into effect on January 1st, 2024, did not deprecate or otherwise modify those provisions.
95.9% of Nevada voters live in counties deploying unverifiable direct recording electronic voting devices with voter-verifiable paper audit trails for all in-person voters. Another 2.4% live in jurisdictions that similarly use unverifiable ballot marking devices for all in-person voters. Only one county, Nye County, home to 1.6% of registered voters statewide, employs theoretically verifiable optical scanners with hand marked paper ballots, and DREs for accessibility purposes. Mail-in ballots are paper ballots that are theoretically verifiable.444
Virginia
Va. Code § 24.2-671.2. specifies that at least one randomly House District race must be audited in years of a general election where any of Virginia’s U.S. House of Representatives seats are contested, and at least one randomly drawn General Assembly district race during a general election where any such seats are contested, must be subject to a risk-limiting audits performed by local electoral boards and general registrars under the supervision of the Virginia Department of Elections and in accordance to procedures prescribed by the State Board of Elections, including procedures for randomly selecting races to audit, pre-audit organization, maintaining ballot chain of custody, counting ballots by hand, and execution of the audits themselves.445
In any odd-numbered year where elections are held, at least one must be subject to the risk-limiting audit, including “constitutional offices”, for which Board of Elections certification is required [Va. Code § 24.2-671.2.C.3]. In any case, each locality (county or independent city) must participate in a risk-limiting audit at least once every five years, and may impart auditing local offices too. Such audits of local elections must be approved, through a vote, by a two-thirds majority of State Board members.[Ibid.C.4]
No contested race wherefor the margin between the leading candidates in the unofficial results and official results generated during the canvass, where absentee ballots and provisional ballots have been tabulated after Election Day, changes by less than 1% [Ibid.E.].446
Only two elections (Senate and House District 1) were subject to auditing in 2024. The presidential race is not eligible for audit under House Bill 6001 (2024).447
Rhode Island
Commencing in 2018, the Rhode Island Board of Elections, in conjunction with county boards, is authorized to conduct risk-limiting audits after all primary, general, and special elections for local, statewide or federal office in accordance with the requirements of R.I. Gen. Laws § 17-19-37.4. If a risk-limiting audit of a contest leads to a full manual tally of the ballots cast using the voting system, the vote counts according to that manual tally shall replace the vote counts reported.
Colorado
Under Colo. Rev. Stat. §1-7-515, the state of Colorado permits the use of risk-limiting audits in every county in the state after each primary, general, coordinated, or congressional vacancy election, with the exception of San Juan County, which hand counts its ballots.448 The state legislature clarified in 2024 that counties are also allowed to run regular manual audits of no less than 5% of voting devices used in their jurisdiction, or 5% of ballots in the case of central-count counties, in the event that the standard RLA is not feasible to conduct, per Colo. Rev. Stat. §1-7-514.449 Counties can also develop their own audit in the case of an instant-runoff election, so long as it does not interfere with Colo. Rev. Stat. §1-7-515.450
No later than the Friday following Election Day the Secretary of State should have already selected at least one statewide contest (if there is none then they will select other ballot items), and for each county one local contest, which will be subject to the risk-limiting audit, per 8 Colo. Code Regs. § 1505-1:25.2.2(j). These ancillary contests are selected according to the following criteria: the closeness of the reported tabulation outcome of the contests; the geographical scope of the contests; the number of ballots counted in the contests; any cause for concern regarding the accuracy of the reported tabulation outcome of the contests; any benefits that may result from auditing certain contests; the ability of the county clerks to complete the audit before the canvass deadline; and any recommendations provided by county clerks or the public regarding which contest should be targeted. 451
Maine
Going into effect on January 1st, 2025, Me. Stat. tit. 21-A, § 726.3 specifies the procedures by which post-election audits of elections to federal and state offices, alongside state referenda, should be conducted, utilizing statistical principles designed to limit the risk that the incorrect outcome is certified. This risk-limiting audit procedure is currently in a pilot stage and not mandatory, and the Secretary of State, though charged with the administration of post-election audits, is not yet statutorily required to carry out such tasks.452 Nevertheless, what the pilot determined is that ballot-polling and batch-comparison audits are insufficient for auditing state legislative races due their small scope and the lack of votes cast therein, and that ballot-level comparison audits are the most airtight method to spot-check these races; however,453 ES&S DS200 polling place optical scanners do not facilitate the exporting of CVRs. DS850 batch-fed optical scanners can be configured to export CVRs, and thus allow ballot-comparison auditing of smaller races.
The risk-limiting audit is open to the public and to media representatives, though the Secretary of State may limit the number of observers if there is insufficient space and the presence of additional individuals would interfere with the conduct of the post-election audit.
As stated earlier, ballot-level comparison audits are the easiest of the risk-limiting audits to game, meaning that local elections would be the easiest to fix undetected going forward.
Indiana
Elections in Indiana may be subject to a non-mandatory post-election audit of votable ballot lines “by means of tests and procedures that are approved by the commission and independent of the provider of the paper ballot or DRE voting system being audited”, suggesting a hand count audit or automated audit using a tabulation system other than that certified for use during elections. [Ind. Code § 3-11-13-38].454
The Secretary of State of Indiana has the authority to designate counties as post-election audit counties. For this to occur the county election board must adopt a resolution to petition the Secretary of State, per Ind. Code § 3-12-13-4. They also have the authority to identify the elections that are ideal to subject to auditing — all contests on the ballot are eligible to be audited, if the Secretary of State determines it necessary.455 County election boards, then, will execute the audit according to procedure prescribed by statute, and they may use risk-limiting techniques such as ballot-polling or ballot comparison auditing if the voting devices have the capacity to export cast vote records.456 The Secretary of State may also waive the requirement for a post-election audit should the county election board issue a written statement affirming that the technology in use cannot satisfy the audit requirements. 457
In 2024, seven counties were audited. Of these, Delaware, Hendricks, and DeKalb counties utilized a ballot-comparison audit, comparison VVPATs to corresponding CVRs exported by the voting system, while Switzerland, Dearborn, St. Joseph, and Fountain counties used a ballot-polling audit.458
In counties that utilize optical scan voting systems, referred to as a ballot card voting system by statute, the county chair for either major political party may petition of county election board to validate the reported vote totals from the optical scan devices in no more than 5% of precincts in the county, for a minimum of five precincts, no earlier than the Saturday preceding the election and no later than the Thursday after the election [Ind. Code § 3-11-13-38]. Direct recording electronic returns may also be audited only if a discrepancy in voter reconciliation between the number of votes cast on the DREs and the number of voters who checked in on the county pollbooks exceeds a pre-defined “audit threshold”. In this event, the county election board or the Secretary of State may order an audit of the voter-verifiable paper audit trails, as described under section Ind. Code § 3-12-3.5-8.459
54.3% of Indiana voters live in jurisdictions that deploy unverifiable direct recording electronic devices with VVPAT for all in-person voters. Another 34.5% live in jurisdictions that use unverifiable ballot marking devices for all in-person voters. Only 11.2% use optical scanners with hand-marked paper ballots. However, unlike most other states the majority of Indianans are served by the smaller company MicroVote. The remainder is are mostly serviced by ES&S and Hart InterCivic, and the similarly obscure Unisyn Voting Systems.460
Audits cannot escalate into a recount.
5.2. All the Other Audits
Alaska
Manual audits of all contested races and, if applicable, one ballot measure and judicial retention measure, after general, special and primary elections in Alaska [Alaska Admin. Code tit. 6 § 25.068461 & 25.203462] are administered and regulated by the Director of Elections, who is appointed by the Lieutenant Governor, and conducted by the State Review Board which is composed on four qualified voters selected by the director [Alaska Admin. Code tit. 6, § 27.070].463 Within 16 days of Election Day, voter selections from each race on in-person and absentee ballots from one randomly-selected optically-scanned precinct in each of the state's forty State House districts, such that the precinct comprises at least 5% of all votes cast in that district, are audited and compared to the machine count in those precincts.464 If there is a discrepancy of over 1% from the machine count in a given precinct, the State Review Board will hand count every ballot in the associated district.
It has the notable problem that attackers could easily avoid stealing votes in large precincts and only target smaller precincts instead. Also, the statute is unclear on which body or individual randomly selects precincts. The Division of Elections, which the director heads, is nominally nonpartisan and employees therein are required to stay their potentially harmful political affinities. But the division remains under the supervision of the Lieutenant Governor, a strictly partisan, elected office, and the Director of Elections is their appointee,465 so they may be handpicked to conform to a certain set of characteristics and partisan proclivities useful to the Lieutenant Governor.466 If the Division of Elections or its employees, or even the director, determines which precincts are audited, and they are not nonpartisan while being privy to which precincts should not be audited, then the value of the audit becomes zero.
Arkansas
Pursuant to Arkansas Code § 7-4-121 the State Board of Election Commissioners shall select by lot a representative sample of counties, polling sites, early voting locations and voting centers within sixty days following the date of the most recent, pertinent general or primary election to be audited by manual count.467 The audit is not binding, and imparts no legal effect on the results of the election.
The jurisdictions of Conway, Drew, Fulton, Garland, Lee, Madison, Mississippi, Montgomery, Ouachita, Saline, Scott, Searcy, Sharp, Van Buren and Yell counties were subject to an audit conducted after the 2024 preference primaries, leading to the lofty claim of exactly zero discrepancies between the hand count and certified machine count, with but one exception in Searcy County, which hand-counted its ballots — matching, of course, the standard corporate prayer that the optical scanners are always accurate, and hand counts are not.468
84.5% of registered voters live in jurisdictions that deploy unverifiable ballot marking devices for all in-person voters. The remaining 15.5% of registered voters across eight counties vote using hand-marked paper ballots and optical scanners, with optional use of BMDs for accessibility purposes. All voting systems in the state are manufactured by ES&S.469
Arizona
Under Arizona Rev. Stat. § 16-602, after each primary, special, general and presidential election, the county officer in charge of the election must conduct an audit of ballots, at one or more secured facilities, at least two percent of the precincts in that county, or two precincts, whichever is greater; plus one percent of early votes or five thousand ballots, whichever is less, per Arizona Rev. Stat. § 16-602(B)(1) & (F), respectively. Precincts are randomly selected, without the aid of a computer program, by the representatives of each qualified state party, in public, after all ballots cast in the state have been returned to the central counting center [Arizona Rev. Stat. § 16-602(B)(1)]. Up to five contested races may be audited, and are selected by lot. 470
The eligible races include one statewide ballot measure, unless there are no measures on the ballot, one contested statewide race for statewide office, one contested race for federal office, either United States Senate or United States House of Representatives, and one contested race for state legislative office, either State House of Representatives or State Senate, in the context of a general election. Two percent of polling places may be audited by county administrators after presidential preference primary elections [Arizona Rev. Stat. § 16-602(B)(2)].
If there are fewer than four contested races picked during the selections and if there are additional contested federal, statewide or legislative races or ballot measures, additional contested races shall be selected by lot not using a computer until four races have been selected or until no additional contested federal, statewide or legislative races or ballot measures are available for selection. If there are no contested races, a hand count shall not be conducted for that precinct for that election [Arizona Rev. Stat. § 16-602(B)(2)(e) & (f)]. Write-in candidacies cannot be audited [Arizona Rev. Stat. § 16-602(B)(4)]. Provisional ballots and “conditional provisional” ballots cannot be included in the count, per Arizona Rev. Stat. § 16-602(B)(1).
For the post-election audit of the 2024 presidential election as it was administered in Arizona, a dataset is available to precipitate the independent analysis of the audit samples used in each county.471 In November of last year, an analyst did one such inspection, which forms the basis of the following section.
Table 1 displays the Early Vote Batch number on the first column and the corresponding Harris and Trump ballots in columns two and three, and the total number of ballots in column four. The disparity between the sum of Harris’s votes and Trump’s votes is attributable to third-party votes which I have omitted from the sample.
We then can calculate the percent candidate shares of the sample audited early vote to find that Harris wins 53.11% percent of the early vote, Trump wins 46.34% and third party or independent candidates win a little under one percent of the vote with a candidate margin of error of 1.3%, and a standard error of 0.006967. As Harris only won 48.34% of the reported early vote in Maricopa County and to Trump 49.73%, we calculate a z-score of 7.98859 and -4.85618 for the respective differences suggesting that the error is unlikely to be a product of statistical noise (α = 0.95). Likewise, the p-values are very close to zero.
Early voted ballots are randomly selected from the population of Maricopa County voters, unlike Election Day ballots which are traceable back to physical polling centers and are not necessarily representative of the county’s voters, only its election districts. Because of this the audit candidate vote shares for Election Day ballots are not as useful, and it appears that the selected polling places are strongly skewed in favor of Trump. Nevertheless, we will assume separately that both the reported results and the audit results are representative of the population of Election Day voters. There are 251,150 votes cast on Election Day and 1,810,424 votes for president cast during the early voting period. We will calculate the expected vote totals using the early voting audit percentages an reported Election Day partisanship, and the early voting and Election Day audit percentages as such:
1,060,429 votes expected for Harris and 988,752 votes expected for Trump, equating to vote shares of 51.44% and 47.8% respectively. Notably, the reported results are almost the exact inverse of these audit totals, at 1,051,531 for Trump and 980,016 for Harris.
1,033,717 votes expected for Harris and 1,014,735 votes expected for Trump, equating to vote shares of 50.14% and 49.22% respectively.
In the first scenario, since Trump’s reported statewide margin of victory is 187,382 votes, the resulting margin shift in favor of Harris, 143,192 votes, accounts for 76.4% of the difference. In the second scenario, the shift only accounts for 48.29% of the difference. Whether or not the audit means that this is the actual early vote support Harris received in the court of public opinion, or if the audit possesses the faculties (or stewardship) to even detect such fraud, is up in the air for debate. The early voting batches might be irrepresentative of the entire county, similarly to Pennsylvania and Georgia — though in both cases the “bias” skewed towards Republicans which, even assuming honest error, suggests that ballot sampling methods are more likely to choose Republican batches versus Democratic batches. In Arizona, there are no all BMD or DRE jurisdictions, unlike the other two states, so the objective determination of oversampling is not possible. Perhaps the Democratic representative purposely picked batches that they knew would be skewed towards Harris. Hell, perhaps the Republican representative chose batches that favored Trump, or more closely matched the reported results rather than the ‘actual’ results, and perhaps the audit batches themselves are modifiable and not reliable. Who knows, though some of the analysis from on high inferred such rather gnarly conclusions from the data.
California
California Election Code § 336.5 and § 15360 requires county elections officials to conduct a manual tally of at least one percent of precincts in the county during the canvassing process to measure a hand count against the accuracy or inaccuracy of the initial Election Day electronic count.472473 If the county should deem it necessary, they may tally more than one percent at their discretion. If one percent of precincts is less than one whole precinct then the county will audit one precinct. Precincts are chosen at random by “the elections official”, though which specific office this corresponds to is never specified by statute. Nevertheless, in ceding unsupervised sovereignty over auditing to possibly partisan officials who may potentially be unscrupulous and/or even criminal is not desirable, and may entail the official choosing precincts that are known not to contain any evidence of vote tampering to audit. The county must also audit a random sample of one percent of absentee ballots, plus additional mail-in vote batches containing votes for races not included in the initial audit batch, per Cal. Elec. Code § 15360(2)(B)(iii)(I).
2017 AB 840 amends the audit law, exempting from the audit ballots not included in the semifinal official canvass that is required to be completed by counties before the Thursday following Election Day,474 which may exclude the auditing of large numbers of remaining absentee and provisional ballots that are typically counted after Election Day and, specific to California, into December.
Auditing and recounting procedures are likely to be ineffective in Los Angeles, San Diego and Riverside Counties (the 1st, 2nd and 4th largest counties in the state) in South California, which supply ballot marking devices to all in-person voters; namely, the Smartmatic/Los Angeles County in-house “Voting Systems for All People” voting system BMD, and the Dominion ImageCast X in Riverside and San Diego Counties, both of which print (allegedly) human-readable text and voter-unverifiable QR codes onto machine-marked ballots. These counties alone account for 40.1% of all voters in the state.475
Connecticut
Section 9-320f(a) of the Connecticut General Statute provides for the post-election, pre-canvass audit of paper ballots in not less then 5% of “voting districts” — that is, central places were votes are cast absentee or in-person and tabulated, as well as Election Day votes cast at precincts — in the state, district or municipality applicable to the context of the audited races by registrars of voters or town clerk. As prescribed in Conn. Gen. Stat. § 9-320f(b), for general elections where the offices of the presidency and the governors are subject to contest, at least three races shall be subject to audit, where one should be drawn by the Secretary of the State, and 20% of races on the ballot should be audited after primary election cycles, plus one additional selected by county clerks. 20% of races, for a minimum of three, are audited after municipal elections.476 When a discrepancy of over half of a percent is discovered during the auditing process, cannot be resolved through other means (for instance, an accounting of improperly marked ballots), and would exceed the margin of victory if extrapolated to the entire contest, the audit may be expanded into a mixed hand/machine count “discrepancy recanvass”, conducted according to procedures prescribed in Conn. Gen. Stat. § 9-311.477
The audit traditionally involves a manual hand count, however, an amendment was made to the auditing process that, according to Conn. Gen. Stat. § 9-320g, for general or primary elections held after January 1st, 2016, the manual audit can be replaced by an audit conducted using electronic equipment, as in, a machine retabulation, at the authorization of the Secretary of the State in consultation with the University of Connecticut.478
Audit results are not binding upon election results unless if a sufficiently large discrepancy is found that merits launching a recanvass.
Delaware
Delaware Code Title 15 § 5012A provides that, within 48 hours of the certification of a general election, primary election or school board election, the Department of Elections must audit one randomly selected voting machine in each county and in one randomly selected election district in the city of Wilmington to audit publicly. Within 60 days of certification, the Department shall conduct a second audit of election results for all races in a randomly selected election district in each county and the city of Wilmington, and audit the results of one randomly selected race in a randomly selected election district in each county and the city of Wilmington. The election districts critically must be unique to each auditing round. Absentee ballots and early voted ballots are not required to be included in the audit batches.479
If a discrepancy from certified results is found to be in excess of 0.5% then the audit will be retrialled by a second auditing team distinct from the original team [25 DE Reg. 101(5.1)] and, if the discrepancy cannot be reconciled, the second team will consolidate all documentation relating to the troubled voting system, the voting system will undergo further Logic & Accuracy testing, and another voting system for the same election will be audited [25 DE Reg. 101(5.2)]. The Department will then enlist the vendor and federal certification authorities to identify possible corrective action and the voting system shall be verified to no longer produce these errors [25 DE Reg. 101(6)].480
The function of the audit appears to impound the detection of routine error. All counties in the state utilize 100% unverifiable ES&S ExpressVote XL hybird BMD/tabulators for all in-person voters, so no recount or audit will have any possibility of detecting malicious mistabulation of those votes.481
District of Columbia
Under D.C. Code § 1–1001.09a, the District of Columbia Board of Elections must manually audit no less than 5% of precincts and no less than 5% of centrally tabulated mail-in ballots and special ballots as a statutory prerequisite for the Board to carry out certification. Of these audited records, the Board must tally votes for no less than three races, where at least one must be District-wide and the other two must be held across the full breadth of at least one ward. At the discretion of the Board, whether at the request of a candidate or else, it may expand the scope of the audit.482
If the discovered discrepancy from the unofficial results exceeds 20% of the reported margin of victory for that race, or exceeds an error rate of 0.25%, whichever is less, then a second audit of the same precincts will be launched to verify the discrepancy, alongside an additional audit of 5% of centrally-tabulated ballots, and if it does the audit will escalate into a manual recount. D.C. Code § 1–1001.09a(h).
Florida
Fla. Stat. § 101.591(2)(a) of Florida’s statutes stipulates that at least 1% of precincts inside a county, floored at a minimum of one precinct, and no more than 2% of precincts in the jurisdiction, may be subject to a hand-count audit. Only one contest on the ballot in those jurisdictions, “randomly” chosen at the sole discretion of the county canvassing board, can be manually audited. The 1-2% of precincts are also chosen by the county canvassing board.483
A 2013 amendment introduced Fla. Stat. § 101.591(2)(b) which authorizes jurisdictions to audit 20% of precincts using an “automated independent audit system”, which appears to be another type of ballot scanner, perhaps a central county, high-speed optical scanning tabulation system, approved by the state Board of Elections that differs from those already certified for use during voting. In such an audit, counties must retabulate every single race on the ballot(s) within their jurisdiction.484 As stated above, machine retabulation audits, with few exceptions, are unlikely to detect any discrepancies relating to fraud.
Audits in Florida are not binding upon the results and cannot be expanded into a recount.
Hawaii
Haw. Rev. Stat. § 16-42 requires the execution of a statewide pre-certification manual audit of in-person and absentee ballots in 10% of precincts where electronic voting systems are in use to verify the fidelity of electronic tallies to voter intent. If discrepancies are found, the chief election officer may expand the audit in order to determine the extent of misreporting within the system. A 2024 revision to the statute allows the chief election officer to rely on “electronic tallies” created by the electronic voting system to audit results so long as the baseline 10% manual audit verifies the correspondence of “electronic tallies” and hand counts: in other terms, a retabulation audit.485
Except for designated election officials, counting center officials, or official observers, no person shall be permitted to witness the audit without the authorization of the chief election officer, clerk, or designated representative, though “observers may request to conduct a manual audit” [Haw. Code R. § 3-177-762(a)(2) and (3)]. This is not defined further though the Verified Voting audit law database interprets it as allowing public observation in some form.486
Idaho
Idaho Code § 34-1203A(1)(a) and (b) requires that counties conduct manual pre-certification audits after voting for any of the following: any or all federal elections held in Idaho; the election for governor; the statewide office election having the narrowest percentage margin of votes; the statewide ballot question election having the narrowest percentage margin of votes; and one legislative office election within the county.487 Eight counties (Idaho has forty-four) of varying population are selected by the Secretary of State of Idaho, and then at least one precinct from these counties, at most 5% of precincts are drawn by the State Treasurer, to be selected for the audit. If fewer than 2,100 ballots are selected for audit in a county, additional precincts may be drawn, up to the full county.488 The Secretary will, at their discretion, choose at least one candidate or ballot question election for audit for each precinct, or absentee or early voting ballot grouping drawn for audit.489
For 2024, the jurisdictions and contests audited is State Senate LD 35 in Bear Lake County, State Senate LD 30 in Bingham County, State Senate LD 2 in Clearwater County, State Senate LD 8 in Elmore County, State Senate LD 26 in Jerome County, State Senate LD 6 in Latah County, and State House LD 27 in Minidoka County. All pollbook/vote count discrepancies were predictably attributed to human error whenever an explanation is provided. Tabulation error as an explanation was never once invoked despite audited precincts adding up to well in excess of the thousand vote mark in which random optical scan error, even in the best circumstances, would become inevitable.490
Illinois
10 ILCS 5/24A491 describes the operation and testing of defunct mechanical voting devices which are (unfortunately) no longer used in any jurisdiction in the state of Illinois. 10 ILCS 5/24B issues ordinances for the operation and testing of precinct optical scanning tabulators and 10 ILCS 5/24C provides for the operation and testing of direct recording electronic voting machines.
As an additional check to the standard procedures of post-election canvassing in optical scan jurisdictions, election authorities shall retabulate the total number of ballots cast in 5% of precincts within the boundaries of the optical scan jurisdictions, alongside 5% of voting devices used for early voting, which are randomly chosen by the State Board of Elections. The retabulation shall consist of counting the ballots which were originally counted and shall not involve any determination of which ballots were, in fact, properly counted, evoking the inference that only reconciliation of ballot counts is considered and not vote counts, begging the question of why they even bother to call it a “audit” of election results at all when it’s a glorified canvass. The audit also tests the optical scanners’ ability to reject overvoted ballots. If any error is detected, the auditors shall determine the cause and “correct” the error, establishing an errorless count before publishing the results. Statute is silent on how discrepancies relating to ballot reconciliation or errant voting results would be troubleshooted, and whether or not the audit is open to the public. Hand- or machine-marked paper ballots in optical scan jurisdictions are statutorily required to be retabulated by machine. Thus, there is no way to adjudicate QR-code/human readable text discrepancies, and election attacks consisting purely of electronic vote theft will never be detected by the audit [10 ILCS 5/24B-15].492
Nearly identical procedure is outlined in 10 ILCS 5/24C-15, which applies to election jurisdictions that vote using DREs for all in-person voters. However, DRE voter-verifiable paper audit trails may be audited by hand or machine, depending on the caprices of the election authorities.493
Direct recording electronic voting machines are still used for accessibility purposes in polling places in Rock Island County and Knox County. Ballot marking devices are used for accessibility purposes in all other counties, and are used exclusively for in-person voters in Kane County.494 Statute is silent in regards to the auditing of mail-in ballots. The audit can be expanded to other auditing units after proclamation of the results under a court order to unseal ballots by the very provisions prescribed hitherto.
Iowa
The Iowa state commissioner of elections is required to cooperate with county election commissioners in order to advance a smooth post-election audit of the official canvass of votes from the preceding general election for President or Governor as stipulated by Iowa Code § 50.51.495 The state commissioner will determine which counties, and precincts thereof, shall be audited by lot through means of a hand count by the respective county audit boards, and if a absentee/special vote pseudo-“precinct” is selected for audit, then, per Iowa Admin. Code r. 721-26.203(4), the audit board shall review, by a machine/hand comparison count of at least 50% of votes in that “precinct” but no more than 2,000 votes.496
Iowa Admin. Code r. 721-26.201 specified that the commissioner of elections must select audit units by lot the day after the preceding general election.497 These legal regulations have, as of late, been found in the breach — how the dynamics of such improprieties might manifest are addressed in the report “Concerning Findings of the 2024 Iowa General Election”;498 thus, I will not go into much detail here.
Kansas
Kan. Stat. § 25-3009 requires county election officers in Kansas to conduct a pre-certification manual audit of all ballots cast in a 1% random sample of precincts, for a minimum of one precinct, within the boundaries of the jurisdiction that they are assigned to. In presidential general election years, the races audited consist of one federal race, one state legislative race, and one county-level race, while during midterm years, audits are required in one more additional statewide race.499 Mail-in ballot-only elections and local ballot initiatives are exempt from the audit [Kan. Admin. Regs. § 7-47-1].500 The results of the audit shall be compared to the unofficial election night returns and a report shall be submitted to the county election office and to the secretary of state’s office prior to the meeting of the county board of canvassers. If a discrepancy is reported between the audit and the unofficial returns and cannot be resolved, the county election officer or the secretary of state may require audits of additional precincts [Kan. Stat. § 25-3009 (d)].
Two local elections may be randomly selected for audit in precincts in the county where that local election is on the ballot during off-year elections at the discretion of county election officers, per Kan. Stat. § 25-3009 and Kan. Admin. Regs. § 7-47-1.
Kan.Stat. § 25-3009 (b)(2)(C) was defined by HB2138 (2022) to provide for extraneous audits, additionally to the standard 1% of precincts audit, in even-numbered election years for any federal, statewide or state legislative race whose margins are within 1% of the total number of votes cast tallied on election night, votes cast for that race in 10% of precincts in the county, as determined by the Secretary of State, shall be audited.501 The county election officer shall conduct the audit in the manner set forth in other sections of state election law for specified race, with a minimum of one precinct in the county subject to audit.
33.5% of Kansans live in counties using unverifiable ballot marking devices for all in-person voters, while another 1.7% live in counties using all hybrid BMDs.502 82.5% of registered voters use voting systems manufactured by ES&S, while another 5.4% use Dominion voting machines. the remaining 12% use systems serviced by Unisyn and Clear Ballot.503
Kentucky
The post-election canvass of ballots in Kentucky is accompanied, according to procedures prescribed by Ky. Rev. Stat. § 117.383(8), with a manual audit of one optical ballot scanner, randomly selected by the Secretary of State or a designee to which their authority is delegated, and votes for one contest tabulated by that optical scanner, in each county in the Commonwealth to gauge the accuracy of the tabulator. If a discrepancy between the hand-eye count and the machine tape is detected, the county board of canvassers shall open an investigation, and discrepancies shall be resolved. A determination as to whether the outcome of the race could have been impacted by the discrepancies shall be made and any findings shall be reported to the Attorney General and Secretary of State.504
4.1% of registered voters live in counties using unverifiable ballot marking devices for all in-person voters.505 68.4% of registered voters use voting systems manufactured by Hart InterCivic, and the remaining 31.6% use ES&S equipment to vote.506
Maryland
After a general or primary election in the state of Maryland, according to Md. Election Law Code Ann. § 11-309(d) the local election board of each county shall conduct a manual audit of at least 2% of precincts in the state, under the conditions that those precincts include at least one precinct per county, a quantity of absentee and provisional ballots canvassed during the post-election canvass, and one early voting center per county, such that the sample of early voted ballots, absentee ballots and provisional ballots encompass at least 1% of those votes cast during the most recent election preceding the audited election in question, within 120 days of an election.507
Per Md. Election Law Code Ann. § 11-309(b)(1), the state will also conduct an additional “automated software audit” of digital ballot images exported by the state’s optical scanners. Md. Code Regs. 33.08.05.09(C)(2) and its subsections clarify that the State Board of Elections has the authority to select which race(s) will be audited, and that the early voting center, along with one ballot scanner, will be chosen by the Chair of the State Board of Elections or a designee within three days before the start of early voting. If a discrepancy of 0.5% is detected then the State Administrator shall require the local board to resolve or explain the discrepancy and may expand the manual audit [Md. Code Regs. 33.08.05.09(A)(2).508
Tallies of digital ballot images are highly controversial and likely have little probative value in the determination of fraud, error, or absence thereof.
Massachusetts
Mass. Gen. Laws, ch. 54 § 109A directs boards of registrars in each county to conduct a manual audit of ballots in 3% of precincts in their jurisdiction, for contested races for president, U.S. Senate, representative to Congress, representative and senator in the Massachusetts General Court, and one statewide ballot question, if any appear on the ballot, chosen by random drawing. The random, non-computerized selection of precincts to audit will be supervised by the Secretary of the Commonwealth two days after Election Day, and the audit will be conducted two days afterwards.509
Most municipalities count votes electronically using optical scanners and BMDs for accessibility, however, fifty-one rural municipalities in the western part of the state largely count their ballots, observably and by hand.510
Michigan
As prescribed in Mich. Comp. Laws § 168.31a the Secretary of State shall design procedures to carry out the optional post-election audit of election documents and ballots, and a comprehensive review of procedures used during the election.511 Statute is silent on the counting method, but the Michigan Post-Election Audit Manual specifies that ballot auditing will be done strictly by a hand count.512 The audits themselves will be carried out by qualified county clerks certified by the state secretary, so long as they have not been prohibited from having any role in the supervision or administration of the audit, or their designee, and county staff.
In 2018, Michigan began implementing administrative risk-limiting audit pilots for local elections on an increasing scale. The state conducted its first statewide RLA pilots of the 2020 presidential primary and general elections. Michigan continues to pilot post-certification RLAs administratively.
There are no provisions specifying the limits of the number of precincts that can be audited, meaning that Secretary of State could possibly select every precinct in the state to audit, or barely any at all. Audit results are not binding on election results, as they are conducted after certification.
Missouri
Mo. Code Regs. tit. 15, § 30-10.110 specifies that, prior to certification of the election, the accuracy certification team is charged with drawing 5% of precincts in the county, such that at least one precinct is selected, to be subject to a manual election audit. Contests audited must include, but are not limited to, at least one of the following: the presidential, senatorial or statewide contest, a statewide ballot initiative, a U.S. House contest or race for the Missouri General Assembly, or partisan circuit and associate circuit judge candidacies and all nonpartisan judicial retention candidacies. Additionally, at least one local contest must be audited, as well as any contest whose separating margins between the top two candidates is less than 0.5%.513
Pursuant to Mo. Code Regs. tit. 15, § 30-10.110(4), if the discrepancy between the manual audit results for a race diverge from the results of the electronically tabulated vote results, the auditing team shall immediately notify the election authority, who shall investigate the causes of any discrepancy and “resolve” any discrepancies prior to the date of certification. However, the process of audit escalation or recounting in response to a major discrepancy is not statutorily addressed.
The accuracy certification team is a bipartisan team appointed by an election authority — defined as a county clerk or board of election commissioners — responsible for logic and accuracy testing, election administration, ballot adjudication, maintenance of chain of custody, and, in the pertinent context, conducting audits. Accuracy certification team members are appointed by the election authority based on lists supplied by the major parties of the state, unless if the authority is a board of election commissioners, which then it is allowed to choose qualified personnel at its sole discretion. The teams are necessarily composed of at least two members in order to ensure that both parties have equal representation in the team [Mo. Code Regs. tit. 15, § 30-10.040].
The random selection of precincts can be observed by the public. Statute is silent on whether or not counties must open up the process of auditing to the public, or to media or party representatives.
Montana
Per Mont. Code Ann. § 13-17-503, audits are required to be conducted after each federal election, and prior to the post-election canvass, by county audit committees. All ballots, except for rejected and unresolved ballots spoiled by undervoting, overvoting, blankness or ambiguous voter selection that prevented its processing by optical scanning tabulators, are to be included in an audit of 10% of precincts across the state.514 Elections for at least two federal offices, two statewide offices, if any, two legislative office races, and two statewide ballot issues if statewide ballot issues were on the ballot, all as identified and selected by the state board of canvassers, and one countywide race if requested by the board of county commissioners using the process prescribed in Mont. Code Ann. § 13-17-510.515 The audit cannot include a judicial retention race or any race where the candidate had ran unopposed, and races subject to impending recount are similarly exempt from the audit [Mont. Code Ann. § 13-17-503].
Nebraska
A post-election audit is not required by a statute, but may be conducted at the discretion of the Secretary of State. According to a 2022 press release, in 2022, the Nebraska secretary of state increased the percentage of precincts audited to 10% from between 2 and 2.5%, with a minimum of one precinct audited in each county. One federal and statewide election, and one local election at the county level.516
New Hampshire
In New Hampshire, the Secretary of State must select not less eight ballot tabulators to be audited following state primaries, presidential primaries and general elections. 2% of ballots, or fifty ballots, whichever is greater, that are recorded by these tabulators are set aside for manual tallying and hand-count/machine-count comparison, while the remaining 98% are simultaneously subject to machine retabulation. [N.H. Rev. Stat. Ann. § 660:35].517
New Jersey
Elections for federal offices and for gubernatorial or state legislative offices in New Jersey are audited under N.J. Rev. Stat. § 19:61-9, alongside whatever local contests chosen at the discretion of the Secretary of State. Election Day ballots cast at a polling place are audited in 2% of precincts per county, in every county, though county and municipal elections administered across jurisdictions with less than one hundred total precincts are exempted from this requirement. Ballots not cast on Election Day, as well as ballots cast provisionally and by UOCAVA voters, are organized into anonymized batches (“audit units”), each with a number of ballots equal to the average number of ballots cast across each precinct in the associated county, that are intended to preserve voter privacy. If the initial audit reveals discrepancies of one-tenth of one percent or more, the audit is expanded, and an additional sample of precincts is audited. The law specifies that the expansion should equal the same number of precincts that were initially audited and, when possible, the same number of audit units. If the initial number of precincts audited is already greater than half the precincts for the election contest in question, then a full manual count for all remaining precincts must be conducted. Further hand-eye count retabulations shall be conducted if the audit team identifies a substantial possibility that continued hand-machine count discrepancies could alter the outcome of one or more elections on the ballot.518
31.8% of New Jersey voters live in jurisdictions that deploy unverifiable ballot marking devices for all in-person voters, and another 67.5% deploy doubly unverifiable ES&S ExpressVote XL hybrid BMD/tabulator voting devices for all in-person voters. Another 0.7% of voters, in Salem County in the southern part of the state, vote on direct recording electronic voting machines that print out voter-verifiable paper audit trails.519
In 2021, Governor Phil Murphy signed into law Senate Bill 3203, requiring that, among other provisions (such as universal early in-person voting), sixteen of the state’s twenty-one counties transition to the use of voting machines that produce auditable paper trails,520 as opposed to the paperless DREs then in use during the 2020 presidential general election.521 They now use all BMDs, including Essex County, which used optical scanners and hand marked paper ballots in 2020, and paperless DREs for accessbility purposes. Evidently, “auditability” means transitioning to a new era of identically unverifiable electronic jank.
New Mexico
Per N.M. Stat. § 1-14-13.2, audits in New Mexico are conducted no later than twelve days each statewide election or as soon as practicable prior to an election to fill a vacancy in the office of United States representative, the Secretary of State shall contract with an auditor qualified by the state auditor to audit state agencies to oversee a check on the accuracy of precinct electronic vote tabulators, alternate voting location electronic vote tabulators and absent voter precinct electronic vote tabulators, and should provide at least a 90% chance of detecting tabulation errors that alter the outcome of an audited contest, though there is no statutory guidance on troubleshooting non-decisive tabulation errors.522
The voting system audit is conducted for elections for federal office, the office of governor, the “regular local office”,523 and the statewide office (other than for governor) for which the winning margin is the smallest of all simultaneously administered contested statewide races. If the winning margins for any of the aforementioned races decreases, and the error rate is at least 90% of the winning margin for that office, then the auditing process will be repeated for a second sample of precincts differing from the first. If the discrepancies continue then the state canvassing board will order the execution of a full hand recount of votes cast for that elected office. The voting system audit is waived for any race with margins narrow enough such that a automatic recount is initiated.
The auditor will publicly select a random sample of precincts to audit separately for each election in the audit. The audit sample size is calculated based on the winning margin of the top two candidates according to the county canvass, from as low as four precincts for an election with a winning margin of less than fifteen points but more than fourteen points, and the sample size exponentially rises as the winning margin decreases towards zero. Noncompetitive elections of a winning margin of more than fifteen points is not required to be audited [N.M. Stat. Ann. § 1-14-13.2(B)]. An extra precinct will be randomly selected from every county where a precinct was not already sampled, such that every county is represented in the audit sample by at least one precinct [N.M. Stat. Ann. § 1-14-13.2(C)]. Comparisons for the manual audit and originally canvassed machine count for the three contested regular local offices with the narrowest margins are also conducted [N.M. Stat. Ann. § 1-14-13.2(D)(2)].
To reduce the chance of detection, an attacker is incentivized to maximize the margins of the elections for statewide office at around 5.5 points or above to minimize the number of audit precincts at or below a sample size of ten. Or, they might steal a statewide election to a vast enough extent that the artifactual winning margin exceeds fifteen points anyways.
All counties in New Mexico use Dominion ImageCast Evolution hybrid optical scan/BMD tabulators for all in-person voting. They are also used for processing mail-in ballots in twenty-four counties.524 However, interestingly, the counties provide the option of hand marked paper ballots to in-person voters, so they’re not necessarily at the mercy of the unrecoverable caprices of those hybrid machines, though they can still mark extraneous and unwanted ballot selections into unvoted races (resulting in lower-than-expected undervote rates for certain races) or they can spoil ballots with overvotes (leading to higher-than-expected uncounted ballots for certain races).
We might expect that, in counties that use the Dominion ImageCast Central batch-fed tabulator for processing mail-in ballots, uncounted vote rates might be lower for absentee ballots than other methods of voting. Of course, ICE voting machines might be fixed to overvote some ballots and fill in undervotes for other ballots for the same races, attenuating or eliminating the undervote/overvote discrepancies. Nonetheless, a non-negligible proportion of ballots cast in New Mexican elections are susceptible to irrevocable fraud that cannot be audited. The number of voters who may utilize the BMDs is possibility within the range of 2-3%.
Audits cannot be expanded in the event of any discrepancy, only a unidirectional total discrepancy that is at least 90% of the margins for the winning candidate. It is not an RLA for these reasons.
New York
Within fifteen days of a general or special election, within thirteen days of a primary election or within seven days after every village election, the county boards of elections of New York, or a bipartisan committee appointed by the boards of elections, will conduct an audit of all the votes on the voter verifiable paper audit trails associated with votes cast on three percent of voting systems in the county [9 CRR-NY 6210.18].525 The audit may be conducted manually or by an “automated tool” (secondary electronic vote tabulation system) approved by the State Board of Elections [ELN § 9-211].526
If the unresolved error between the audit vote totals and the machine tabulation exceeds 0.1% of all votes counted in the hand count, or discrepancies are observed from ten percent of audited machines, then the audit can be expanded to an additional five percent of machines in the county. If discrepancies persist then the county may audit an additional twelve percent of voting machines, and further discrepancies shall compel each county board to manually count all voter verifiable paper audit trail records from all the remaining unaudited machines and systems where the contest appeared on the ballot [9 CRR-NY 6210.18].
Neither canvassing nor recanvassing in New York involve the inspection, manual or otherwise, of voter selections. Statute is unclear if paper ballots are subject to audit.
Columbia County, in the far eastern part of the state, conducts a full hand recount of its ballots after each election, and has done so since 2010.527
North Carolina
The North Carolina State Board of Elections to implement rules and standards governing the conduct of post-election manual audits in two precincts per every county. Elections audited may only include one statewide ballot item; for presidential general election years, this is the presidential election, allowing downballot races for state elected office to fully escape auditing quadrennially. If there is no statewide ballot item, the State Board shall provide a process for selecting district or local ballot items to adequately sample the electorate [N.C. Gen. Stat. § 163-182.1].528
In the event of a discrepancy between the hand count and the original machine count, then the hand count will take precedence except where paper ballots have been lost or destroyed or where there is “another reasonable basis to conclude that the hand‑to‑eye count is not the true count.”. If the discrepancy between the two counts is “significant” then a full hand count audit will be conducted. Statute is silent on whether or not that full hand count audit is conducted at the scope of the entire county or entire state.
All in-person voters in Cherokee, Davie, Davidson, Jackson, Mecklenburg, Perquimans and Warren counties use ballot marking devices, accounting for 13.5% of all registered voters in the state. The remaining 86.5% of voters live in areas with the option to mark their ballots by hand, or use BMDs only for accessibility purposes.529
North Dakota
In 2024 and after, North Dakota conducts audits of ballots at one polling place per county six days following an election. Whenever available, one election for federal office, statewide elected office, legislative office, and county-level office are subject to audit. If an error separating the audit returns and the unofficial reported election results at the examined polling places is identified, then the audit returns will take precedence, and the Secretary of State may authorize additional auditing. The statute makes no references to the observability of the audits or the counting means according to which the audits are conducted [N.D. Cent. Code § 16.1-06-15].530
Ohio
County boards of elections in Ohio must conduct summary post-factum audits of three contested races for elected office, questions or issues, as directed by the Secretary of State, unless if there are fewer than three votable elections on the ballot, whereupon all contests are audited; any election is eligible to audit [Ohio Rev. Code § 3505.331].531
Counties may use risk-limiting audit methods in order to minimize the risk of certifying incorrect election results, or physically examine and hand count a fixed-percentage of ballots cast. They may also use other auditing protocol that satisfy certain requirements prescribed by the Secretary of State. In the event of a fixed-percentage audit, if the error between the hand count and the machine tabulation exceeds a maximum acceptable error rate prescribed by the Secretary of State, then the county board of elections shall order an escalation of the audit by sampling a parallel batch of ballots, so long as the secondarily audited ballots contains no transplants from the initial audit batch. If the unacceptable errors persist, then the Secretary of State may order a full hand recount of the contested races on the ballot across the entire county.532 Canvassed results are amended to match the recount results. Audit units for the fixed-percentage audit is usually around 5% of all ballots cast.
The audit units for the risk-limiting audit may impound individual ballots or ballot batches, depending on the exact method used by the county. The fixed-percentage audit may be conducted over discrete precinct-level, polling place-level or voting machine-level audit units.
34.6% of registered voters in Ohio live in counties that use ballot marking devices for all in-person voters. Another 1.9% live in areas that exclusively utilize ExpressVote hybrid BMD/tabulators manufactured by ES&S. 14.9% of in-person voters are forced to vote on direct recording electronic voting machines in twelve counties. The remaining 48.6% of voters use hand-marked paper ballots counted by optical scanners, and BMDs are used to satisfy ADA voter accessibility requirements. 47.3% of registered voters use ES&S tabulation systems, 16.7% use Dominion, 7.1% use Hart Intercivic, 23.4% use Clear Ballot and the remaining 5.6% use Unisyn machines. A large fraction of Clear Ballot’s significant share of the voting system market in Ohio is because Cuyahoga County uses their optical scanning and ballot marking equipment.533
Oklahoma
Oklahoma’s audit statute, first enacted in 2019 and revised in 2025 (effective 11/1/25), delegates the authority to direct counties’ conduct of audits to the secretary of the State Election Board, and to develop and promulgate policies, rules and procedures to achieve that end, for the purpose of maintaining the security of the election system by ensuring that voting devices and software used in a particular election correctly tabulated votes. The audit may be conducted manually or electronically at the discretion of the county. No statutory guidance is provided to define the audit units for the audit, though most counties elect to sample at the precinct-level. The audit must be conducted after general, primary or special election [Okla. Stat. tit. 26, § 3-130].534
All voters in Oklahoma live in jurisdictions that use optical scanners with hand marked paper ballots, and paperless direct recording electronic devices for accessibility purposes.535
Oregon
After each primary election, general election and special election, counties in Oregon to conduct a traditional hand count audit of a certain percentage of precincts, or a risk-limiting audit. If the county clerk opts for a hand count audit, then the precinct sample size is determined to be inversely proportional to the winning margin of the audited contest between the two leading candidates, according to the unofficial results reported by the voting system. If the margin is less than one percent then the county shall audit in at least 10 percent of all precincts or of ballots in at least 10 percent of all batches of ballots collected by the county clerk. If it is between one and two percent then at least five percent of all precincts or of ballots in all batches shall be audited. Finally, if the audit extends beyond two percent then at least three percent of ballots in all precincts or ballot batches shall be audited. The Secretary of State selects the precincts or batches at random [Or. Rev. Stat. § 254.529].536
Per Or. Rev. Stat. § 254.529(3), the audited races must impound the election with the most votes cast for it, a race voted on by voters in the state at large, and a ballot measure if possible. If precincts are audited, they must have at least 150 ballots cast in them.
County clerks have the authority to initiate a risk-limiting audit of county-level elections. For the risk-limiting audit of elections that span multiple counties the county clerk may petition the Secretary of State to establish regulations enforcing the requirement that other county clerks within the jurisdiction of the contested elected office in question cooperate to conduct the multi-county audit. Alternatively, the county clerk can directly request that other clerks coordinate to conduct a multi-county risk-limiting audit [Or. Rev. Stat. § 254.532].537
If the error rate for the hand count audit exceeds 0.5%, then the county clerk shall conduct a second audit of the same sample of ballots, and if the error rate still exceeds 0.5% then they shall order a hand count of all ballots cast in that county. The hand recount results will go on to be certified. If the initial hand count audit results, or the secondary audit, diverge from unofficial results by less than 0.5% then they will amend the unofficial results and be certified. The risk-limiting audit may also expand into a full hand recount if it provides considerable evidence that the reported results are incorrect.
South Carolina
S.C. Code § 7-3-20(D)(19) requires the executive director of the South Carolina State Election Commission to establish methods of auditing election results, which may include risk-limiting audits, hand-count audits, results verification through independent third-party vendors that specialize in election auditing, ballot reconciliation, or any other method deemed appropriate by the executive director. Election result audits may be conducted in all statewide elections after the election concludes, but prior to certification by the State Board of Canvassers, and may be performed following any other election held in the State at the discretion of the executive director.538 According to the SEC website,539 these audits primarily involve the hand counting of ballots in an unspecified percentage of early voting centers and Election Day polling places, and a Clear Ballot automated digital ballot image audit of all votes.
Auditing is optional. No statutory guidance is provided on whether or not audits are binding on election results, and how administrators can expand an audit if discrepancies are found.
All registered voters in South Carolina live in jurisdictions that use unverifiable ballot marking devices for all in-person voters.540
South Dakota
The law of South Dakota requires that 5% of polling place precincts, randomly selected without a computer, per county are to be subject to a hand count audit, such that at least one hundred ballots or more are in the audit sample. Statute explicitly states that absentee “precincts” are exempt from the audit. One contest that is a statewide election must be audited; if no such contest is available then another randomly selected contest is chosen. If only one contest is on the ballot then that is chosen to be audited [S.D. Codified Laws § 12-17B-20].541
If there is a discrepancy shown by the results of the post-election audit that is greater than the margin by which any contest for elected office on the ballot in the county was decided, the auditor must notify each candidate for that office. Any candidate who receives a notification from the county auditor has an additional seven days from the date the auditor sends the notification to file a verified petition requesting a recount of the official returns. The petition may be filed regardless of the margin by which the contest was decided [S.D. Codified Laws § 12-17B-23].542
Tennessee
For elections held during and after 2024, the Secretary of State of Tennessee must prescribe the procedures to county election commissions to conduct audits in three counties after August elections and six counties after November elections. The races audited include the presidential and gubernatorial race after a general election where the race for president or governor is on the ballot and, after August elections, the highest election on the ballot will be audited, alongside any other election that the chosen county election commission selects to audit at its own discretion. The protocols used by the counties to audit after an election must be approved by the Secretary of State and include traditional tabulation audits or risk-limiting audits [TN Code § 2-20-103(a)]. County election commissions in counties not selected by the Secretary of State will still audit ballots by retabulating Election Day ballots through optical scanners reserved for early voting, and early voted ballots rescanned by optical scanners reserved for Election Day. At least one precinct is audited in these counties when the it has less than 300,000 residents, and, else, at least five precincts are subject to audit. If the initial machine audit reveals discrepancies of more than 1%, the audit is expanded to include “at least” 3% of voting precincts (which may include the same precincts audited in the original 1%). This second audit is conducted by machine, but at the discretion of the county election commission may also be done by hand. [TN Code § 2-20-103(b)].543
Texas
Tex. Elec. Code § 127.201 mandates that Texas election administrators must conduct a manual inspection of 1% of precincts selected by the Secretary of State, for a minimum of three, per county that use voting systems that create voter-verifiable paper audit trails, of votes for not more than three contests for elected office and/or three ballot initiatives after general elections for state and county officers, primary elections, or any election with proposed state constitutional amendments or statewide ballot measures. If an election is held that doesn’t fit the aforementioned description, then all ballot items are included in the hand count audit. While candidates and their appointed representatives are allowed to observe the audit, there are no provisions that mention their ability to verify ballot marks. While appointed observers are allowed, there is also no mention of the general public’s ability to attend, and no requirement for the time and location of the audit to be publicly announced. Audit results are not binding upon election results.544
87.2% of registered voters in Texas live in jurisdictions that deploy unverifiable ballot marking devices for all in-person voters. These include ES&S AutoMark and ExpressVote BMDs, which encode voter selections as theoretically verifiable human-readable plaintext and unverifiable barcodes, and Hart InterCivic Verity Duo and Verity Touch Writer BMDs that lack the faith-based barcode/QR-code functionality. Another 0.3% of voters use paperless DREs for all in-person voters, manufactured jointly by ES&S and Hart InterCivic. The remaining 12.2% of voters live in hand-marked paper balloting/optical scan regions that deploy BMDs for accessibility purposes. 50.4% of registered voters use Hart InterCivic, while the other 49.6% of voters use ES&S voting equipment. Additionally, another three counties, Collingsworth, Foard and Glasscock counties, in Central Texas and the Panhandle region, count hand-and machine-marked ballots by hand.545
Utah
Utah county election administrators are required to conduct post-election audits of one percent of ballots cast within their jurisdiction, for a minimum of 50 ballots and up to 1,000, with at least one batch audited from each scanner used in the election. One percent of paper trails generated by DRE machines are also audited where they are used. After every general election, election officers audit the highest federal race on the ballot, the governor’s race (if on the ballot), a state legislative race, a countywide race, a ballot proposition, and any race within a 5% margin at the time of the audit. The audit of direct recording electronic machines is performed manually, however, the corresponding audit of hand-marked paper ballots can be done manually or by audit of digital ballot images stored on the county central election management system.546
The audit is not binding on the official election results and cannot lead to a full recount.
65.6% of registered voters in Utah use hand-marked paper ballots and optical scanners, and ballot marking devices for accessbility purposes. The one county, accounting for the remaining 34.4% of registered voters, that uses unverifiable direct recording electronic voting machines with voter-verifiable paper audit trails, is Salt Lake County, which contracts out to Dominion Voting Systems. One county utilizes Unisyn tabulation systems, and the rest of counties use ES&S machines.547
Vermont
17 Vt. Stat. Ann. § 2493 requires that the Secretary of State must audit a random selection of polling places from the pool of polling places, which includes those who count ballots by hand on Election Day.548 Statute does not specify sample sizes, however, the Code of Vermont Rules 04-010-001(E)(a) specifies that the Secretary of State must conduct a random audit of at least six polling places election results within thirty days of an election.549 The audit is binding upon official election results.
All registered voters in Vermont live in jurisdictions that either have voted to use a vote tabulator, who “shall use a uniform vote tabulator approved by the Secretary of State” [17 V.S.A. § 2493(a)(1)] (in this case Dominion optical scanners) or smaller, rural jurisdictions that count ballots by hand.
West Virginia
W. Va. Code § 3-4A-28(d) requires canvassers to conduct a manual audit of paper ballots and voter-verifiable paper audit trails in three percent of precincts during the post-election canvass. If a discrepancy of more than one percent exists between precinct unofficial results and the results of the auditing of the paper records for that precinct, then the audit results will take precedence over the original tabulated results. However, there are no provisions relating to escalating the audit in any way.550
89.5% of registered voters live in jurisdictions that deploy unverifiable ballot marking devices for all in-person voters. 4.8% of registered voters live in jurisdictions that use doubly unverifiable hybrid BMD/tabulators for all in-person voters. The remaining 5.7% of registered voters vote on hand-marked paper ballots that are optically scanned, with the option of BMDs for accessibility purposes. All counties use equipment manufactured by ES&S.551
Wisconsin
Following each biennial general election, Wisconsin county clerks shall manually audit validly cast votes tabulated by optical scanners for three randomly selected contests, plus the contest at the top of the ballot (the presidential race in 2024), in order to ensure compliance with federal standards for voting system error rates administered by the Help America Vote Act of 2002. As its only statutory purpose is to ensure an optimal machine error rate, it is not binding upon election results and cannot be expanded into a recount [Wis. Stat. § 7.08(6)].552
Counties audit ballots at the level of reporting units, which are defined as wards (precincts) or aggregations of wards. For 2024, the rules are such that four reporting units can be selected for the two largest municipalities of Milwaukee and Madison, three reporting units for the following twenty largest municipalities, and one reporting unit for the rest of the municipalities in the state in order to obtain the requisite percentage of audited reporting units needed to fulfill the requirements listed hereinafter. During the 2012 and 2016 presidential general elections that sample size included a flat and inflexible total of one hundred reporting units, but by 2018 this had been expanded to 5% of all reporting units in the state, for a total of 186. For 2022 and 2024, this is now 10% of reporting units.553
The WEC instructs auditors to disallow the interpretation of voter intent from ballots rejected by tabulators for ambiguous markings of votes, such that they must count votes as the machine would, which partially defeats the very purpose of an audit designed to gauge machine error rates. Unclean scan heads, bleed-through of penned ballot ink, votes falsely assigned to the wrong candidate, validly marked votes unread by the scanner, and so forth are attributed to equipment error. Human error is defined as error arising from unclear voter intent, “errors in tallying votes during the audit”, ballots from other reporting units being accidentally included in the audit sample for another reporting unit, etc.. Despite the fact that mistabulation errors are evidently quite common, especially, without reference to Election Day malfeasance, in Wisconsin, administrators still have the audacity to attribute almost all error, happening at a rate that is unrealistically low, to human error.554
Townships in about half of Wisconsin’s counties use Dominion ImageCast Evolution hybrid optical scan/BMDs for tabulating ballots as an optical scanner would, and the casting ballots by disabled voters,555 providing the opportunity for attackers to replace undervotes on validly cast ballots with stuffed votes, or irrecoverably steal votes cast using the ballot marking function. They could even draw unwanted, haphazard markings for voted races that would be read by the optical scanner as an overvote, causing it to reject the ballot under normal operation and exempting them truly being audited. Portage County uses ballot marking devices for all in-person voters.556
There are thousands of reporting units across the entire state and hundreds in urban counties and municipalities. Allocating only, for example, four audited reporting units to the largest municipalities would generate a sample that is both non-random and asymmetric on the basis of county size and urbanity. There would necessarily be a undersampling of ballots from urban areas, like Pennsylvania and Georgia, and many other states; indeed, there is such an undersampling in the 2024 Wisconsin audit.
Wyoming
Wyo. Stat. § 22-6-130 requires county clerks to complete an audit of the county’s unofficial election results by identifying and reviewing the smallest observable percentage between the statewide candidates who received the most votes and the statewide candidates who received the second highest votes for each contest within the county not later than the first Thursday following a primary, special or general election. Additional contests may be audited at the discretion of the county clerk. No more than 5% of ballots shall be audited.557
Statute provides no guidance as to how ballots should be counted. However, in 2022, the state’s audit policy instructed county clerks to use the EMS to compare the ballot with the corresponding cast vote record.558 In practice, this means comparing digital ballot images, which can be doctored by the voting system, to cast vote records, which can be edited by the voting system and are reproduced from the DBIs.
Compulsory fixed-percentage audits that induct 3% or less of precincts or ballots for manual tallying are present in thirteen states: Arizona, California, Florida, Kansas, Maryland, Massachusetts, Minnesota (for large counties), New Jersey, New Hampshire, Pennsylvania, Texas, Utah, and West Virginia. 5% of precincts are audited in Colorado (with authorization), Connecticut, the District of Columbia, Idaho, Illinois, Missouri, Ohio, South Dakota and Wyoming. States that count ballots in 10% of precincts are Hawaii, Montana, Nebraska (with SoS authorization), and Wisconsin.
Fixed-percentage/sized audits of a preset quantity of ballot scanners or voting machines are utilized in three states: Kentucky, New Hampshire and New York. Vermont audits votes cast on the polling place-level, which may be inequivalent to precincts in those areas (typically urban) where polling places serve multiple precincts.
Even in the ideal scenario of truly randomized ballot sampling, and zero sabotage, fixed-percentage audits are not considered to be robust, and have a low-chance of detecting mistabulation. The audit described in Wisconsin’s statute has severe sampling issues that will, and does, disproportionately miss reporting units in urban regions; regions which, logically, an outsider would hack.
Three states impose limits on the audit sample size in any given jurisdiction, spanning on the scope of individual counties. The Arizona Revised Statutes specify a early ballot sample size upper-limit of only 5,000 ballots in each county. The Pennsylvania Statutes define a maximum county-level sample size of 2,000 ballots for its longstanding, eighties-era fixed-percentage canvassing ballot audit. Audit policy for the state of Utah allows for a maximal sample size of only 1,000 ballots per county.
One state prescribe provisions for running optional fixed-percentage manual tallies in some subset of counties within the boundaries of the state: Indiana. Arkansas, Idaho and Tennessee conduct non-optional fixed-percentage manual audits in only a fraction of counties. Five states used fixed-size auditing techniques, and these are Alaska, Delaware, New Hampshire, North Carolina and Vermont. Nebraska law allows the Secretary of State to optionally authorize an audit an arbitrary number of precincts in the state, which usually enumerates to 2-2.5% but included 10% in 2022.
Audits in Georgia, Maryland, South Carolina, Utah and Wyoming may involve the automated tabulation of votes recorded on digital ballot images exported by voting systems. Human inspection of images is apparently not done, meaning that erroneous or malicious replications of image files will likely go undetected.
Four states optionally allows counties to tally ballots using automated batch tabulation systems, and those are Connecticut, Florida, Hawaii and Oklahoma. Four states do not have audit provisions. These are Alabama, Louisiana, Mississippi, and North Dakota. Maine did not have audit provisions until January 2025.
Six states require the use of risk-limiting audits. These are Colorado, Georgia, Nevada, Pennsylvania, Rhode Island and Virginia. Another five states, Indiana, Maine, Michigan, Ohio and Oregon, allow the optional use of risk-limiting audit methods by either county administrators or the Secretary of State. In Ohio, in 2024, ballot-polling audits were used in Cuyahoga County and Hamilton County.
As Georgia, Nevada and Pennsylvania witness a significant usage of unverifiable voting systems, RLA methods are mostly or entirely worthless in these states. As such, only three states conduct audits that might catch outcome-determinative errors or fraud: Colorado, New Mexico (which technically doesn’t use RLAs), Rhode Island and Virginia. However, the Virginia auditing process can be easily predicted, circumvented and avoided, and New Mexico utilizes hybrid tabulator/BMDs which can print extraneous votes onto hand-marked ballots, reducing that pool to two of fifty states.
5.3. Internet Voting
The final topic we will address in this section is the otherworldly abomination known as Internet voting. While varying in method, allowing voters to cast votes remotely by fax, email or web portal, they are used in thirty-two states to facilitate voting by uniformed and/or overseas, or UOCAVA, voters.559 The Internet voting environment is, of course, wholly administered by private corporations, such as the defense contractor Ecompex going back to the Bush era. We will, for the sake of brevity, ignore said private corporation’s political leanings and complete freedom from any sort of regulation or oversight, and unfettered ability to monkey with those military voters’ votes.560
The logistics of handling hundreds of thousands of absentee ballots from overseas has been a complicated problem to overcome so the development is presumed to have been employed with good intentions, although with the strong-arming of the election industry you can’t be sure, but these setups are obviously insecure to a degree even greater than with regular, highly networked precinct voting systems, and their susceptibility to fraud is well established by decades of research,561562563564565 opening the door to undetectable, unauditable manipulation of votes and even outright ballot stuffing by criminals, cyberterrorists and international threats.
In 2010, the District of Columbia launched an inquiry into the real world reliability of Internet voting, whilst enlisting white hats to hack into the system to trial its security. In thirty-six hours the voting server was completely compromised by experts at the University of Michigan, allowing them to modify votes undetectably, violate ballot secrecy, hack the security cameras at the election board’s data center, and, without endeavoring even the slightest attempt at stealth, managed to evade the detection of officials for two days, despite said officials bearing full acknowledgement and actively searching for evidence of the breach. They even detected evidence of unidentified IP addresses originating from places in New Jersey, and even India, China and Iran, attempting to break the network. Whether or not they were intentional was another issue, though it would not be surprising in the least if they were.566567
Across the northern border, in Canada, in 2012, a distributed denial of service attack using 10,000 IP addresses on an online NDP leadership vote led to delays affecting thousands of voters. Sensing the oncoming assault upon its marketability, Scytl wasted no time claiming that its systems weren’t breached and no votes were tampered with or lost, which, if history teaches nothing else, is an unreliable promise.568
The fairly evident upshot is that Internet voting is bad.569 It is unbelievably insecure, cannot be secured, and completely unaccountable, and any votes transmitted over these systems are not trustworthy. The second, more underappreciated lesson is that there already is a significant market for electronic electoral fraud that is evinced empirically by the aforementioned cyberattacks. The Washington D.C. pilot, for example, was just that, a demonstration of merits, not even a real election, and regardless overseas hackers were attracted to it like dogs to a hunk of steak.
5.4. What Cannot Be Audited
Even if all votes were cast on paper ballots marked by hand and scanned by an optical scanner, even if chain of custody and ballot accounting procedures for the paper trail were properly administered, and even if all ballots and all ballot options were counted publicly and responsibly by hand, what still remains is an unobservable voting system that is still insecure and hackable. Not all election rigs need to be conducted by stealing votes electronically, in a way detectable by manual examination.
Poll books are records primarily used by poll workers for administrative purposes; keeping track of unused ballots, voted ballots, the number of ballots ordered by the polling station, etc.. They are also used to qualify voters by allowing them to sign their signature onto the book, which is counted for later voter reconciliation, i.e. determining that the number of voters equals or is slightly less than the number of ballots passed out. Poll workers also use poll books for the purposes of voter qualification, the process in which voters are assessed for their eligibility to vote. But lately, this process has been computerized tool with paper poll books being replaced by electronic poll books, or e-poll books, devices which do not currently undergo federal certification and which can be set-up to connect to the Internet, or communicate over a wireless network with digitized voter registration databases to automatically update loaded registration data on the device. They automatically qualify voters and allow them to sign in, and are used to assign them to the precinct that they are registered in.570571 In 2024, over 84% of voters live in jurisdictions that use commercial or in-house e-poll books.572 Because they are usually connected to the Internet, hackers can access them quite easily.573
Electronic poll books and computerized voting systems can be used in concert to violate voter privacy and the secrecy of the ballot. Malware on an e-poll book can track the exact time and date when voters sign-in to the polls, giving the attacker a list of personal information identifying the registered voter, and that can be matched with audit log data from the machines for the precinct they are assigned to. The cast vote record generated at the moment they cast their votes or scan their ballots are assigned to that voter, allowing the attacker to know, with reasonable certainty how they voted.
From there the rigger can establish a database of registered voters, tied to the best estimation of their voting preferences across time, to gauge their partisan affiliations and propensity to vote,574 and predict who they will vote for next. While “old-school”, low tech voter suppression tactics involve a considerable amount of guesswork in order to determine which voter votes for who, usually invoking some form of oblique racial profiling based on name or address, since the election rigger now knows how people vote they can strip the constituency of their adversary bare with extreme precision and low risk of harming their own likely voters.
Voter registration databases in at least some states already track voting histories, and assign party registration based on whether they voted in a party’s primary, but it's still reasonable to suspect that a registered voter might crossover to vote in another parties’ primaries in an attempt to spoil the nominations with ineffectual and weak candidates, rather than having any loyalty to that party, so purging these voters based on that can still backfire. Additionally, primary voters are a minority as far as the populace goes575 — record primary turnout in 2020 was less than one-half of the general election turnout.
Obviously, a hacker can tamper with voter records, by incorrectly designating voters of a certain background or persuasion as having already voted, to generate Election Day chaos and lower turnout. But more insidious, and circuitous, than that arises from the action of violating ballot secrecy itself.
They can also construct a database of unlikely voters whose personal information and signatures can be stolen and logged into the memory of the e-poll book in future elections to facilitate ballot stuffing. The process of voter reconciliation is an important safeguard against outsider ballot stuffing, but when that process is digitized too, it can be hijacked and those fraudulent or low-propensity voter registrations can be “signed-in” by the hacker to produce voter counts that match the inflated ballot counts. When such crucial data becomes editable by hackers and outsiders, and is rendered untrustworthy.
In the first scenario, the problem is depriving voters of the ability to vote, which cannot be ameliorated by auditing, and in the second, the problem is fraudulently submitted ballots which would be inducted into the final audit or recount and pass through with flying colors.
Sections 6, 7 and 8 will be addressed in the next part, which you can access here: https://codenogo1.substack.com/p/subverting-democracy-its-easier-than-400
https://www.nist.gov/itl/election-administration-united-states-1934-joseph-p-harris-phd p. 315 - 381 provide historical examples of corrupt electoral conduct.
And even then, there's still the issue that election fraud was never a monopoly and was perpetrated liberally by both sides. In the 1960 presidential election, an example of a national election both close enough to be rigged using traditional, local tactics and was indeed charged with having been rigged, the analysis not only imparted the determination of whether or not Kennedy really did stuff ballots, and he did, and then if it was enough to steal Texas and Illinois, but also whether or not that necessarily isn't cancelled out by the various graveyards that surely voted for Nixon.
https://web.archive.org/web/20050621083316/https://www.itl.nist.gov/lab/specpubs/500-158.htm for a perspective of such concerns from 1988.
Ibid.
Ibid.
Ibid.
Ibid.
That is not a compliment. As we will see, standards from the 1990s should not be influencing the standards which guide certification in the 2020s.
Ibid.
https://www.bradblog.com/?p=3731 — report is accessible piecewise at the bottom of the article
https://blog.citp.princeton.edu/2018/02/22/are-voting-machine-modems-truly-divorced-from-the-internet/ for discussion about this.
https://web.archive.org/web/20110114010652if_/http://www.american.edu/spa/cdem/upload/full_report.pdf — I only quote it because it’s pertinent, not for the substance. Others have exposed most of it as bogus.
See https://www.dhs.gov/archive/news/2016/10/07/joint-statement-department-homeland-security-and-office-director-national for the standard, counterfactual administrative sales pitch.
I continue to use ‘insider’ and ‘supply-chain attack’ to imply an attack propagated by a corporate insider, i.e., an election vendor. Of course this is not necessary and the computers used to program memory cards and test voting machines are connected to the Internet so an attacker grafting malicious logic to machine software as they're being prepared and distributed would count as a ‘supply-chain attack’, and an ‘insider’ might constitute a rogue poll worker. I insist upon corporate election rigging because the vendors themselves are subject to little government oversight and have well-documented partisan proclivities that are beyond the scope of this article.
https://verifiedvoting.org/verifier/#mode/navigate/map/makeEquip/mapType/normal/year/2024 — The Verified Voting database will be cited frequently in this article.
It might be tempting to grasp at the archaic dates of some (but not all) of these examples and proclaim that that means these lessons no longer apply. Of course, most of these items were aggregated by a single source that largely stopped posting after 2010, explaining all of the non-recent dates.
These are still corporations and, as in any other industry, are still profit-motivated and cutthroat, even if they are (unfortunately) de facto in charge of administering our democracy. Think of this as an introductory course.
A defunct election vendor based in Oakland, California. It has since been integrated into Dominion.
At its most extreme you have entire states, like Georgia, whose entire slate of completely standardized voting machines were programmed and serviced by three corporate contractors working for ES&S, from a garage, over insecure WI-FI setups in 2018, or, post-2020, by one corporate contractor working for Dominion. So much for “decentralization”.
A company that was a subsidiary of the ATM manufacturer Diebold Nixdorf Incorporated. Rebranding as “Premier Election Solutions” in 2006, it was temporarily acquired by ES&S in 2009, increasing its share of the market to ~70%, elevating it to an outright monopoly of the voting system market. After an anti-trust suit by the Department of Justice was filed in 2010, ES&S was made to sell off the defunct company's primary assets, including intellectual property, software, hardware and firmware for current and legacy Diebold voting systems, and all versions of the GEMS election management software. These properties were thereafter bought by Dominion.
Ibid.
https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-123.pdf — “System security should not depend on the secrecy of the implementation or its components.”
https://web.archive.org/web/20080710013226/http://www.elections.state.md.us/pdf/risk_assessment_report.pdf — This study is the same as the SAIC study from above, just heavily redacted.
https://web.archive.org/web/20081108172343if_/http://www.sos.ca.gov/elections/voting_systems/ttbr/diebold.pdf p. 2: “Whereas, the Diebold Red Team members, with access only to the Windows operating system on the Diebold GEMS election management server supplied by Diebold and without requiring access to Diebold source code were able to access the Diebold voting system server software and to corrupt the election management system database, which could result in manipulated voter totals or the inability to read election results, rendering an election impossible to complete electronically;”
Voting machine vendor based in Indianapolis.
A Vancouver, British Columbia-based election vendor that was acquired by Diebold Nixdorf, Inc. in 2002 and reorganized into Diebold Election Systems.
https://jhalderm.com/pub/misc/fsgg-voting-written19.pdf — J. Alex Halderman does not give the subcontractor a name, however, based on the description it can be inferred the identity of the company to be Command Central.
Ibid.
Ibid.
Ibid.
Ibid.
Ibid.
As in, state participation in the EAC's certification program is voluntary. https://www.eac.gov/voting-equipment/system-certification-process
Between 1994 and 2002, VSTLs were nominated and accredited by the National Association of State Election Directors, or NASED.
Wyle Laboratories is a former VSTL headquartered in Huntsville, Alabama that is now defunct. Most of its employees now work at Pro V&V.
https://www.wpr.org/news/sealing-error-vote-tabulation-machines-delay-milwaukee-election-2024 — Absentee ballots were retabulated by the very same tabulator whose network ports were found to be improperly sealed.
Really putting the “voluntary” in Voluntary Voting System Guidelines, huh?
Most “red-team” system vulnerability examinations were conducted before 2010 so newer systems, with the exceptions of the DS200 and ImageCast X, largely escaped the notoriety of older systems like the AccuVote-TS and TSx. Minor companies such as Unisyn avoided this negative attention for reasons related to their obscurity.
Ibid. Section 5.2.8
Ibid. Section 7.3.1
Ibid. Section 7.4.1
Fractionalized voting was already known to some election administrators before its formal description by independent analysts, though they apparently never considered it to be in the public interest to inform voters how their votes may be counted until activists exposed the whole ordeal.
https://whowhatwhy.org/elections/unexpected-russian-traffic-spike-wisconsin-raises-eyebrows/ — Like cybertraffic monitoring, for example.
https://blogs.princeton.edu/citp/wp-content/uploads/sites/952/2021/03/brian-mechler-ESS-exam-report-EVS6110-aug.pdf Section 7.1 — “It was disclosed during the concurrent EVS 6.0.3.0 exam that ES&S personnel have performed the hash verification process instead of their customers.”
Ibid. p. 17 — “[Results Export Program] was developed to meet the U.S. Election Assistance Commission’s 2002 Voting Systems Standards but has not been submitted to a Voting System Testing Laboratory to date. Because Customer is requiring only functional testing of [Results Export Program], [Results Export Program] will not require federal or state certification for Customer Acceptance testing for use in any election in Ohio.”
Ibid. p. 37
https://whowhatwhy.org/elections/ohio-goes-to-court-over-ballot-image-preservation/ — Indeed, the system’s stewards do everything within their power to keep such materials (and all other materials) from ever seeing the light of day. So much for transparency.
Although the voter might interact with them using a push-button interface or keyboard.
https://archive.ph/Qf4Vw — “Once the voter verifies his or her choices, the voter can print the ballot summary card and either have it returned from the front slot or cast into a secure card bin for later tabulation.”
https://web.archive.org/web/20070715020256/http://bocc.cuyahogacounty.us/GSC/pdf/esi_cuyahoga_final.pdf p. 11 — 9.66% of paper audit trails were destroyed, blank, illegible, taped together or otherwise compromised.
Presumably, how these parameters affect voter verification would be quantified using spoilt ballot rates for each of the pseudo-demographics, but the extent to which this would be done is dependent on how much risk the attacker is willing to tolerate.
Provided that these ballots are sometimes in the custody of private companies such as Iron Mountain, one must wonder if, perhaps, the facilities that officials contract out to for maintaining election materials are controlled by the same people hacking elections.
https://www.americanprogress.org/article/election-security-50-states/ provides a more closer inspection from 2018.
The number of ballots cast is important because the difference between that quantity and the sum of all votes cast in the audited race, the undervotes, may or may not exist, and be an artifact of poor or malicious tabulation. Thus it is imperative to audit votes listed as invalid by the machines.
This formula only works if the reported winner won an absolute majority.
https://www.usenix.org/system/files/conference/evtwote12/evtwote12-final27.pdf footnote 9 — Parameters β and t appear to be synonymous.
Table 1 in https://www.stat.berkeley.edu/~stark/Preprints/RLAwhitepaper12.pdf p. 47 demonstrates, however, how their efficiency decays in narrower races.
https://copswiki.org/w/pub/Common/M1938/Four Fatal Flaws of RLA Audits (M1938 2019-12-10).pdf p. 15 — “But here is where they make the big mistake: They would then only report discrepancies with the new computer report [the second machine count generated after hand counting the ballot batch for error troubleshooting purposes], which would always match perfectly, thereby effectively covering up the original discrepancy.”
This specifically deals with auditors in Los Angeles County, California, but there is reason to be suspect of audits in other states.
The auditing statute codified in The Rules and Regulations of the State of Georgia and the Official Code of Georgia Annotated contradict each other in key aspects, but I will rely on the former since its regulations are more pertinent to the practice.
Transcluded from https://arxiv.org/pdf/2408.00055
https://archive.ph/CyXpH — Report detailing duplicated entries and miscounts.
https://www.grc.com/sn/sn-215.pdf — The Arrogance Maxim: The ease of defeating a security device or system is proportional to how confident/arrogant the designer, manufacturer, or user is about it, and how often they use words like “impossible”, as in “impossible to crack”, or “tamper-proof.”
Election vendor based in Vista, California.
The clause reads “no contested race shall be selected to receive a risk-limiting audit if the tabulation of the unofficial result for the contested race shows a difference of not more than one percent of the total vote cast for the top two candidates.”, which might be construed as meaning that only races with a margin of less than 1% can be audited. However, since elections with margins over 1% have been audited, its fair to assume that this interpretation would be incorrect.
Regularly scheduled nonpartisan municipal and county local elections.
There's also the implication that, if low-propensity voters are hypothesized to review their ballots less often, then a hacked BMD, equipped with a modem of WIFI memory card and communicating with the e-poll book, can opt to steal votes from signed-in voters who are labeled, by the rigger’s database, as being “low-propensity”.
Thanks for writing this, it clarifies a lot. Your analysis of electoral systems vulnerabilities and polotical cynicism is quite astute. I wonder, what robust, scalable tech or policy solutions do you envision to mitigate these systemic risks, especially with global digitization trends? Excellent piece.